Return to return to the beginning of this post.
With these encryption keys, nothing in our digital lives is off limits to the Clinton's and their conspirators
President Trump’s new executive order can be sabotaged with these keys; alternatively, he can use the order to prosecute these criminals
Many foreign powers have conspired with the SES and their Queen’s Privy Council overlords since before 1993

1999 | 2000 | 2001 | 2002 | 8-K. FBI Contract Press Release (Oct. 29, 2003) | Jones' Stock Options (Dec. 05, 2003) | 2003 | Co. Overview (2003) | Jones' Signature (Dec. 23, 2003) | Jones' Bio (Mar. 15, 2004) | 2005 | 2006 | 2007 | 2008 | 2009 | 2009A | Relationships (1998-2009)
AFI (Nov. 06, 2015). Complicit encryption geeks enable the American spy state. Americans for Innovation.
AFI (Nov. 25, 2015). Dell and Lenovo (IBM) ship computers with spy state backdoors. Americans for Innovation.
https://youtu.be/-zWWJ1BzKgI | (Raw *.mp4 video file—use if the YouTube version is censored).
SPECIAL NOTICE: This post is a work in progress. You are encouraged to return to pick up additional evidence as it is added. Indictable evidence continues to pour in for use by prosecutors, alternative media, Treasury, U.S. Marshalls and military tribunals. These criminals have relied on the fact that encryption, cryptography and cryptanalysis is a field of esoteric mathematics for which the average person has little interest. Hopefully, that will now change.
Cryptography—the use of codes and ciphers to protect secrets—began thousands of years ago. Until recent decades, it has been the story of what might be called classic cryptography — that is, of methods of encryption that use pen and paper, or perhaps simple mechanical aids. In the early 20th century, the invention of complex mechanical and electromechanical machines, such as the Enigma rotor machine, provided more sophisticated and efficient means of encryption; and the subsequent introduction of electronics and computing has allowed elaborate schemes of still greater complexity, most of which are entirely unsuited to pen and paper.
In a simple form, simply scrambling the letters in a word is a basic form of cryptography. HELLO might become OLHEL or LEHLO. In more sophisticated approaches, look up tables contain readable words in the first column and a replacement word in the second. The resulting message looks like jibberish until the look up table is used by the recipient. The public key infrastructure and certificate authorities discussed in this post are simply more scrambled forms of encryption.
The earliest example known was from an Egyptian scribe about 1900 BC. Assyrian merchants used a form of encryption called intaglio in 1500 BC. Hebrew scribes wrote a copy of the Book of Jeremiah in a substitution cipher in 605 BC. In 487 BC the Greeks used a "skytale" to encrypt important messages. Julius Caesar (100-44 BC) encrypted government communications. Abu ' Abd al-Rahman al-Khalil ibn Ahmad ibn Amr ibn Tammam al Farahidi al-Zadi al Yahmadi wrote a book on cryptography in 725-790 AD. Thomas Jefferson invented a wheel cipher. Tellingly, a design in 1976 by IBM based on "the Lucifer cipher" is now used and called "triple-DES" (the Triple Data Encryption Algorithm).
When the German Enigma Machine was cracked in World War II, the Allies could read ALL German communications from that point forward. In the same way, Hillary's access to the PKI, Dual_EC_DRBG algorithm and Certificate Authorities gives her access to The Internet of Things' version of the Enigma Machine break, which was considered by western Supreme Allied Commander Dwight D. Eisenhower to have been "decisive" to the Allied victory. See History of Encryption.
(Sep. 16, 2018)—Imagine that your identity is stolen suddenly.
Your healthcare, education, police, employment and bank records are all altered overnight to make you look like an embezzler. Imagine you are jolted awake the following morning by the police bashing in your door to arrest you. Imagine that the local TV is already carrying news of your arrest using a drunken party photo of you off your phone.
Imagine further that you are Hillary Clinton. You need for 55,000 Clinton Foundation emails on FBI director James Comey computer to disappear. Poof. They’re wiped without a trace.
Imagine still further that you are Lord Mark Malloch-Brown from the Queen’s Privy Council. You need to erase the U.S. Department of Treasury’s new evidence of foreign meddling embedded in your Smartmatic voting machines. Your bunk buddy George Soros makes a call to Hillary. Poof. This evidence is digitally wiped, without a trace.
This cannot happen in America you say? Think again.
Since these people have full backdoor access to any computer or phone on the Internet, can they ever be caught? Yes, once we realize how they do it. That method has just been discovered.
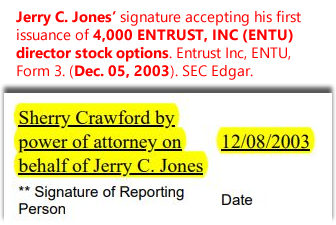
Truth is, Hillary Clinton literally has access to every computer on the Internet through a company named ENTRUST. Her 19-year Rose Law Firm partner Jerry C. Jones directs the company (now ostensibly run by a Silicon Valley dude named Orlando Bravo and his private equity firm Thoma Bravo, LLC), and has done since Dec. 2003. Entrust issues the encryption keys for most major governments and companies in the world.
Bookmark: #hillary-jones-acxiom | https://tinyurl.com/ya8u98awWhere did Hillary send Jerry C. Jones after she took control of ENTRUST? Acxiom (Little Rock, AR)—a carbon copy of Cambridge Analytica & SCL Limited (Sir Geoffrey E. Pattie)
The Securities & Exchange Commission records reveals that at the same time Jerry C. Jones secretly became a director of ENTRUST, Inc., he also became a director of Acxiom Corp—a data analytics firm that appears to be a carbon copy of Cambridge Analytica and SCL Limited in the UK owned by the Queen's Privy Counsellor in charge of mass surveillance, Sir Geoffrey E. Pattie. See for yourself. Here is a PDF of the SEC filings. Here is an Excel spreadsheet showing the bevy of me-too beta-males and females who feed off of the Clintons and the SES in Little Rock, Arkansas.
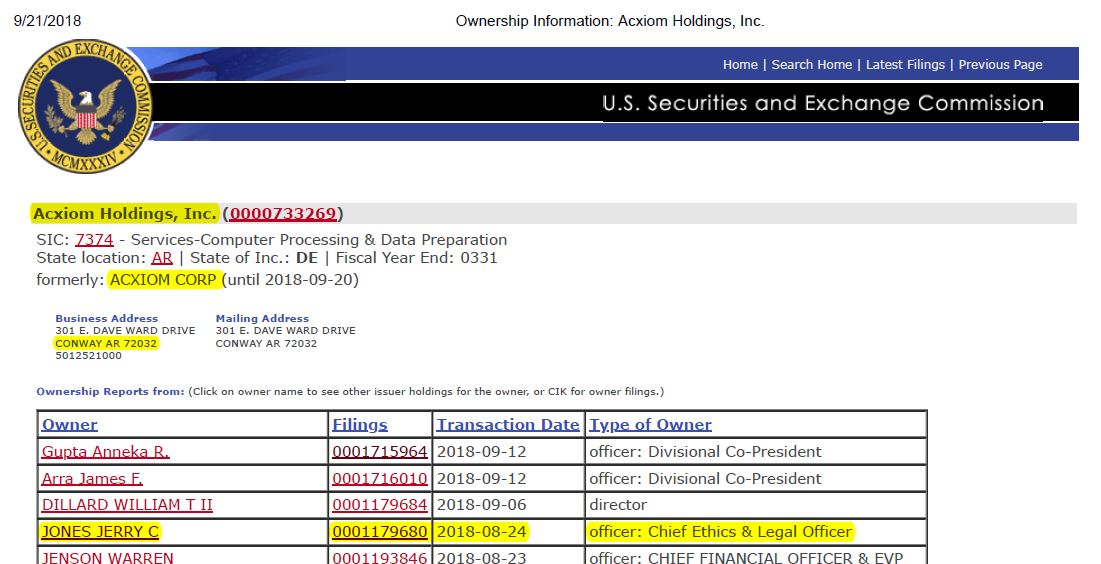

Fig. 6—Douglas Gabriel, Michael McKibben. (Sep. 28, 2018). We are at war with China. American Intelligence Media, Americans for Innovation.| (Raw *.mp4 video file).
See also Staff. (Sep. 28, 2018). ACXIOM (owned by C.I.A.-led Blackrock, controlled by Hillary) moving “data onboarding” operation from Little Rock, AR to China. Patriots4Truth.

What is an encryption key why is this discovery so devastating to the Deep State shadow government?
Put simply, encryption keys are used on both the sender’s and receiver’s computers to send data. It takes two keys to make a connection to send or receive data. The Clinton Administration created “trusted Certificate Authorities (CA)” to check with to make sure that the two keys are the real sender and receiver. If your keys are not approved by the CA, your connection will be blocked. In the hands of tyrannical globalists like Hillary Clinton, Barack Obama, George Soros, Eric Schmidt and Robert Mueller, this will be the new censorship on the Internet.
Bookmark: #what-are-encryption-keys | https://tinyurl.com/ybkforoz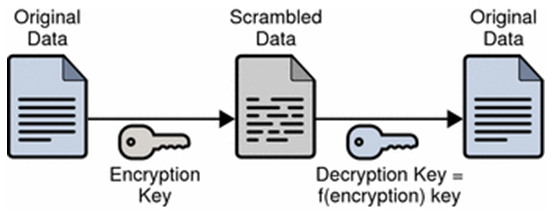
Encryption scrambles the contents of your messages then files and unscrambles them once they reach their intended destinations using digital keys managed by encryption engineers.
For example, the phrase “your cancer treatment program” would be encrypted with a digital key and travel through the Internet as “Qij\aq6NB5Lf@;kndFq7CN{Q{." So, even if it was intercepted it could not be read. The theory is that this knowledge of your medical condition would remain confidential between you and your doctor. Not so for Hillary, she would see you have cancer and could use that information for blackmail, extortion or murder, whatever worked for her.
These CA’s make a big deal in their propaganda that you can “trust” them not to use or spoof your identity to get access to data that you and they are not authorized to have. That is a boldface lie. No wonder these people have the countenances of criminals. They are, and they know it.
Suppose you are the CA who issues keys to the FBI. Suppose you want to see the evidence being gathered against you in an investigation.
All you have to do is “borrow” the FBI key from Hillary or ENTRUST. Then you can connect to the target FBI computer using a bogus key created for you by ENTRUST, and voile! You then have two “trusted” keys so the FBI computers let you in. There are technical nuances to this description, but basically, you can do what you want with these keys. Don't let trollers try to baffle you with techno-jargon to throw your dogs off the scent. Lucifer (literally, IBM Triple-DES) is in these encryption details.
Hillary Clinton has this level of access to practically all data on the planet, including the FBI, NSA, Departments of State, Commerce, Energy, Treasury, GSA, Patent Office, Post Office, NIST, as well as numerous foreign government and commercial entities. See ENTRUST 10-K Annual Reports (1998-2009). SEC Edgar.
Now that we finally know how the Clinton's stay one step ahead of the sheriff, we can now stop them.
More hard proof that Hillary Clinton is a digital monster
In this post, we will prove without a doubt how Hillary Clinton cleverly wormed her way into full access and control for 50,000 FBI encryption keys.
They are likely managing this empire from Obama’s Google-constructed U.S. Digital Service bunker three blocks from the White House manned by Valerie Jarrett and Eric Holder.
We admit that these findings sound more like Grisham fiction. But the evidence is a pesky thing. The evidence is now pouring out.
The evidence provided is “judicially recognizable” and indictable, we believe
“Notoriously public” information, like the U.S. Securities & Exchange Commission filings that we cite, is evidence that requires no further verification to be used in litigation, hence the adjective “notoriously.” This means that the information is so publicly noteworthy that further proof of validity is unnecessary. For example, John F. Kennedy was assassinated in 1963. That is a notoriously public fact and no proof is needed.
Notoriously public facts, like SEC filings, are “judicially recognizable” and can be accepted as truthful since the submitter attests to the SEC that they are true. It is criminal fraud to lie intentionally in SEC filings.
TIMELINE: Bill & Hillary Clinton began orchestrating unfettered access to the FBI’s encryption keys in 1993
On Jun. 07, 1993, the new Clinton Administration convened the “Third CPSR Cryptography and Privacy Conference (CPSR - Computer Professionals For Social Responsibility).”
The conference was held two days before an important Jun. 09, 1993 House hearing on "encryption and telecommunications network security." The conference gathered over 106 attendees representing government, politics, commerce, manufacturing, industry, media, technology, telecommunications, healthcare, banking, education, faith and accounting. That’s plenty of arm-twisting, even for Washington, D.C.
The meeting sponsor was globalist advocate Carnegie Endowment for International Peace.
The hosts included:
(1) James P. Chandler, III, George Washington University intellectual property and national security law professor, and later patent attorney for social networking inventor Leader Technologies, Inc. (Jan. 2000);
2) John D. Podesta, chief of staff and campaign manager to Bill Clinton, Barack Obama and Hillary Clinton; and
(3) Stephen D. Crocker, founding member of the illegal public-private conspiracy group Highland’s Forum/Group (Feb. 1995), then Barack Obama’s director of ICANN (Internet Corporation for Assigned Names and Numbers) who ceded control to the UN on Oct. 01, 2016—one month before Donald J. Trump was elected president.
Hillary hid the 1993 encryption meeting attendee list
The information about this meeting was hidden on Hillary’s private email server. It was unearthed by corruption watchdog Judicial Watch after they pressed the State Department in court to release the document.
Bookmark: #clinton-fbi-encryption-scam-begins | https://tinyurl.com/ybpflzqn
James P. Chandler, III, John D. Podesta. (Jun. 07, 1993). Third CPSR Cryptography and Privacy Conference, included Stephen D. Crocker, John D. Podesta, James P. Chandler, III, Ann Harkins, Ken Mendelson (Stroz Friedberg), Juan Osuna, Cathy Russell, Steven Wolff, IBM, HP, AT&T. FOIA No. 9403963. U.S. Dept. of State. Note: This PDF file contains a spreadsheet of the attendees (click on the paper clip inside the PDF).
In 1993-1994, more than 20 people close to or investigating Clinton corruption died under suspicious circumstances.
Theft & Weaponization of U.S. inventions
In Feb. 1995, the Highlands Forum/Group was formed. It was and is a highly illegal private “public-private” meeting sponsored by the Department of Defense Net Assessment group run by Senior Executive Service (SES) members Richard P. O'Neill and Andrew W. Marshall. See also AFI. (Nov. 22, 2017). The Weaponization of Social Media Should Concern Us All. Americans for Innovation.
The no-notes meetings involve no-bid crony insiders from the military, intelligence, banking, technology, telecom, transportation, defense, venture capital, media an academia to discuss the weaponization of new inventions stolen by DARPA (Defense Advanced Research Projects Agency).
On Apr. 17, 1995, Clinton signed Executive Order 12958 titled "Classified National Security."
This order consolidated control of classification procedures to just seven people: (1) Secretary of State, (2) Secretary of Defense, (3) Attorney General, (4) C.I.A. Director, (5) U.S. Archivist, (6) National Security Director and (7) the President.
A most dubious provision said that any U.S. security classification that contradicted another country's laws or treaty rendered it of no effect. In other words, if Obama wanted to release a classified document, all he had to do was call up Justin Trudeau in Canada and ask him to pass a law saying America’s XYZ classified information was harmful to beavers on the northern slopes. That would nullify the U.S. classification and give Obama the excuse to release it. Clearly, it was a precursor to Obama’s foreign trade entanglements in the Trans-Pacific Partnership (TPP) that President Trump killed, thankfully.
On Apr. 19, 1995, the Alfred P. Murrah Federal Building in downtown Oklahoma City, was bombed by Timothy McVeigh and Terry Nichols—just two days after Bill Clinton formed a secret White House intelligence operation via Executive Order 12958 cited above.
This bombing created more excuses for mass surveillance against Americans. Notably, Clinton body guard Alan G. Whicher was killed in this weapons grade-energy blast that could not have been caused by a fertilizer bomb, as were led to believe by MSM. Retired FBI superstar Theodore L. Gunderson, a short-list candidate to be FBI director, revealed that psychiatrist Dr. Jolly West, one of the founders of the C.I.A. MKUltra mind control program, paid a visit to McVeigh before the trial. Gunderson said he believed that McVeigh was a brainwashed MKUltra drone.
On Jul. 12, 1995, IBM and Lotus merged. Lotus Notes became the Deep State’s groupware platform of choice for establishing a global mass surveillance spy grid. PKI (Public Key Infrastructure) encryption standards were selected to build into IBM/Lotus/Microsoft/Novell/Red Hat software, hardware and firmware.
Laws changed to prepare for the Patriot Act abolishment of the Bill of Rights
Between 1995-1999, a series of national security laws, executive orders (EOs) and presidential policy directives (PPDs) were written for Clinton by James P. Chandler, III, his national security and intellectual property advisor.
Magically, the laws that Chandler drafted passed nearly unanimously. (Note: Whenever that occurs, all of Congress has been bought off or fooled en masse before the vote. Remember: Clinton had likely already had access to the FBI encryption keys by this time. Therefore, he had amassed plenty of blackmail and extortion information on every influential member of Congress.)
On Feb. 28, 1996, FBI Director Louis Freeh self-consciously deferred to James P. Chandler, III in his testimony on economic espionage, revealing that Chandler controlled FBI security policy for Clinton. Freeh was clearly the puppet and Chandler the puppet master.
Bookmark: #chandler-fbi-freeh-clinton-mueller-congress-mass-surveillance-scam | https://tinyurl.com/y7vhfozr
Professor James P. Chandler biography, National Intellectual Property, p. 6; Chandler admission and notorious Washington, D.C. knowledge among Chandler associates in the National Intellectual Property Law Institute.
On Oct. 11, 1996, Congress passed three Clinton-Chandler laws that were used to further gut Congressional oversight over security and privacy. It enabled the FBI to increase mass surveillance, then lie about it.
The Economic Espionage Act, 18 U.S. Code § 1831;
The Federal Trade Secrets Act, 18 U.S.C. § 1836; and
The False Statements Accountability Act of 1996, 18 U.S.C. § 1001.
Hindsight shows that the names for these laws were a cruel, unlawful, immoral, devilish deceit and had the opposite of the intentions of the rogue C.I.A., Clinton's, Chandler, Mueller, Comey, etc. to fuel economic espionage, theft of trade secrets and lying to Congress, courts, the President and We the People.
On Feb. 12, 1997, Chandler incorporated Eurotech, Ltd. to hire former Soviet scientists and engineers to build embedded encryption spy backdoors inside all computer hardware, firmware and software in Italy. The key Eurotech players were/are Microsoft, IBM, Intel, Cisco, Oracle and Wind River, among others. JPMorgan Chase’s John McNeil Wilkie helped expand the company, as did Fenwick & West LLP (another Leader Technologies patent attorney and Silicon Valley C.I.A. co-conspirator).
On Oct. 23, 1997, The Clinton Foundation was formed.
Mar. 5, 1998—Jul. 11, 1999, Clinton and Gen. Wesley Clark prosecuted the Kosovo fraud based on a so-called “Racak genocide massacre” false flag. French journalists have proved that Racak was completely staged. However, it did succeed in cajoling Congress to approve U.N. intervention (led by Gen. Wesley K. Clark), and it succeeded in disabling Orthodox Christian resistance to the planned jihadi migration wave now occurring.
On Aug. 06, 1998, Robert S. Mueller, III's law firm Hale & Dorr (now Wilmer Hale) helped file "The Internet of Things" patents for Hewlett-Packard’s Richard C. Walker that described a global surveillance grid that even monitors and controls individual body functions and describes human beings as "wet-ware." The invention also contains an accounting and taxing capability to manage "certificate authorities" to control Public Key Infrastructure (PKI) encryption, tax the Internet and control "wet-ware" access.
Bookmark: #walker-patent | https://tinyurl.com/y87pvqgq
On Aug. 18, 1998, Entrust Technologies, Inc. went public after being started as a spin-off of Nortel Networks (Canada) to manage and distribute Public Key Infrastructure (PKI) Certificate Authorities—the encryption keys for the Internet. Their customers include important military, banking, healthcare and government entities in the U.S., U.K., Australia, Canada, Sweden, Denmark, France, Italy, Spain and China.
Bookmark: #entrust-1998-prospectus | https://tinyurl.com/y9h6ogel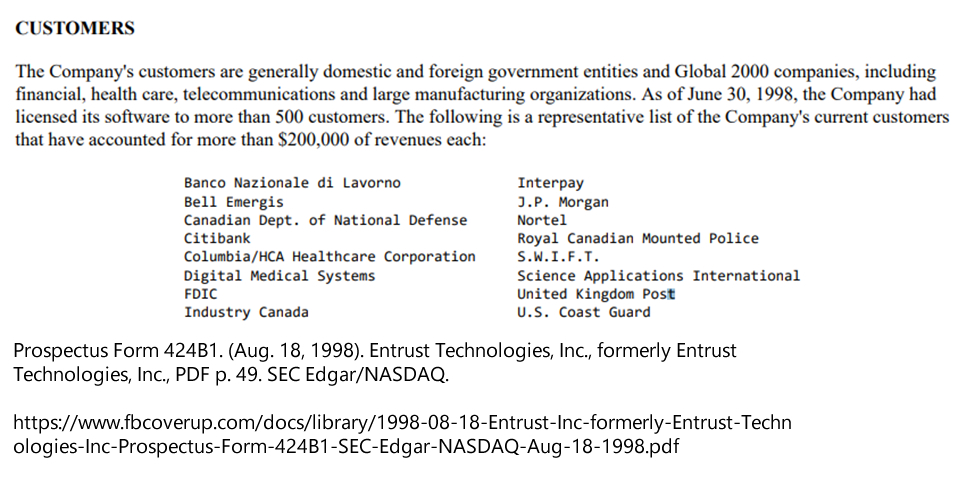
On Oct. 14, 1998, SI International, LLC, later renamed SERCO SERVICES, Inc., was allowed to form with Lockheed Martin and Senior Executive Service (SES) executives associated with the treasonous Highlands Group (Feb. 1995). Lockheed Martin runs the Queen's "Golden Share" company British Nuclear Fuels Limited with SERCO.
On Dec. 20, 1998, globalist psychopath George Soros admitted to having been a Hungarian Jewish Nazi collaborator without remorse for betraying his own Jewish brothers and sisters.
On Mar. 09, 1999, Clinton's Vice President Al Gore took credit for founding the Internet, laughably.
On Jul. 01, 1999, Clinton Attorney General Janet Reno created a new "Office of Special Counsel" inside the Department of Justice after the Special Counsel law was not re-authorized by Congress. This dubious Department of Justice policy (not a law) is now being used to justify the Mueller witch hunt.
On Jul. 02, 1999, Clinton appointed Larry H. Summers Treasury Secretary. The next day, on Jul. 03, 1999, Summers appointed Sheryl K. Sandberg as chief of staff. Sandberg later started Gmail in Jan. 20, 2001, and then became Facebook chief operating officer on Mar. 14, 2008.
Summers' former Treasury staffer (1993-2001), Marne L. Levine (Deutch) became Summers' chief of staff starting at Harvard on Jul. 02, 2001 where she oversaw the C.I.A.'s MKUltra establishment of the 19-year old Mark Zuckerberg as their Facebook cardboard cut out. Then, she became product vice president at AOL on Apr. 06, 2009. Then, she became Summers' chief of staff for the National Economic Council on Jan. 21, 2009. Then, she became Obama's Special Assistant to the President for Economic Policy on Jun. 24, 2010. Then, she attended an exclusive dinner with Hillary and Sandberg on Mar. 27, 2012. Then, she became chief operating officer of Instagram on Oct. 07, 2014. Truly magical.
White House rogue intelligence NOC (Network Operating Center): National Infrastructure Assurance Council
On Jul. 14, 1999, the Clinton White House set up a spy skunk works that has run rogue intelligence operations called the “National Infrastructure Assurance Council (NIAC)” On Jan. 18, 2001, Clinton appointed James P. Chandler, III and Bill Gates, Microsoft, as directors on NIAC the day before he left office and the same day he pardoned his former CIA director John M. Deutch (Marne L. Levin-Deutch's father in law) and fraudster Marc Rich.
On Sep. 16, 1999, Clinton announced "relaxed" encryption rules in a flurry of press releases and letters to Congress, which were most assuredly drafted by national security advisor James P. Chandler, III. This action effectively gutted normal engineering security practices. It had the effect of enabling unfettered foreign and domestic access to U.S. classified data.
On Sep. 29, 1999, Bill Clinton established In-Q-Tel Silicon Valley cardboard cutouts for the C.I.A. to be able to raise private venture capital funds to build its rogue operations. It is illegal for a government agencies to invest in private companies.
Bookmark: #in-q-tel-formed-by-cia | https://tinyurl.com/ydcmaxpp
On Nov. 12, 1999, Bill Clinton and Larry Summers abolished Glass-Steagall banking controls, enabling the banks to fund In-Q-Tel “private” companies.
On Nov. 17, 1999, Agilent Technologies went public using Robert S. Mueller’s III’s law firm Hale and Dorr (renamed Wilmer Hale). Agilent Technologies was tasked with building the digital infrastructure for “The Internet of Things” global mass surveillance of everything using the Richard C. Walker HP/Agilent patents for monitoring all human beings called “wet-ware” in the patents.
On Jun. 08, 2000, Clinton espionage attorney James P. Chandler, III, participated in seminal Leader invention design meetings as Leader’s newly-appointed patent attorney. He was fully briefed on Leader’s social networking innovations at this meeting (see photo below) without disclosing his Deep State shadow government conflicts of interest and treachery.
Bookmark: #chandler-learned-leader-innovations-jun-08-2000 | https://tinyurl.com/y9medtrp
On Jun. 20, 2000, Sir Geoffrey E. Pattie was awarded the ISSA Silver Star Award in Washington, D.C. Pattie is the primary spy director for the Queen’s Privy Council and founder of SCL Ltd. and Cambridge Analytica—two C.I.A. MKUltra mind control and brain washing operations in the UK.
On Aug. 25, 2000, F. Gary Davis, Acting Director of the U.S. Office of Government Ethics, issued a tortured 13-page "advisory" that dramatically muddied the waters on mutual fund investing disclosure. Davis left government service soon thereafter. This opinion opened the door to massive nondisclosure fraud by politicians, SES and federal bureaucrats.
In 2001, NSA Director Michael V. Hayden recommended expansion of the NSA's Senior Executive Service (SES) programs.
On Apr. 15, 2001, C.I.A. whistleblower Susan Lindauer warned American senior intelligence leadership that "I first learned of the 9/11 Conspiracy from my CIA handler, Dr. Richard Fuisz, in mid-April, 2001." She was imprisoned for a year without due process to shut her up as the first casualty of The Patriot Act.
In Jul. 2001, Department of Justice John C. Yoo was hired into the Office of Legal Counsel (OLC) and gave legal opinion cover for a proposed NSA project “Stellar Wind” for mass surveillance of American citizens.
On Sep. 04, 2001, Robert S. Mueller, III was sworn in as FBI Director by President George W. Bush, just 10 days before 9/11.
On Sep. 11, 2001, World Trade Center, Pentagon and Shanksville “terror” attacks were timed simultaneously with DoD NORAD war games and a stand down order.
On Oct. 04, 2001, President Bush approves operation “Stellar Wind” mass surveillance on American citizens.
On Oct. 16, 2001, President Bush signed Executive Order 13231 "Critical Infrastructure Protection in the Information Age" forming the "National Infrastructure Advisory Council (NIAC)." The order used the same NIAC acronym used by Clinton as the excuse for setting up a mass surveillance networking operating center run out of the White House.
On Oct. 26, 2001, President Bush signed The Patriot Act that has essentially destroyed the Bill of Rights. Just look at the flies that gathered to watch the signing.
Bookmark: #patriot-act-signed | https://tinyurl.com/y8zvjr4x
On Oct 31, 2001, NSA whistleblower and former chief architect William E. Binney resigned the NSA saying the agency had "gone rogue."
On Nov. 29, 2001, IBM intellectual property attorneys James P. Chandler, III and David J. Kappos used a $40 million IBM “donation” to start the IBM Eclipse Foundation which has been the exclusive distributor of Leader Technologies’ social networking innovations.
On Aug. 29, 2002, IBM Eclipse Foundation distributed Version 2.0.1 that included all of Leader Technologies' social networking innovations.
On Sep. 18, 2002, career IBMer Thomas E. Noonan (Internet Security Systems, Inc.) was appointed to the National Infrastructure Assurance Council (NIAC) by George W. Bush, surely recommended by James P. Chandler, and he remains a member of the Council to this day. In 2003, Noonan became a partner to ENTRUST INC. Public Key Infrastructure (PKI) controlled by Hillary Clinton.
On Dec. 04, 2002, the entire Silicon Valley military-industrial complex began joining the IBM Eclipse Foundation to receive Leader Technologies' social networking invention source code, all of which IBM criminally claimed copyright, and then criminally declared "open source." They admitted a "single company [Leader Technologies]" for their code.
Bookmark: #ibm-eclipse-distributes-stolen-leader-social-networking-invention | https://tinyurl.com/y9mmr36z![respectively.[209]](https://www.fbcoverup.com/docs/library/2002-12-04-Minutes-of-the-Eclipse-Board-Meeting-Dec-04-2002.jpg)
On Oct. 29, 2003, ENTRUST INC was awarded the contract to supply all 50,000 encryption keys for the Federal Bureau of Investigation (FBI).
Bookmark: #fbi-entrust-conspiracy | https://tinyurl.com/ycscm59j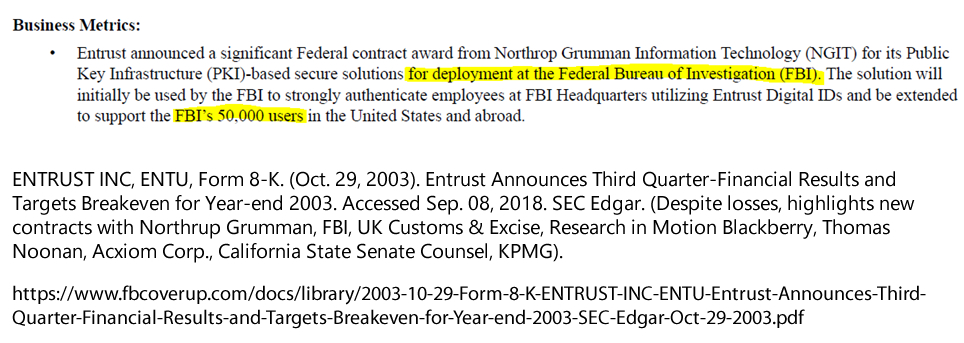
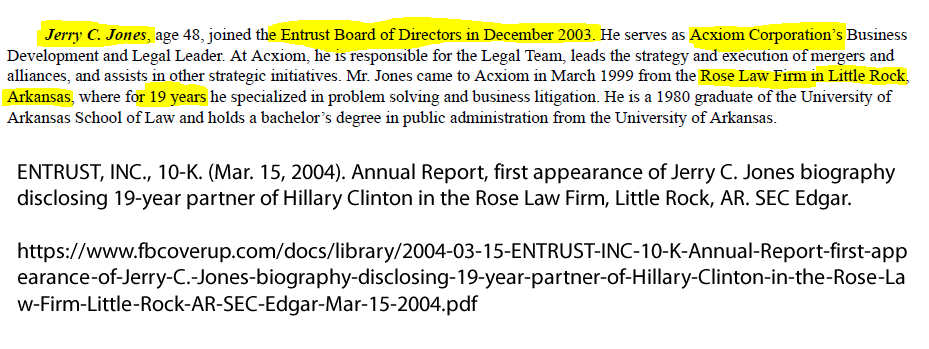
On Dec. 04, 2003, ENTRUST INC elected Jerry C. Jones as a "Class I" director to replace retiring Gen. Wesley K. Clark. Jones is a 19-year Hillary Clinton partner at the Rose Law Firm, Little Rock, Arkansas. With the appointment of Jones, FBI Director Robert S. Mueller, III had an ethical duty to disclose to the public that his approval of ENTRUST INC to manage 50,000 FBI encryption keys enabled his political mentor Hillary Clinton to have full access to the entire FBI operation.
Bookmark: #fbi-entrust-mueller-jones-hillary-conspirators | https://tinyurl.com/y8fsqmjl Bookmark: #jones-secretly-elected-entrust-director | https://tinyurl.com/yamr7zad
On Sep. 09, 2008, the IBM Eclipse Foundation boasted 191 members [Silicon Valley allies of the fascist Senior Executive Service (SES)] , including Microsoft, AT&T, Verizon, Facebook, Google, YouTube, SAP, Cisco, Oracle, HP, Samsung, Motorola, Nokia, Sony, JPMorgan Chase, Goldman Sachs and Tsinghua University (Beijing, China). Most if not all of these companies are ENTRUST INC (or sublicenser) clients, and probably all of them embed the NSA Dual_EC_DRBG encryption backdoor key algorithm in their hardware, software and firmware. See AFI (Nov. 06, 2015). Complicit encryption geeks enable the American spy state. Americans for Innovation.
Bookmark: #ibm-eclipse-membership-sep-17-2008 | https://tinyurl.com/y9xntl6j
See The Eclipse Foundation (Sep. 09, 2008). Membership Logos [Board minutes]; See also The Eclipse Foundation(Sep. 17, 2008). The Members of Eclipse, Minutes of the Eclipse Board Meeting, Sep. 17, 2008; AFI. (Jan. 15, 2015). IBM plots digital control with federal judges; steals inventions, p. 6.
On Mar. 11, 2009, ENTRUST INC. issued its last 10-K annual report before selling its operation to Orlando Bravo and his Thoma Bravo, LLC private equity firm in San Francisco, CA. They disclosed that they had "more than 2,000 customers in 60 different countries."
Bookmark: #entrust-relationships | https://tinyurl.com/y77rkg4q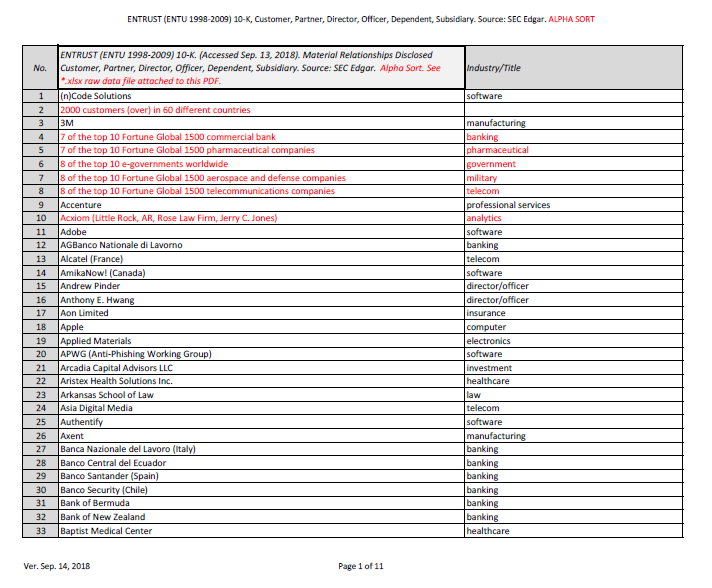
ENTRUST INC. SEC Filings Timeline:
1999 | 2000 | 2001 | 2002 | 8-K. FBI Contract Press Release (Oct. 29, 2003) | Jones' Stock Options (Dec. 05, 2003) | 2003 | Co. Overview (2003) | Jones' Signature (Dec. 23, 2003) | Jones' Bio (Mar. 15, 2004) | 2005 | 2006 | 2007 | 2008 | 2009 | 2009A | Relationships (1998-2009)
On Jul. 16, 2009, ENTRUST, INC. proposed to shareholders to sell to Orlando Bravo and his Thoma Bravo, LLC private equity firm in San Francisco, CA., which occurred on Aug. 07, 2009.
Conclusions:
Conclusion #1: Robert S. Mueller, III had an affirmative duty to disclose his approval of the contract for ENTRUST to manage the FBI's 50,000 encryption keys in late 2003. The FBI itself has been scandalously compromised to Hillary Clinton and the Rose Law Firm ever since.
Conclusion #2: ENTRUST's planetary control of the encryption keys for "over 2000 customers in 60 different countries" means that any matter handled by their customers at the FBI, Department of State, NSA, Treasury, etc. is the fruit of a poisonous tree—tainted by Clinton corruption.
Conclusion #3: President Trump has enough evidence here to seize and prosecute the leaders of every government agency that has involved that agency, or induced other agencies to work with ENTRUST, without disclosing their total compromise to Hillary Clinton and her crime syndicate.
Clearly, Hillary Clinton's director surrogate at ENTRUST, INC., Jerry C. Jones (2003-2009), steered the development of the company's control over encryption keys for the maximum benefit of his Clinton overlords.
At a bare minimum, Mueller and the FBI leadership has had an ethical duty ever since Jerry C. Jones became an ENTRUST director to disclose his direct conflict of interest and compromise of FBI operations by Hillary Clinton, his mentor.
* * *
Return to return to the beginning of this post.* * *
Notices: This post may contain opinion. As with all opinion, it should not be relied upon without independent verification. Think for yourself. Photos used are for educational purposes only and were obtained from public sources. No claims whatsoever are made to any photo.
Comment
Click "N comments:" on the line just below this instruction to comment on this post. Alternatively, send an email with your comment to afi@leader.com and we'll post it for you. We welcome and encourage anonymous comments, especially from whisteblowers.
Leader Technologies, Inc. sent their FIRST AMENDED MILLER ACT NOTICE to President Trump today. It is a contract demand for the U.S. Treasury to pay them for the federal government's 18-year theft of their social networking inventions. These inventions were stolen by Major General James E. Freeze (US Army, ret.) and Leader's patent attorney James P. Chandler, III, on behalf of Andrew W. Marshall and the Department of Defense Office of Net Assessment that steals and weaponizes inventions for continuous war making and enrichment of its fascist insider military-industrial corporations.
Patriots are encouraged to help get this First Amended Miller Act Notice to President Trump and past the Praetorian Guard. See American Intelligence Media republish of the Leader Miller Act Notice.

 e.g. "IBM Eclipse Foundation" or "racketeering"
e.g. "IBM Eclipse Foundation" or "racketeering"








Email comment by JB:
ReplyDeleteYou can't make this stuff up! It turns out Judge Kavanagh’s Mother was the Judge who foreclosed on Christine Blasey Ford’s Parents’ home! Furthermore, pro-Chinese Sen Diane Feinstein and company apparently had this alleged accusation months ago – why release it at the last minute?
It's interesting to note that the accuser of Judge Kavanaugh, Christine Blasey Ford, is a progressive-leftist professor of Social Work at Palo Alto University & teaches in consortium with Stanford University. (By the way, she thought the Women's March "...didn't go far enough!")
Keep in mind, Stanford is a notorious hot-bed of Frankfurt School neo-Marxist social engineering that has given us the likes of: Sen. Diane Feinstein (D-CA), Rep. Adam Schiff (D-CA), Valerie Jarrett, Larry Page (Google), Reed Hastings (Netflix), Phil Knight (Nike), Rachel Maddow, Xavier Becerra (Attorney General of California), Cheryl D. Mills (Counselor and Chief of Staff to Hillary Clinton during her whole tenure as United States Secretary of State) and even Chelsea Clinton!
But perhaps the most interesting Alumni (given Stanford's reputation as a CIA recruitment center) is R. James Woolsey Jr. currently a Senior Vice President at security firm Booz Allen Hamilton (remember Edward Snowden?).
James Woolsey was CIA director when Aldrich Ames was arrested for treason and spying against the United States. It was Aldrich Ames that recruited the young communist John Brennan; who went on to become the Station Chief in Riyadh Saudi Arabia during 9/11 (even signing the Visa's of the alleged Saudi conspirators) before going on to become the bellicose CIA director under Obama – nicknamed "the Drone King."
It seems James Woolsey and the CIA were: '... criticized for not focusing on Ames sooner, given the obvious increase in Ames' standard of living; and there was a "huge uproar" in Congress when Woolsey decided that no one in the CIA would be dismissed or demoted at the agency. Woolsey declared: "Some have clamored for heads to roll in order that we could say that heads have rolled...Sorry, that's not my way." Woolsey abruptly resigned on Dec 28, 1994.' (Wikipedia)
Also an interesting, and perhaps relevant, Stanford Alum is Jared Cohen:
'CEO of Jigsaw (previously Google Ideas) and an Adjunct Senior Fellow at the Council on Foreign Relations. Previously, he served as a member of the Secretary of State's Policy Planning Staff and as an advisor to Condoleezza Rice and later Hillary Clinton. Initially brought in by Condoleezza Rice as a member of the Policy Planning Staff, he was one of a few staffers that stayed under Hillary Clinton later referenced in an article entitled "Tweeting While Tehran Burns." In this capacity, he focused on counter-terrorism, counter-radicalization, Middle East/South Asia, Internet freedom, and fostering opposition in repressive countries.' (Wikipedia) Hmm? "...fostering opposition in repressive countries." What this really means is regime change à la George Soros "Color Revolutions."
In light of this, the technology policy expert Alec Ross, Senior Advisor for Innovation to Secretary of State Hillary Clinton, sent an e-mail saying: "Jared [Cohen] and I met with Stanford President John Hennessy last week and we will work through Stanford to indirectly launch an innovation competition for the best apps and programs that provide tools for circumvention of politically motivated censorship." My, my, my?
http://www.youtube.com/watch?v=DjQy6ptWo78
Previous comment:
Deletehttps://tinyurl.com/yc4hp4mn
Spread the truth.
Email comment by GH:
ReplyDeleteJohn Binder. (Sep. 16, 2018). Kavanaugh Accuser Signed Letter Fighting Trump Border Enforcement. Breitbart.
The woman accusing President Trump’s United States Supreme Court nominee Brett Kavanaugh of a “rape attempt” when the two were in high school previously signed a letter fighting Trump’s “Zero Tolerance” policy at the U.S.-Mexico border.
The American Civil Liberties Union (ACLU)—an open borders advocacy organization—letter was written and sent to Department of Homeland Security (DHS) Secretary Kirstjen Nielsen and Attorney General Jeff Sessions in June.
Christine Blasey Ford, a psychology professor, signed the ACLU letter as “Christine Blasey Ph.D. Psychologist,” signing off on statements that accused Trump of using southern border enforcement to “traumatize children” and claimed the Zero Tolerance policy was “violating fundamental human rights.”
The policy to prosecute all illegal border crossers, enacted by the Trump administration, including illegal alien adults who cross the border with children, results in border-crossing parents having their children taken into federal custody. This is a loophole known as the Flores Settlement Agreement.
Detaining child border crossers was a policy during the Obama administration when Breitbart Texas exclusively reported on the conditions in which unaccompanied minors were being packed into crowded cells and holding facilities. As Breitbart News reported, the federal government has separated adult border crossers from the children they have brought with them into the U.S. as far back as 2001, court records reveal.
Full story:
https://www.breitbart.com/big-government/2018/09/16/kavanaugh-accuser-signed-letter-fighting-trump-border-enforcement/amp/
Previous comment:
Deletehttps://tinyurl.com/ycj3362u
Spread the truth.
Email comment by Anon:
ReplyDeleteBaxter Dmitry. (Sep. 17, 2018). Breaking: Kavanaugh Accuser’s Brother’s Firm Linked To Fusion GPS. YourNewsWire.
Christine Blasey-Ford, Brett Kavanaugh's accuser, has a brother worked for a law firm that retained Fusion GPS.
Christine Blasey-Ford, the 51-year-old woman who has come out of the woodwork at the last minute, accusing Brett Kavanaugh of sexually assaulting her as a teenager, has a brother who worked for a law firm that later retained Fusion GPS, the primary “fixer” for the Clintons and the DNC.
Ralph Blasey, brother of Christine Blasey-Ford, worked for 15 years as a Litigation Partner for Baker Hostetler, a law firm that ended up retaining Fusion GPS, the infamous D.C. company that produced the unverified Steele dossier on President Donald Trump and Russia, sparking the whole Russian collusion investigation.
Full story with evidence:
https://yournewswire.com/kavqanaugh-accuser-brother-fusion-gps/amp/
Previous comment:
Deletehttps://tinyurl.com/y757p3q2
Spread the truth.
Email comment by Roger Stone:
ReplyDeleteStaff. (Sep. 16, 2018). STONE CAN’T THINK OF ‘ANY CIRCUMSTANCE’ IN WHICH HE’D TESTIFY AGAINST TRUMP. VARIETY INTERVIEW WITH ROGER STONE.
Stone Can’t Think of ‘Any Circumstance’ in Which He’d Testify Against Trump - Variety Interview With Roger Stone
(VARIETY.com) WASHINGTON — Roger Stone, the political consultant who served as informal adviser to the Trump campaign, said it is “conceivable” that special counsel Robert Mueller will “bring some bogus charge against me,” but he can’t think of any circumstance in which he’d testify against President Donald Trump.
In an interview with Variety‘s “PopPolitics” on SiriusXM’s political channel POTUS, Stone said, “it is possible the special counsel could bring an action against me that is designed to make me testify against Donald Trump, who I have known on an intimate basis for almost 40 years.”
He added, “I do not work in the Trump White House. There are some things he has done as president that I do not agree with, and other things that he has done as president that I do agree with. But that said, I can’t think of any circumstance under which I would be willing to testify against him.”
Full story [VIDEO]:
https://stonecoldtruth.com/stone-cant-think-of-any-circumstance-in-which-hed-testify-against-trump/
Previous comment:
Deletehttps://tinyurl.com/y7xutco5
Spread the truth.
Email comment by David Knight:
ReplyDeleteDavid Knight. (Sep. 18, 2018). BREAKING LIVE! TRUMP ORDERS SECRET RUSSIA DOCUMENTS DECLASSIFIED. Infowars.
President Trump has ordered the release of key documents regarding the FISA court warrant on Carter Page, all reports of FBI interviews with Bruce Ohr, as well as “the release of all text messages relating to the Russia investigation, without redaction, of James Comey, Andrew McCabe, Peter Strzok, Lisa Page, and Bruce Ohr.”
Full story [VIDEO]:
https://www.infowars.com/breaking-live-trump-orders-secret-russia-documents-declassified/
Previous comment:
Deletehttps://tinyurl.com/ydfwzetz
Spread the truth.
Email comment by Alex Jones:
ReplyDeleteReuters. (Sep. 18, 2018). NORTH KOREA’S KIM: SUMMIT WITH TRUMP “STABILIZED” REGION. Reuters / Infowars.
North Korean leader Kim Jong Un said on Tuesday his “historic” summit with U.S. President Donald Trump in Singapore stabilized regional security, and that he expected further progress at an inter-Korean summit aimed at reviving stalled nuclear diplomacy.
Kim thanked South Korea’s President Moon Jae-in for bringing about the Singapore meeting in June as the two leaders began their third round of talks in Pyongyang.
“Thanks to that, the political situation in the region has stabilized and I expect more advanced results,” Kim told Moon, referring to the Singapore gathering, at the start of their talks.
Full story:
https://www.infowars.com/north-koreas-kim-summit-with-trump-stabilized-region/
Previous comment:
Deletehttps://tinyurl.com/ydd7umnv
Spread the truth.
Email comment by TG:
ReplyDeleteJames O'Keefe. (Sep. 18, 2018). Deep State Unmasked: State Department on Hidden Cam, “Resist Everything,” “I Have Nothing to Lose”. Project Veritas.
Federal Employee for State Department: “Resist everything… Every level. F**k sh*t up.”
Democratic Socialists of America (DSA) Embedded in Federal Government Positions, Actively Resisting
Stuart Karaffa Does Work for DSA While on Taxpayer’s Dime: “I’m careful about it. I don’t leave a paper trail.”
“I have nothing to lose. It’s impossible to fire federal employees.”
Ethics Officer Fails to Recognize Breach on Ethics Form: “somebody just rubber stamps it and it goes forward…”
Full story [VIDEO]:
https://www.projectveritas.com/2018/09/18/deep-state-unmasked-state-department-on-hidden-cam-resist-everything-i-have-nothing-to-lose/
Previous comment:
Deletehttps://tinyurl.com/y9h6dgvf
Spread the truth.
AP. (Sep. 19, 2018). “I’m disappointed!” Trump slams Jeff Sessions. The Horn News.
ReplyDeleteThe feud between President Donald Trump and his Attorney General Jeff Sessions escalated on Wednesday after the president said, “I don’t have an attorney general.”
Trump, in an interview with The Hill, said that he’s “so sad over Jeff Sessions,” whom he has repeatedly denounced for recusing himself from the Russia investigation.
The president broadened his disappointment with Session far beyond his recusal, claiming that Sessions has not performed up to Trump’s standards on several issues.
Full story:
https://thehornnews.com/im-disappointed-trump-slams-jeff-sessions/
Previous comment:
Deletehttps://tinyurl.com/y8qdjhvp
Spread the truth.
Email comment by Tom Fitton:
ReplyDeleteRamona Cotca. (Sep. 19, 2018). Inside Judicial Watch: THE LATEST on Bruce Ohr & the Clinton-DNC Dossier. Judicial Watch.
In this edition of “Inside Judicial Watch,” JW Senior Attorney Ramona Cotca joins host Jerry Dunleavy to discuss the latest developments in our battle to get to the truth about the Department of Justice’s relationship with Fusion GPS, the opposition research firm that produced the Clinton-DNC dossier on Trump.
Full story [VIDEO]:
https://www.judicialwatch.org/video-update/inside-judicial-watch-the-latest-news-on-bruce-ohr-the-doj-and-their-relationship-with-fusion-gps/
Previous comment:
Deletehttps://tinyurl.com/y9xzaw6x
Spread the truth.
Previous comment:
ReplyDeletehttps://tinyurl.com/y75vvreo
Spread the truth.
Email comment by Alex Jones:
ReplyDeleteshtfplan.com. (Sep. 20, 2018). TAXING AND TRACKING THE INDEPENDENT MEDIA: CENSORSHIP AND CONTROL. Infowars.
Taxing and Tracking the Independent Media: Censorship and Control
One of the most heinous things about taxes is that they support the very “organs” (to quote a Soviet-era term) of government that crush the people…even further.
The taxes are weapons used by the authorities…and all authority comes from the barrel of a gun (to paraphrase Mao). The taxes are used to corral in the masses and keep them upon a continuous treadmill that sustains the system…the very system that exploits and enslaves the citizens.
The most heinous of all is the “death tax” of 50% to the government after you die. If you made a million in money and property at the end of your existence…paying taxes on it all the way…the original income taxes on the money you made, and then the interest income tax on what you made from your investments. You have property taxes on your house. You are (depending on your state) levied taxes on ad valorem, or state income taxes, or community (city, town) taxes. You are taxed on gifts you give to your children. You are taxed when you begin a business.
Full story:
https://www.infowars.com/taxing-and-tracking-the-independent-media-censorship-and-control/
Previous comment:
Deletehttps://tinyurl.com/ycgmtsww
Spread the truth.
Email comment by Roger Stone:
ReplyDeleteRoger Stone. (Sep. 18, 2018). ROGER STONE ISSUES A CLARIFICATION AND APOLOGY TO DONALD TRUMP JR. StoneColdTruth.com.
AN INFOWARS EXCLUSIVE
Posted by Roger Stone | Sep 18, 2018 | Latest News | 0
Roger Stone Issues A Clarification And Apology To Donald Trump Jr
I reported last week, incorrectly, that Don Jr. was in the crosshairs of Mueller. I am here tonight to correct myself, and the record. That is not true at this time.
https://www.infowars.com/trump-jr-presidents-trusted-circle-much-smaller-after-nyt-op-ed/
https://stonecoldtruth.com/roger-stone-issues-a-clarification-and-apology-to-donald-trump-jr/
Previous comment:
Deletehttps://tinyurl.com/yb9eokaj
Spread the truth.
Email comment by TG:
ReplyDeleteTRUTH NEWS HEADLINES SEPT 20, 2018
- President Trump: "I don't have an attorney general. It's very sad." "I'm very disappointed in Jeff. Very disappointed."
- FBI, DOJ To Defy Trump Order
- Does Christin Blasey Ford even exist?
- Broaddrick: FBI Probe Ford Allegation? Then 'Investigate My RAPE Allections. Against Clinton
Full stories:
https://aim4truth.org/2018/09/19/truth-news-headlines-september-19-2018-2/
Previous comment:
Deletehttps://tinyurl.com/y6w4kyft
Spread the truth.
why,why, are these leftwing democrats trying to pull off a coup. They all have been caught just a matter of time to get them indited and sent to jail. I think Americans are sick of this slow walking everything trying to get to midterms were I think they are going to get their asses kicked.
ReplyDeleteEmail comment by TG:
ReplyDeleteTRUTH NEWS HEADLINES SEPT 25, 2018
- Gallup: GOP Rises to Highest Approval Rating in Nearly a Decade
- Stall and Delay Tactic: Lawyer Casts Doubt on Ford Appearing at Thursday Kavanaugh Hearing
- The Brits did it... with help from Senior Executive Service
- Meet Noel Francisco, SES Operative Who (Some Say) Would Replace Rod Rosenstein
Full stories:
https://aim4truth.org/2018/09/25/truth-news-headlines-september-25-2018/
Previous comment:
Deletehttps://tinyurl.com/ybhenusg
Spread the truth.
Email comment by GH:
ReplyDeleteAnthony Cuthbertson. (Sep. 22, 2018). GOOGLE ADMITS GIVING HUNDREDS OF FIRMS ACCESS TO YOUR GMAIL INBOX. Independent UK.
Hundreds of apps are able to scan and share data from the email inboxes of Gmail accounts, Google has revealed.
In a letter to US lawmakers, which was made public on Thursday, Google explained that third-party developers are able to both access and share data from Gmail accounts – though the company said it thoroughly vets any third parties that are granted access, and permission must be given by the user.
The inbox scanning takes place despite Google ending its own controversial email-scanning practice a year ago.
"Developers may share data with third parties so long as they are transparent with the users about how they are using the data," Susan Molinari, Google's head of US public policy, wrote in the letter, which was first seen by the Wall Street Journal.
Full story:
https://www.independent.co.uk/life-style/gadgets-and-tech/news/google-gmail-data-sharing-email-inbox-privacy-scandal-a8548941.html
Previous comment:
Deletehttps://tinyurl.com/y7cpmnzw
Spread the truth.
More deception. Google insists that the users give permission to use their personal information, and that they are transparent. What they neglect to say is that no one can use Google without giving away all user rights in their personal information in exchange for using the services!
DeleteEmail comment by Katie:
ReplyDeletePatrick Howley. (Sep. 25, 2018). EXPOSED: Kavanaugh Second Accuser Is A Left-Wing Activist Who Campaigned Against The Word ‘Sissy’. Big League Politics.
Brett Kavanaugh’s second accuser Deborah “Debbie” Ramirez is a left-wing activist who spoke at a PFLAG (Parents, Families and Friends of Lesbians and Gays) event and agitated against use of the word “Sissy” on T-shirts handed out at an annual Colorado 10k run.
Ramirez, who claimed with no evidence that Kavanaugh exposed himself at a college party, is the senior volunteer coordinator for the Boulder County Department of Housing and Human Services. She is known colloquially as “Debbie.”
Full story:
https://bigleaguepolitics.com/exposed-kavanaugh-second-accuser-is-a-left-wing-activist-who-campaigned-against-the-word-sissy/
Previous comment:
Deletehttps://tinyurl.com/yaz3jsq3
Spread the truth.
Email comment by TG:
ReplyDeleteTRUTH NEWS HEADLINES SEPT 26, 2018
- WH's Conway: 'Vast Left-Wing Conspiracy' Attacking Kavanaugh
- Trump: Democrats Playing 'Con Game'
- W. Virginia Decisions to Allow Smartphone Voting for Midterms Raises Serious Security Concerns
- Mike Adams: Signed Executive Orders reveal Trump is planning mass arrests, military tribunals for deep state traitors
Full stories:
https://aim4truth.org/2018/09/26/truth-news-headlines-september-26-2018/
Previous comment:
Deletehttps://tinyurl.com/y7kuqr2r
Spread the truth.
Email comment by GH:
ReplyDeleteSam Biddle. (Sep. 26, 2018). THE GOVERNMENT WANTS AIRLINES TO DELAY YOUR FLIGHT SO THEY CAN SCAN YOUR FACE. The Intercept.
OMNIPRESENT FACIAL RECOGNITION has become a golden goose for law enforcement agencies around the world. In the United States, few are as eager as the Department of Homeland Security. American airports are currently being used as laboratories for a new tool that would automatically scan your face — and confirm your identity with U.S. Customs and Border Protection — as you prepare to board a flight, despite the near-unanimous objections from privacy advocates and civil libertarians, who call such scans invasive and pointless.
According to a new report on the Biometric Entry-Exit Program by DHS itself, we can add another objection: Your flight could be late.
Although the new report, published by Homeland Security’s Office of the Inspector General, is overwhelmingly supportive in its evaluation of airport-based biometric surveillance — the practice of a computer detecting your face and pairing it with everything else in the system — the agency notes some hurdles from a recent test code-named “Sprint 8.” Among them, the report notes with palpable frustration, was that airlines insist on letting their passengers depart on time, rather than subjecting them to a Homeland Security surveillance prototype plagued by technical issues and slowdowns:
Full story:
https://theintercept.com/2018/09/26/airport-facial-recognition-flight-delay/
Previous comment:
Deletehttps://tinyurl.com/y76jy9t4
Spread the truth.
Email comment by Tom Fitton:
ReplyDeleteChris Ferrell: (Sep. 27, 2018). Chris Farrell: Leftists’ Abuse of Process Towards Kavanaugh ‘Corrosive to the Constitution’. Judicial Watch.
September 26, 2018- JW Director of Investigations and Research Chris Farrell appeared “Lou Dobbs Tonight” on the Fox Business Network to discuss whether Rod Rosenstein will be fired and the Kavanaugh hearing.
Full story:
https://www.judicialwatch.org/press-room/in-the-news/chris-farrell-leftists-abuse-of-process-towards-kavanaugh-corrosive-to-the-constitution/
Previous comment:
Deletehttps://tinyurl.com/y8xpyzbc
Spread the truth.
Email comment by BR:
ReplyDeleteTRUTH NEWS HEADLINES OCT. 1, 2018
- U.S. and Canada Reach Basis of Deal to Replace NAFTA House Before U.S.-Mexico Deadline
- Merkel Fights for Globalism, Warns Trump Against 'Destroying' the United Nations
- McCaskill takes a hit in the polls after opposing Kavanaugh confirmation
- Fox News Cowards Spread Fake News that Christin Blasey Fort is 'Credibile'
Full stories:
https://aim4truth.org/2018/10/01/truth-news-headlines-october-1-2018/
Previous comment:
Deletehttps://tinyurl.com/y87ntnwh
Spread the truth.
Email comment by TG:
ReplyDeleteTRUTH NEWS HEADLINES OCTOBER 5, 2018
- Trump Has 50% Approval Rate Says Rasumussen Poll
- Demoncrat Sen. Jeff Merkley demands immediate court ruling to halt Kavanaugh vote
- Watch DiFiChi just after she read the new Kavanaugh report. Looks like something went very, very wrong....
- Kavanaugh Vote Rallies the Base
Full story:
https://aim4truth.org/2018/10/04/truth-news-headlines-october-5-2018/
Previous comment:
Deletehttps://tinyurl.com/ya2cg9fr
Spread the truth.
Email comment by GH/JJ:
ReplyDeleteJohn Solomon. Oct. 08, 2018). Former FBI lawyer: Plot to record, remove Trump not a joke. The Hill.
Don’t tell former FBI general counsel James Baker that those now-infamous discussions about secretly recording President Donald Trump and using the tapes to remove him from office were a joke.
He apparently doesn’t believe it. And he held quite the vantage point — he was on the inside of the bureau’s leadership in May 2017, when the discussions occurred.
Baker told Congress last week that his boss — then-Acting FBI Director Andrew McCabe — was dead serious about the idea of surreptitiously recording the 45th president and using the evidence to make the case that Trump should be removed from office, according to my sources.
Baker told lawmakers he wasn’t in the meeting that McCabe had with Deputy Attorney General Rod Rosenstein in which the subject came up. But he did have firsthand conversations with McCabe and the FBI lawyer assigned to McCabe, Lisa Page, about the issue.
Full story:
https://thehill.com/hilltv/what-americas-thinking/410447-former-fbi-lawyer-plot-to-record-remove-trump-not-a-joke
Previous comment:
Deletehttps://tinyurl.com/y86k2ftb
Spread the truth.
Email comment by BR:
ReplyDeleteAnonymous Patriots. (Oct. 08, 2018). Remember ‘Mao Tze Tung Loving’ Communist Anita Dunn? Patriots for Truth.
FLASHBACK TO AUGUST 4, 2016: “Pervasive ties have been uncovered that directly link the former and current personal legal counsels to President Obama, Robert F. Bauer (PDF) (No. 23), and his wife, Anita B. Dunn, and their long-time law firm, Perkins Mao-Tse-TungCoie LLP, with the Facebook Cabal.
Y’all remember Anita Dunn..right?
Her favorite political philosopher is Mao Tze Tung.
Remember the article recently regarding another attorney from Perkins Coie – Michael Sussman? See here. Connect the dots. They couldn’t be more obvious.
Full story:
https://patriots4truth.org/2018/10/08/remember-mao-tze-tung-loving-communist-anita-dunn/
See also:
https://americans4innovation.blogspot.com/2013/07/fix-leader-v-facebook-to-restore.html
Previous comment:
Deletehttps://tinyurl.com/y8ofnm9m
Spread the truth.
Can we remove ENTRUST Authorities from our computer certificates? I see Entrust, INC and Entrust.net.
ReplyDeleteThis would all make more sense had her emails not been hacked...
ReplyDeleteYou would think that with the Power of holding "50,000 Keys" this Simple Moron could spare a few to her Useful Idiots...
Nice eye catching Headline on a baseless story...
I'm thinking that also with the ability to control as much as you claim, this Hideous Whore would be the last person anyone would trust with that capability...
And surely with the new administration, it would be corrected as with the rest of the incompetent bullshit that has taken place...
Oh my goodness! Incredible article dude! Thanks, However I am having troubles with your RSS.
ReplyDeleteI don't understand the reason why I am unable
to join it. Is there anybody else getting identical RSS issues?
Anyone who knows the answer will you kindly respond?
Thanks!!