The IBM “Internet of Things” really started in 1933 Nazi Germany with massive abuses of privacy, property & genocide
C.I.A. employed hundreds of Nazi scientists in mass mind control research
C.I.A. refined AGITPROP (agitation propaganda) now being used to demonize & undermine President Trump
Editorial, Sep. 03, 2017: He Fights
This is an important perspective on why the average, non-elitist American supports President Donald J. Trump and strongly rejects MSM (should be renamed C.I.A. Mind Control Media (MCM)) and its breathless, dishonest, Alinsky attempts to prevent their choice for President from doing the job we sent him to Washington to do. Evan Sayet. (Sep. 02, 2017). HE FIGHTS. Townhall. We fight. MSM must be defeated.
In 2013, a DARPA (Defense Advanced Research Projects Agency) whistleblower revealed to fellow scientists an active C.I.A. mind control project that targeted Christianity and Islam. The documents were just uncovered by an AFI researcher. The secret government program sought to induce and disrupt religious "narratives" with desired propaganda. This project (lead: Steven R. Corman PhD) entered its implementation Phase III in the run up to the 2016 election. The Arizona State project leaders are experts in social media and received $6.1 million to develop actionable strategies to disrupt "master narratives" (like a person's Christian or Islamic beliefs) in the name of, naturally, controlling extremism. [Editor: The opposite is also true: one learns how to incite extremism also.] The program focused on finding trigger words and phrases that provoked desired emotional responses by using words in lieu of magnetic resonance pulses to the brain—irrespective of the truth or proper context of the information (aka "virtue signalling"). For example, "Crusades" emotionally triggers some Moslems, as does "jihad" for some Christians. Considering the inordinate number of times Hillary Clinton repeated it, an effective Corman-inspired (?) fake news propaganda trigger tied to candidate Donald Trump was evidently "p_ssy" and "(bent wrist) duhhh," among others. See Anonymous. (Jan. 29, 2013). (4.5 MB) Whistleblower Reveals Military Mind Control Project BAA 12-03 ASU 12040772 at Arizona State University—secret DARPA Mind Control Project Revealed. See esp. researcher concerns (including the whistleblower) about possible accusations, page 8: "This project is aimed at creating bad technologies like mind control, a narrative ray gun."
ORIGINAL POST
(Aug. 24, 2017)—America’s founder John Adams said that property and privacy were “inviolable precepts” if we are to be a free people.
America's Founders believed that a free people could not tolerate a government that confiscated personal property and rummaged through personal effects capriciously.
A rogue C.I.A.-controlled federal bureaucracy is currently engaged in AGITPROP (Agitation Propaganda) using invasion of privacy by warrantless surveillance and confiscation of property through regulatory abuse.
AGITPROP uses state-controlled news, arts and entertainment to demonize a target before taking him or her out (e.g., assassination, “car accident,” “suicide,” “plane crash,” coercion, blackmail, regime change, firing, resignation). By the time that happens, the public has become so dumbed down and fatigued by the lies and misinformation that they don’t protect the victim.
Bookmark: #agitprop-failing | https://tinyurl.com/y9twk6qlAgitprop: failing propaganda weapon? The boy who cried wolf?
AGITPROP has worked. It has numerous successes like 9/11, the Adolf Hitler, Arab Spring, Afghanistan, Bolshevik Revolution, Bundy Standoff, Gulf of Tonkin, Iraq, ISIS, Kosovo, Kristallnacht, Lewinsky Affair, Libya, Oklahoma City Bombing, Ruby Ridge, Rwanda, Sheriff Joe Arpaio, Syria, Vietnam Antiwar protests, Waco, Watergate, World Trade Center. However, now it has devolved further into the abyss with historically illiterate air head accusations like Bolshevik!, Conspiracy Theorist! Dangerous!, David Duke!, Dead!, Demogogue!, Deranged!, Distrubing!, Dying!, Erratic!, Fascist!, Fearmonger!, Fringe!, Garbage!, Groper!, Grotesque!, Homophobe!, KKK!, Lord Voldemort!, Mental!, Monstrous!, Muddled!, Mussolini!, Mysogynist!, Nazi!, Neo-Nazi!, Nut Job!, Pathological!, Putin's Puppet!, Rasict!, Russian Agent!, Scary!, Sexist!, Swindler!, Tax Cheat!, Uncle Tom!, Unfit!, Unhinged!, Vulgar!, What-e-v-e-r Triggers a Snowflake!, White Nationalist!, White Supremecist!, Womanizer!, Wrecking Ball!, Xenophobe!, Astroturfing (fake grassroots comments on blogs) and WHATEVER FOOLS THE UNTHINKING, UNINFORMED AND UNSUSPECTING “MASSES.”
Advertisers and the C.I.A. have known about the effectiveness of immoral “virtue signaling” to trigger the unthinking masses with fabrications for many decades. Given the way these misanthropes have hurled every adjective in the dictionary against President Donald J. Trump, we can only hope and pray that we may finally be seeing the DEATH OF AGITPROP as an effective weapon of propaganda.
Given the lack of an uprising in the general American public to protect their privacy and property from the rogue C.I.A.'s warrantless surveillance and property confiscations through regulatory abuse, we can only conclude that, we are actually no longer a free people as we were in our parents' generation.
Bookmark: #chandler-ibm-wolves | https://tinyurl.com/y9cvzg6jThe question is: Will we wake up before it is too late?

James P. Chandler & IBM —wolves in sheep’s clothing
Michael McKibben and Leader Technologies—the true inventors of social networking—discovered that their former patent attorney, James P. Chandler, III, and his client IBM are wolves in sheep’s clothing.
McKibben said, “Chandler was recommended to us by Maj. Gen. James E. Freeze (US Army ret.), the former #3 at the NSA. Freeze was our first outside company director in 2000. After meeting Chandler in Washington, D.C., just a few blocks from the White House, we engaged Chandler as our patent lawyer and second outside director. We naturally expected him to honor his Constitutional duty and protect our invention. Sadly, he personally stole it.”
“What was so important about our invention that Chandler sacrificed his integrity and honor to steal it? Now we know. Chandler's world of rogue C.I.A. spies wanted our social networking platform to spy on the planet, while making lots of money for themselves and their friends.”
Bookmark: #social-networks-spy | https://tinyurl.com/y7akezgqChandler & IBM use social networking to spy on everyone
“To our horror, we have discovered that Chandler not only stole and distributed our invention through IBM, but they now use it to violate the privacy and property rights of EVERY American,” McKibben explained.
Chandler and IBM created several organizations to carry out their subversion under Clinton, Bush Jr. and Obama, including:
- National Infrastructure Advisory Council (NIAC) (with a permanent IBM/Cisco/C.I.A. agent—Thomas E. Noonan),
- National Security Staff (NSS) / Joint Special Operations Command (JSOC), and
- IBM Eclipse Foundation
According to former secretary of defense Robert M. Gates in Duty (2014), the NSS at the White House mushroomed from 50 people under Clinton to 350 under Obama. And yet, even the FBI says not a single terrorist has been caught as a result of all this spying. However, the WikiLeaks Podesta revelations reveal that the Deep State has made extensive use of these spy databases for blackmail and for covering up widespread Satanism, child sex trafficking and pedophilia among these elitists.
See Jenna McLaughlin. (Nov. 17, 2015). “U.S. mass surveillance has no record of thwarting large terror attacks.” The Intercept; See also FBI Special Agent-in-Charge Ted L. Gunderson. (May 12, 2005). CIA, FBI Deep State shadow government operates “a rogue criminal enterprise within the government” to compromise Congress “through sex and drugs” blackmail.
Bookmark: #why-care | https://tinyurl.com/ycaf45xyWhy should you care if the gov't collects all of your personal information?
McKibben continued, “For example, take your personal family photos. Behind the scenes, the social sites run facial recognition programs on everyone in all your photos. Then, they store that “linking relationship” information in your “Dark Profiles.” In other words, even those who are not on Facebook are being secretly catalogued—adults and children alike—just like the Nazis catalogued Jews and other undesirable citizens in Germany on IBM computers. Their fate is infamously known, may God rest their souls.”
According to Edwin Black, author of IBM and the Holocaust: The Strategic Alliance between Nazi Germany and America's Most Powerful Corporation, we now know the numerical categories of each of Hitler’s “unacceptables.”
Bookmark: #ibm-and-the-nazi-holocaust | https://tinyurl.com/y8c82vqoFurther References:
S. Hrg. MKUltra. (Aug. 03, 1977). CIA's Program Of Research In Behavioral Modification. Senate Subcommittee on Human Resources. 95th Congress, First Session. Stock No. 052-070-04357-1. GPO.
Karl Sie. (May 13, 2011). Hitler’s Mind Control Experiments and How They Influenced Modern Propaganda. Subversify Viral.
Nazi Disclosures. (Oct. 01, 1999). Implementation of the Nazi War Crimes Disclosure Act. Nazi War Criminal Records Interagency Working Group, October 1999. An Interim Report to Congress. National Archives.
Bookmark: #bernstein-msm-cia | https://tinyurl.com/bernstein-msm-cia

New! Aug. 29, 2017: Carl Bernstein. (2007). THE CIA AND THE MEDIA—How America's Most Powerful News Media [MSM] Worked Hand in Glove with the Central Intelligence Agency and Why the Church Committee Covered It Up. CarlBernstein.com. (“the New York Times provided cover for about ten CIA operatives . . . Many signed secrecy agrements . . . some signed employment contracts . . . 'The secrecy agreement was the sort of ritual that got you into the tabernacle. After that you had to play by the rules.' . . . separating the American press corps and government was often indistinguishable . . . journalists were put 'on a string' [of control] . . . at least 200 journalists signed secrecy agreements or employment contracts with the Agency in the past twenty-five years.” Mexican telecom tycoon Carlos Slim—the world's richest man—now owns the New York Times and is the largest single donor to The Clinton Foundation.) Rogue C.I.A. agents? Most assuredly.
“There are no alumni in the CIA. Once a CIA agent, always a CIA agent.” Former FBI Agent-in-Charge (Memphis, Dallas, Los Angeles) Ted L. Gunderson. (Apr. 02, 2005). Open Letter to Barbara Cartwell. Educate Yourself. See also Ted l. Gunderson. AFI Timeline.
IBM and rogue C.I.A. use social media to catalog citizens in ways many times more effective than the Nazis
Once your personal data is collected, spies then use a Raytheon program named RIOT to find more linking relationships across all social platforms, Facebook, Google, YouTube, WhatsApp, Instagram, Yahoo, Hotmail, MSN, Outlook 360, LinkedIn, Gmail, Yahoo Mail, Facebook Mail, Facebook Messenger, AOL, etc. All of that information is stored in your Dark Profile.
Bookmark: #raytheon-riot | https://tinyurl.com/y7a3qlbyLeader’s fight is our Republic’s fight

McKibben asked, “Is it just a coincidence that the same IBM that catalogued Jews and other politically undesirable segments of the European population in WWII is using social networking to illegally catalog all Americans in 2017?”
“Why are we so blindly revealing all our friends and work connections through Facebook, Google, LinkedIn, Instagram, What's App, etc.? These people are stealing your privacy. Your privacy is much more valuable to you as a citizen in our Republic than your car or belongings.”
“This rogue C.I.A. is softening the citizenry up for the kill in my opinion . . . so far we've let them get away with it without consequence.”
“Is it just a coincidence that both Hitler and Hillary Clinton considered the citizens who disagreed with them ‘unacceptable’ i.e., ‘deplorable’ and ‘irredeemable’ and not worthy of respect?”
IBM Thomas Watson (C)

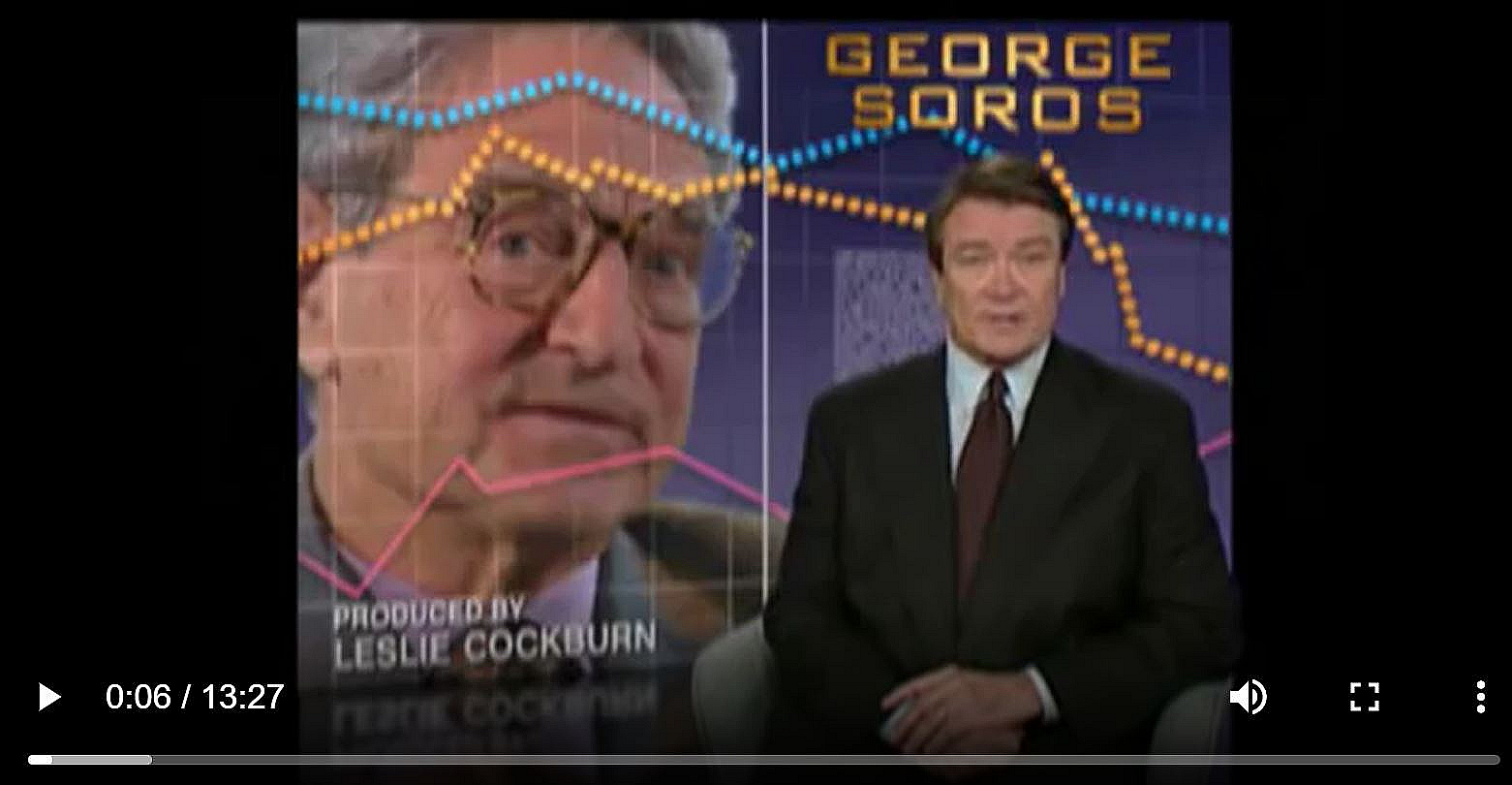
The truth is that IBM and the C.I.A. profited from (and continue to profit from) the blood of the innocents. See video, Fig. 2.
See Donald W. McCormick, James Curtis Spee. (Dec. 01, 2008). IBM and Germany 1922-1941. Organization Management Journal.
“What are they using this information for? Are they using it for our welfare? The answer is obviously not.”
“One principle is certain: The collection and use of this information destroys our Constitutional rights to privacy and property. When our government reaches into our homes, businesses and thoughts and steals whatever it wants, we are not free.“
“Jesus Christ said you will know what's in a person’s heart by observing his or her actions. Therefore, we can see from the greedy, selfish and power mongering actions of these people that their hearts are empty of love for their fellow human beings. Instead, they lie, cheat and steal without remorse. They see us as little more than consuming animals who pollute their air with too much carbon dioxide,” said McKibben.
Bookmark: #agitprop | https://tinyurl.com/y8vpwncc“AGITPROP” demonizes opponents before taking them down
At the end of WWII, the newly-formed C.I.A. co-opted some 1,600 Nazi scientists, brought them to the U.S. and allowed them to continue their research. Some of them had worked on a Soviet mass mind control technique called AGITPROP (Agitation Propaganda).
AGITPROP stages events with messages reinforced by media, news, films, literature, plays, pamphlets and other art forms to demonize opponents and condition the general population for an eventual crackdown on those opponents.
Kristallnacht (Night of Broken Glass) on Nov. 9-10, 1938 in Germany is a prime example. 7,000 Jewish businesses were confiscated (including the business and home of the family of an AFI editor), and 1,000 synagogues were burned. The German populace was largely silent. Hitler then ratcheted up this persecution that eventually led to 6,000,000 Jews killed in the "Final Solution" extermination camps. The property and privacy of the minority German Jewish population was ignored, along with those of Jehovah's Witnesses, Poles, gypsies, homosexuals, clergy, etc.
Bookmark: #cia-exploits-nazi-mind-control | https://tinyurl.com/yb28xr9mC.I.A. hired over 330 Nazi Party mind control experts
The Bluebird Report to Congress (1999) revealed that:
“Between 1945 and 1955, 765 scientists, engineers, and technicians were brought to the United States under Overcast, Paperclip, and similar programs. It has been estimated that at least half, and perhaps as many as 80 percent, of the imported specialists were former Nazi Party members.”
The rationale for bringing these scientists to the U.S. was to prevent them from working for the Soviets, Chinese or North Koreans. Some of these people had conducted murderous experiments on human subjects in concentration camps and were prosecuted as war criminals at the Nuremberg Trials. For example, Arthur Rudolph persecuted slave labor in the underground V-2 Nordhausen Concentration Camp in Germany, where thousands of prisoners died.
The CIA started in 1947 and exploited these scientists under various mind control programs including CHATTER, PAPERCLIP, OVERCASE, BLUEBIRD, ARTICHOKE, MKULTRA, MKNAOMI, MKDELTA, MKOFTEN MKCHICKWIT, MKSEARCH and Operation Midnight Climax (yes, even targeting San Francisco brothels!).
Bookmark: #beware-spymasters-bearing-gifts | https://tinyurl.com/ycrne85mBeware the C.I.A. spymaster promoting a business opportunity
McKibben said, “Even after we met Chandler, we never gave him a full copy of our programming source code, which is the Holy Grail of any program. We had protected it so well that one former U.S. intelligence asset called us a ‘hard target,’ meaning our security was virtually impenetrable.”
“After dragging his feet for several years after promising to bring us business prospects, Chandler suddenly one day brought us what appeared to be a ready-made business opportunity through his friends at Lawrence Livermore National Laboratory (LLNL).”
“They wanted us to test our new social networking technology with LLNL’s perimeter security cameras. The system passed with flying colors and was certified for use with Defense-grade encryption. Shockingly for us, after that our business prospect base just dried up, almost overnight.”
“Hindsight says we should have been wary of Chandler’s LLNL introduction. It was a Deep State set up. Chandler produced a 72-page LLNL license agreement. Tellingly, he wrote himself into the agreement so that he would hold a copy of the source code in a custody agreement for 'legal safekeeping.'
“The LLNL co-signer was Jeffrey Wadsworth, who we had never met, but soon thereafter appointed CEO of the Battelle Memorial Institute and president of the Ohio State Trustees—even though he is British with no Ohio loyalties. Ohio State then teamed up with IBM and John Kasich and moved the Ohio State data center off campus where it became the network hub for the national university equivalent of Common Core called 'Massive Open Online Course.'”
“Source code custody agreements are not uncommon in software. We actually thought we would be more protected since Chandler was our attorney.”
“On June 06, 2002, we provided Chandler with an encrypted CD-ROM containing $10 million worth and 650,000 lines of source code written with 145,000 man-hours of programming.”
“On Aug. 29, 2002, eleven weeks later, the IBM Eclipse Foundation distributed our invention to all Eclipse members as Version 2.0.1. They had to wait another year for us to finish debugging that source code, which occurred on Oct. 28, 2003.
Magically, that’s the same night Mark E. Zuckerberg, who AFI researchers now believe to be a C.I.A. asset, hacked the House sites at Harvard to steal student photos and wrote in his online diary, “Let the hacking begin.”
Bookmark: #property-privacy-contract-abuses | https://tinyurl.com/ybwq3jh3Property, privacy, contract abuses
McKibben says, “Our property was stolen. That property is being used to invade the privacy of billions of human beings on the planet.”
“Our patent contracts have not been honored. How much worse can the federal government’s conduct get? When King George sent soldiers into the homes of Boston arbitrarily and without notice, he provoked an uprising we now call the American Revolution.”
Bookmark: #obama-promoted-nazi-ibm | https://tinyurl.com/y8b5rd5a
Read more at AFI. (Feb. 11, 2016). Obama promotes IBM criminality in latest executive order. Americans For Innovation.
“We appeal to real Americans to come to our aid. We have filed a Miller Act Notice. We have put President Trump’s White House on notice that his predecessors abused our property and we don’t ask or beg, we demand that our government pay us for this theft of our invention property for which the government has even signed multiple patent contracts and has enjoyed the benefits since 2000 without compensation, other than during Katrina.”
“Our claims are actually even stronger. Thanks to corruption watchdogs Judicial Watch and Citizens United, we discovered secret contracts between Hillary Clinton while Secretary of State and Facebook. Starting on Sep. 26, 2009, Hillary used State Department funds to hire Facebook to build election rigging software. Besides interfering in the election process, Hillary obstructed justice since we were suing Facebook at the time.”
“We can show that Barack Obama obstructed justice by raising money and sending propaganda through 'Obama for America' using our invention.”
“We can show that the Patent Office and former IBMer David J. Kappos and Patent Office director obstructed justice by setting up a Facebook page while we pursued our lawsuit with Facebook.”
“All the judges in our Facebook lawsuit held substantial Facebook financial interests in flagrant violation of the Code of Conduct for U.S. Judges to avoid even the appearance of impropriety.”
“There's more, but I'll stop there.”
Bookmark: #property-is-liberty-plus-creativity | https://tinyurl.com/y8kubd3qPersonal property = Liberty + Creativity
McKibben emphasizes, “My property is the use of my God-given liberty to create something of value and own it.”
“My Privacy is the right to enjoy my liberty without unlawful government interference. “
“A patent is a contract between an inventor and the American people.”
“My property right is crystal clear. I entered into contracts with the federal government that resulted in multiple patents. The government loved my inventions so much they stole them right off the design storyboards, even before they were fully functional! In addition, my patent attorney was an agent (albeit a secret spymaster) of the federal government as well. We also had five letters of engagement with him as an attorney.”
Bookmark: #scene-of-the-chandler-crime | https://tinyurl.com/y96bnnng
“In fact, patents are the only property rights actually written into the U.S. Constitution. Article I, Section 8, Clause 8 ('[The Congress shall have power] To promote the progress of science and useful arts, by securing for limited times to authors and inventors the exclusive right to their respective writings and discoveries.')”
“Clearly the Deep State ignores patent property rights, when it suits them. As a result, the legal sophistry that we have encountered is off the charts corrupt.”
“My shareholders and I have been denied all three of these fundamental Constitutional rights: property, privacy, contract.”
McKibben said, “In our case, the federal government marched in with jack boots and just confiscated our social networking invention ‘for the greater good.’ Those were the very words of my patent attorney James P. Chandler to me once. AND THEN, THEY USED THE INVENTION AGAINST US ALL.”
Bookmark: #wouldnt-you-expect-payment | https://tinyurl.com/yam2zg38If you did the work, wouldn’t you expect payment ???!!!
Ask yourself, if you had spent five years, $10 million and invested 145,000 man-hours into building something, wouldn’t you expect to be paid by anyone who used what you built?
Exactly. Well, so do social networking inventor Michael McKibben and his stockholders in Leader Technologies.
Worse, the federal government is using Leader’s invention as a global spy machine to engage in “Collect it All” warrantless surveillance on everyone.
This theft is wrong on so many levels.
We call upon all real Americans to speak up for Leader’s property rights, as well as the privacy rights of every American—it's that important, for all of us.
Hopefully, the age of CIA-IBM-Deep State mind control is coming to an end.
Taking care of real inventors like Michael McKibben and Leader Technologies is a good first step.
Support the Leader Technologies / Michael McKibben Miller Act Notice. Ask President Trump to take care of these American entrepreneurs like he promises.
* * *
Bookmark: #resources | https://tinyurl.com/ycndh7qdResources:
Bookmark: #kevin-shipp-exposes-shadow-government | https://tinyurl.com/ybc9f2o6C.I.A. Whistleblower Kevin Shipp calls for social-civil revolution against the Shadow Government to restore the Constitution
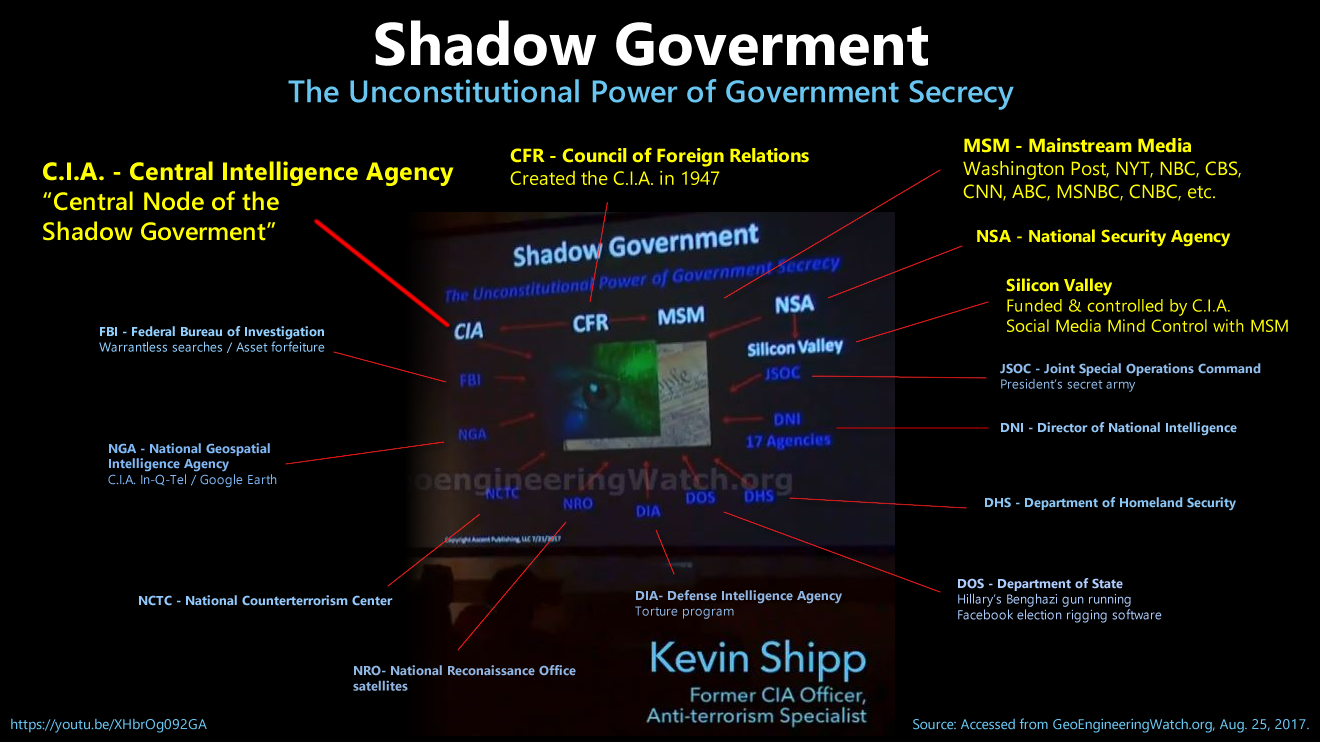
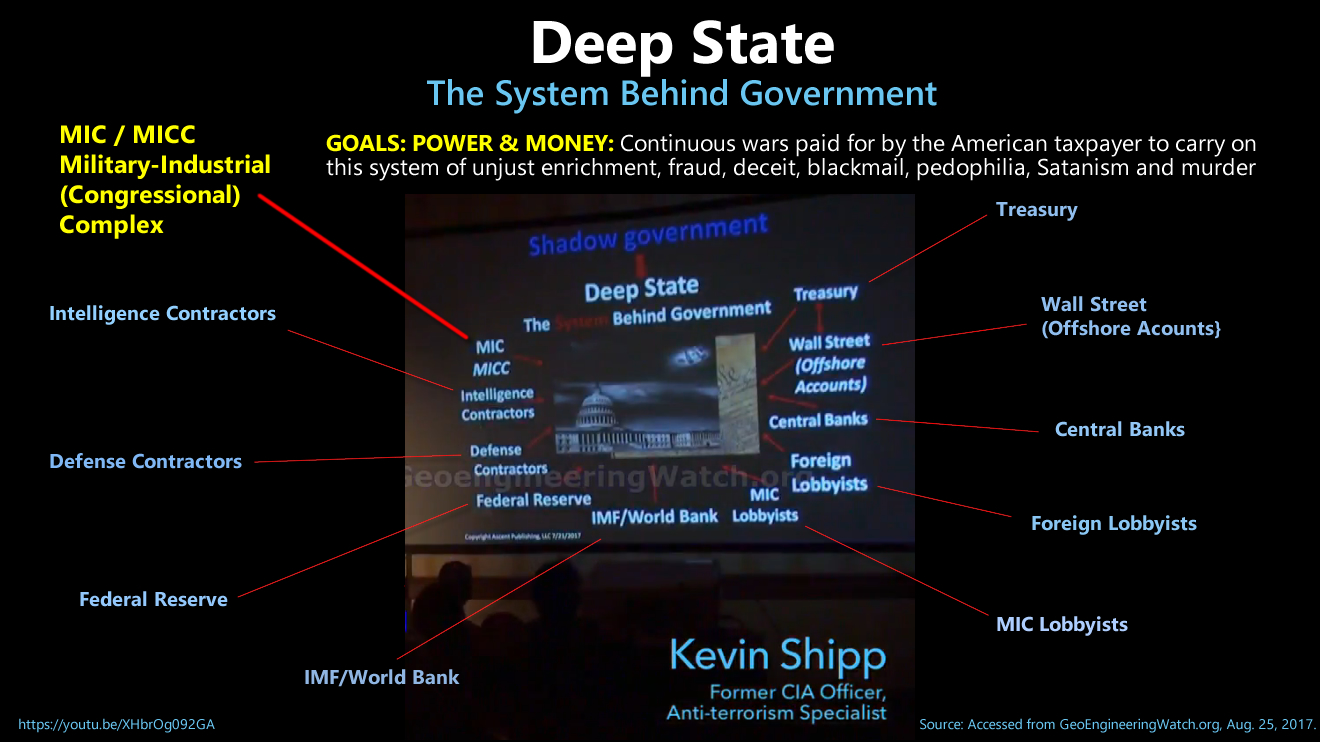
Warning: C.I.A. Deep State with IBM are close to a full takeover

Notices: This post may contain opinion. As with all opinion, it should not be relied upon without independent verification. Think for yourself. Photos used are for educational purposes only and were obtained from public sources. No claims whatsoever are made to any photo.
Comment
Click "N comments:" on the line just below this instruction to comment on this post. Alternatively, send an email with your comment to amer4innov@gmail.com and we'll post it for you. We welcome and encourage anonymous comments, especially from whisteblowers.

 e.g. "IBM Eclipse Foundation" or "racketeering"
e.g. "IBM Eclipse Foundation" or "racketeering"