Cisco CEO John Chambers built back doors into his I nternet routers, donated $5 million to The Clinton Foundation, and paid $1 billion into the Obama/Hillary "Russian Reset"


Assistant U.S. Attorney; Mueller Russia probe appointee; JPMorgan attorney; failed to prosecute any Wall Street executives
[*] Goldstein's work history at Paul Weiss LLP before 2010 is very evidently censored.
ORIGINAL POST
(Jun. 30, 2017)—On Jun. 19, 2017, President Trump hosted a roundtable of technology and academic elitists. Perhaps unknown to President Trump and his agency heads is the fact that these companies have been working for decades to undermine the American Republic in favor of a globalist New World Order run by unelected bureaucrats and multi-national corporations.
The original authority for this Deep State shadow government Internet collusion is Executive Order 13231 which has been renewed six times by Presidents Bush and Obama. It is due for another renewal on Sep. 30, 2017 as Executive Order 13708.
If Executive Order 13708 is not renewed by Sep. 30, 2017, these Deep State conspirators will be officially rogue—having lost their dubious legal authority to support the White House's National Security Staff (NSS). These devious individuals have hidden their collusion in a mountain of government intelligence legalese that promotes "public-private partnerships"—in the name of national security, of course. Their collusion has been cleverly hidden from Congress and the public by stamping "classified" on almost everything they have done since Bill Clinton came to power in 1993. According to former Defense Secretary Robert Gates in his book Duty (2014), the NSS staff ballooned from 50 in 1993 to over 350 in 2016 under Obama. That is a lot of spies running around in the White House! Are they doing The People's business? That is doubtful.
The question is, for whom have they been spying? The answer is evident: Deep State globalists working for a U.N. New World Order run by the very multinational corporations, academics, intelligence agencies and media who comprise this "public-private partnership" of elitist spies.
The NSS is a rogue C.I.A. spy operation run out of the White House without Congressional oversight to which the 17 other intelligence operations, including the NSA and FBI, are subservient.
The NSS has numerous tentacles into policy, funding, intelligence, media, academia, judicial, research and development—all sustained by a long string of dubious "national security" executive orders from Bill Clinton through George Bush and Barack Obama. Note: AFI researchers interviewed a very prominent member of the judicial community in preparation for this post. He had no awareness of this unConstitutional exploitation of intelligence executive orders. Therefore, spread the word.
- Policy & Funding—National Infrastructure Assurance / Advisory Council (NIAC) and the “safe harbor” concept to get around the Fourth Amendment, which prohibits unreasonable searches and seizures. It requires governmental searches and seizures to be conducted only upon issuance of a warrant, judicially sanctioned by probable cause.
- R&D—The IBM Eclipse Foundation and theft of social networking invention from Leader Technologies to get around the Fifth Amendment, which protects personal property from confiscation by the government without fair compensation.
- Funding—Wall Street, offshore money laundering & drugs. See HSBC / SwissLeaks / Comey / Mueller. See also The Panama Papers.
- Media— NPR, New York Times, CNN, Washington Post hide behind the First Amendment to disguise their role as Deep State propagandists. See backdoor keys.
- Blackmail—C.I.A., FBI, NSA, use of pedophilia & ritual child sacrifice
- Academia—Harvard, Yale, Stanford, Columbia, GWU, Ohio State M.O.O.C. (Massive Open Online Course—Deep State takeover of universities), Carnegie Mellon
- Judicial—Secret FISA Court exploitation and the “safe harbor” mutual fund concept for hiding bribery of judges and getting around judicial ethics prohibitions against the 'appearance of impropriety'
The White House roundtable participants gather regularly around the world in various forums (likely seditious) to further their anti-American globalist agenda in places like Bilderberg, Davos, Tri-lateral Commission, In-Q-Tel, IBM Eclipse, NIAC, NVCA (National Venture Capital Association), World Bank, IMF, Federal Reserve, Council on Foreign Relations (CFR) and the Brookings Institution.
"Ok, Houston, we've had a problem here"
This was the message that Apollo 13 Command Module Pilot Jack Swigert radioed to earth after an explosion in their spacecraft.
This Roundtable group almost universally backed Hillary Clinton for President. A president Hillary would have renewed Executive Order 13708 by Sep. 30, 2017.
However, without that renewal, the decades of digital sedition that has hidden under these executive orders will officially go rogue. The roundtable group members will have no legal authority to operate their warrantless surveillance of Americans and their unConstitutional theft of our privacy.
Said another way, the decades of collusion that have led us to the cliff of The New American Surveillance State will have no legal legitimacy whatsoever come Sep. 30, 2017.
Indeed, like Apollo 13, these conspirators just heard an explosion inside their own “command module.” They have a serious problem.
After September 30, 2017, unless President Trump offers them some sort of amnesty these people will be in trouble. They will need to disclose anyone who is 'blackmailing' them, or their Deep State collusion will likely land substantial numbers of the technology world in prison for treason and sedition. Indeed, former C.I.A. leader turned whistleblower Robert David Steele recommends that President Trump implement such a "truth and reconciliation" program to help fix the rampant rogue spy-generated blackmail that has overtaken our public institutions.
Officially criminals after Sep. 30, 2017
On Sep. 30, 2017, all of the companies and individuals who have colluded with the rogue C.I.A. / NSA / FBI and NSS in the White House to spy illegally on the American people will be officially criminals because they will no longer have the dubious executive order protections they have relied on since 1999 when these shadow government executive orders were instituted. (The first version of the NIAC, Executive Order 13130 was implemented by Bill Clinton on Jul. 14, 1999.)
How bad is it?
President Trump asked each Roundtable participant to introduce himself or herself. AFI researchers have compared that list of attendees to various other collusion membership lists compiled for the AFI TIMELINE:
People you trusted are now hijacking the Internet.
What emerged is a list that we have named the “Deep State Hive Mind Index.” "Hive mind" as in "groupthink." We have hard evidence of this groupthink, in which the desire for harmony or conformity in the group results in an irrational or dysfunctional decision-making outcome. We believe this explains the globalist New World Order elitist drive to seize power and control, at all costs.
The Deep State Hive Mind Index
We coined the term “Deep State Hive Mind Index” as a way to determine the relative contributions of the various actors involved in this massive collusion. Clearly, some of these players are more central to this hive mind than others.
Membership in the following Deep State shadow government activities were each given a “1” value, and Clinton speaking fees were given a “1” for each speech. Ohio State's Trustee President Jeffrey Wadsworth manages numerous intelligence units as CEO of Battelle Institute and therefore classifies Ohio State as a C.I.A. agent.
Ohio State is also the network hub for M.O.O.C. (Massive Open Online Course)—an evident agent of the Deep State shadow government to steal university research data and brainwash students using advanced C.I.A. MKUltra mind control techniques like virtue signaling and trolling. MKUltra never stopped despite Congress' order to shut it down. "Conspiracy theory!" you say? Open your eyes. Such reactions have been effective in hiding this diabolical program in plain sight. This is not 'conspiracy theory' if it is true. See FBI superstar Agent In Charge Ted L. Gunderson whistleblower revelations.
Criteria for the creation of the Index below:
- Policy & Funding: National Infrastructure Assurance / Advisory Council (NIAC), the “safe harbor” concept to circumvent 4th Amendment privacy protections; safe harbor protections will expire on Sep. 30, 2017 which will likely and immediately expose all NIAC contributors to treason and sedition charges
- FBI backdoor: On Jun. 07, 1993, Podesta and James Chandler sponsored CRYPTO 1993 to give the FBI a backdoor key to the Internet
- Judicial bribery: the “safe harbor” mutual fund concept
- R&D: IBM Eclipse Foundation and the theft of Leader Technologies’ social networking invention
- NSA backdoor encryption: NIST registration of backdoor keys. See also Dell ships backdoor keys
- Financing: In-Q-Tel / C.I.A. / Wall Street / Silicon Valley
- Gov’t contracting: using procurement to enforce conformity to the rogue agenda
- Blackmail data collection: Warrantless Surveillance (Snowden)
- Blackmail exploitation: Obama donors and insiders. See Feb. 17, 2011 and Mar. 02, 2015.
- Blackmail exploitation: Clinton Foundation donors and insiders. See also The Clinton Chronicles
| No. | WH Roundtable Participants Jun. 19, 2017 |
Deep State Hive Mind Rating |
| 1 | [Cisco] (conspicuously absent, see below) | [15] |
| 2 | Oracle | 11 |
| 3 | Facebook, Clarion, Palantir / CIA | 10 |
| 4 | IBM / CIA | 10 |
| 5 | Microsoft | 10 |
| 6 | Amazon, Washington Post / CIA | 8 |
| 7 | Apple | 8 |
| 8 | Google, Alphabet | 8 |
| 9 | Kleiner Perkins / CIA | 8 |
| 10 | Ohio State / Battelle / CIA | 8 |
| 11 | Palantir, NSA, In-Q-Tel / CIA | 8 |
| 12 | Qualcomm | 8 |
| 13 | Carnegie Mellon U, Hoover Institution, Stanford | 7 |
| 14 | Intel | 7 |
| 15 | MIT | 7 |
| 16 | VMWare, Dell, EMC | 7 |
| 17 | Accenture | 6 |
| 18 | Akamai | 6 |
| 19 | MasterCard / AOL | 6 |
| 20 | SAP | 6 |
| 21 | Adobe | 5 |
| 22 | OpenGov | 5 |
| 23 | UNC | 5 |
Table 1: White House Technology Roundtable Participants (Jun. 19, 2017). |
||
What is the Deep State Hive Mind?
One notable trend among these collaborators is their near universal involvement in the IBM Eclipse Foundation started on Nov. 29, 2001. This foundation distributed the social networking invention of Columbus innovator Leader Technologies at no charge to the entire tech community. Of course, embedded in that code were Deep State requirements for backdoor keys and quid pro quo data sharing.
Sacrificed morals for power and money
Evidently, these people sacrificed their morals and ethics to establish this unconstitutional and depersonalized “Internet of Things” to spy on you and steal all your best ideas to exploit among the hive mind elitists.
These people are like a hive of drone bees buzzing around their corrupt Queen Hillary.
Tellingly, Barack Obama even promoted the “Internet of Things” in his Executive Order 13718. They probably thought no one was paying attention.
Misprision of a Felony: Did the roundtable participants commit a felony by not disclosing their Deep State collusion to the President?
The law is clear. It is a felony to have knowledge of fraudulent activity involving a contract with the federal government and not disclose it.
18 U.S. Code § 4 - Misprision of felony
“Whoever, having knowledge of the actual commission of a felony cognizable by a court of the United States, conceals and does not as soon as possible make known the same to some judge or other person in civil or military authority [including the President and his agency chiefs] under the United States, shall be fined under this title or imprisoned not more than three years, or both.”
Each of these Deep State participants has contracts with the federal government.
By remaining silent about their decades of fraud and crony capitalist collusion, is not each person who introduced himself or herself to President Trump guilty of misprision of a felony? In the opinion of our legal experts, yes.
Why was the Deep State digital kingpin Cisco absent? Good Question.
Conspicuously absent from the White House meeting is one of the Deep State kingpins—Cisco and its chairman John T. Chambers.

Facebook director & major shareholder, funded Zuckerberg's first $500,000 in 2004, founder of PayPal, co-founder of Palantir NSA / C.I.A. spy software
We digress for just a moment to give readers more context for the insidious Washington, D.C. corruption machine. Also missing the roundtable was Facebook's Zuckerberg or Sandberg. However, since Peter A. Thiel is a director and major shareholder of Facebook, they were present, even if not introduced. This does not even consider that all or nearly all of the companies who did attend collude with Facebook. See Jim Cramer's CNBC rant about Peter Thiel's unethical sale of Facebook IPO stock on May 22, 2012. Also present were former Goldman Sachs executives who were the primary underwriters for the Facebook stock offering that substantially funded the Deep State.
The Facebook initial public offering provided hundreds of billions of dollars for the Deep State's campaign of bribery and collusion. For example, all of the Leader v. Facebook judges cashed in.
Remember, the real purpose of Facebook and Google is to be a rogue C.I.A. global spy data collection system for the Deep State shadow government to manipulate and control you—the wolf—who comes into your home dressed in the sheep's clothing of coupons, titillation and baby pictures—very devilish, insidious and effective. Isn't that right Alexa? (The voice of Google Home.)
News Update! Jul. 09, 2017: Snowden NSA documents prove Cisco, IBM, Google, Facebook helped lead the Deep State takeover
![Greenwald. (May 14, 2014). Snowden NSA archive Documents from No Place to Hide, PDF page 12. Glenn Greenwald / MacMillian. (Glenn Greenwald, p. 102: "NSA Strategic Partners, Alliances with over 80 Major Global Corporations Supporting both Missions: Telecommunications & Network Service Providers, Network Infrastructure, Hardware Platforms Desktop/Servers, Operating Systems, Applications Software, Securty Hardware & Software, System Integrators: AT&T, CISCO, EDS, H-P [HP, Hewlett-Packard], IBM, Intel, Oracle, Qualcomm, Microsoft, Motorola, Verizon").](https://www.fbcoverup.com/docs/library/2014-05-14-Snowden-NSA-archive-Documents-from-No-Place-to-Hide-Page-012-Glenn-Greenwald-MacMillian-May-14-2014.jpg)
Cisco updated switch software to fix rogue NSA problems
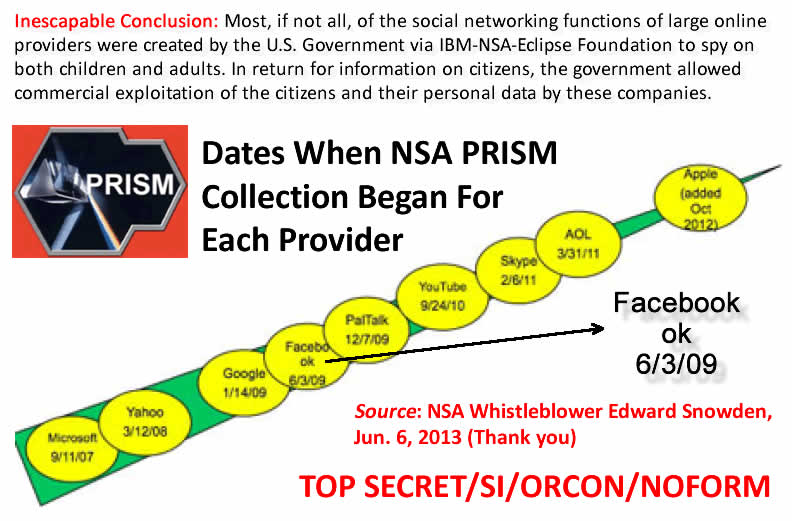
Deep State social spy net: social providers agreed to share their user data in exchange for profits
Rogue C.I.A. / NSA Lawless Admission: "Exploit it All"
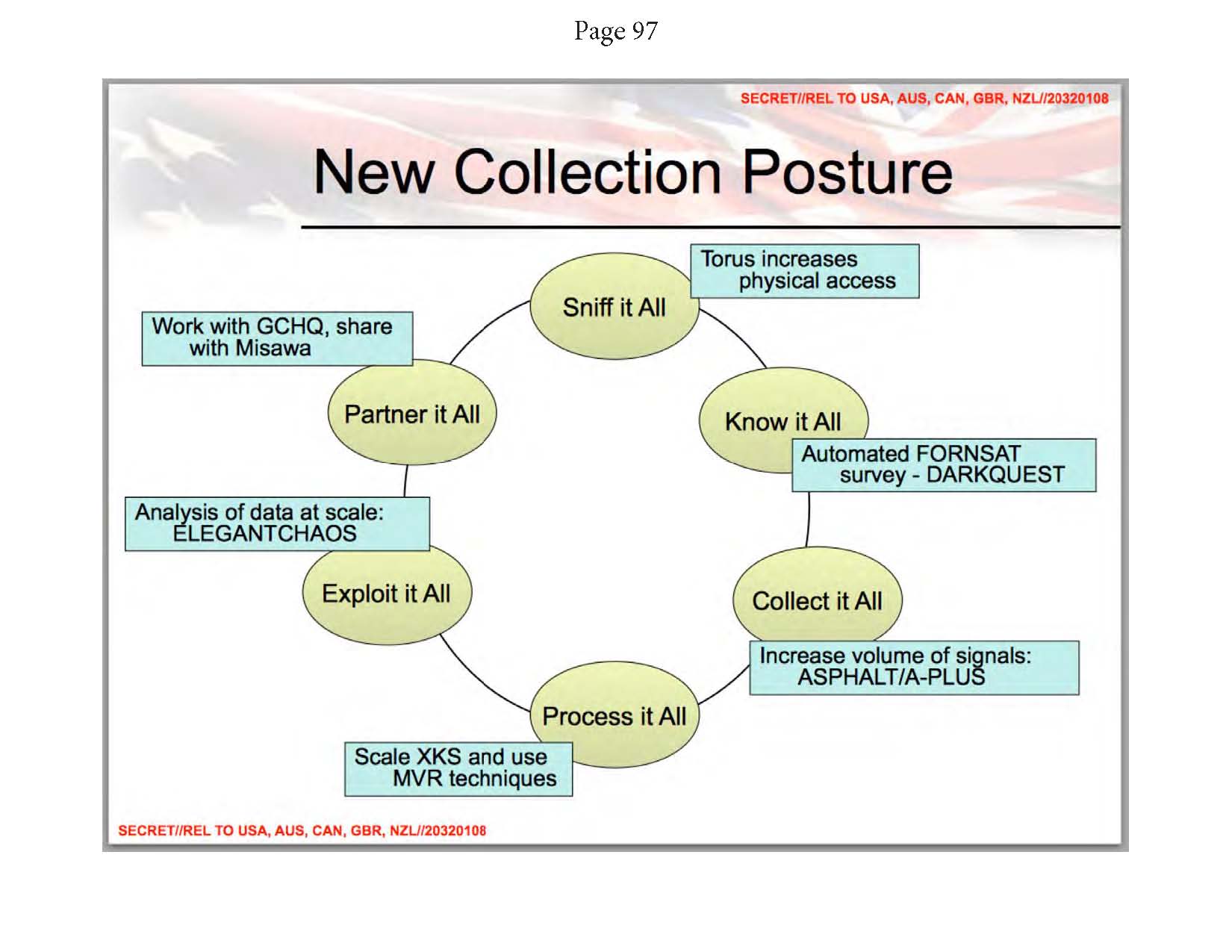
Deep State colluders admit racketeering: "a lot of money being made by U.S. entities"
See TIMELINE for more Snowden proofs of government collusion with the private sector -- unConstitutional crony capitalism at its zenith. (Please be patient! The Jun. 06, 2016 bookmarked timeline entry for Edward Snowden will load automatically.)
Cisco has helped lead the Deep State technology collusion
From 2002-2006 Cisco’s CEO John T. Chambers was vice chair of the National Infrastructure Assurance Council (NIAC) started under Bill Clinton as the main policy arm of the rogue C.I.A.’s takeover of the Internet. It was during this period that IBM and Cisco conspired with the rest of the technology world to steal Leader Technologies’ social networking invention and convert it to a global spying platform.
These were also the formative years following the Deep State’s rogue C.I.A. orchestration of the 9/11 false flag and The Patriot Act. This council was established under Clinton/Podesta in 1999 and tasked to set policy for the Deep State shadow government's “Internet of Things” global spy grid.
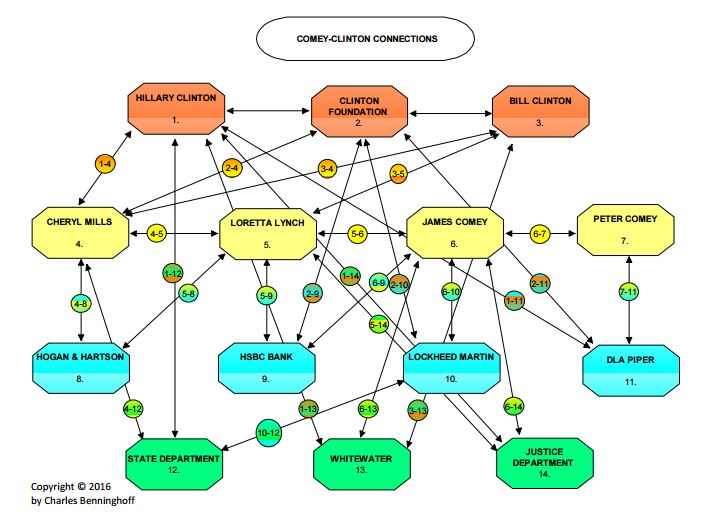
Cisco’s timeline shows that they were helping lead the development of the rogue C.I.A. surveillance system—almost completely outside the oversight of Congress and the American People. It also shows that Cisco has been a central figure in the Clinton-Obama-Soros-Russia axis:
Bookmark: #chambers-cisco-treason-sedition| Cisco/Chambers score the highest—15 on the Deep State Hive Mind Index (see Table 1) | |
| 1993 | Steven Wolff (later Cisco) collaborated with the Clintons, Podesta, Summers, Sandberg, Albright, Milner and World Bank to give the FBI a backdoor encryption key to all digital traffic and content; media attending were: NPR, New York Times, Washington Post |
| 1997 | Chambers/Cisco teamed with IBM, Microsoft, Intel and Wind River to build backdoors into all hardware and firmware for the "Internet of Things" offshore, in Italy, via Eurotech, Ltd. |
| 1999 (Jul 14) | Chambers/Cisco secret member of NIAC, v. 1 (Executive Order 13130, under Clinton) |
| 2001 (Oct 16) | Chambers/Cisco, secret member, NIAC, v. 2 (Executive Order 13231, under Bush) |
| 2001 (Nov 29) | Chambers/Cisco, secret member, IBM Eclipse Foundation |
| 2002-2006 | Chambers/Cisco, appointed vice chairman of NIAC (under Bush) |
| 2005 (Sep. 02) | Bill Clinton broker the UrAsia uranium mining rights in Kazakhstan for friend Frank Giustra |
| 2006 (May 18) | Chambers/Cisco paid Bill Clinton $150,000 for speech in Monterey, CA |
| 2006 (Aug 17) | Chambers/Cisco paid Bill Clinton $150,000 for speech in Las Vegas, NV |
| 2007 (Feb 12) | Bill Clinton's friend Frank Giustra sold UrAsia uranimum mining to Uranium One for $3.1 billion |
| 2007 (Mar 29) | Chambers/Cisco paid Bill Clinton $100,000 for speech in Kiawah Isl., SC |
| 2008 (Sep 09) | Chambers/Cisco, public member, IBM Eclipse Foundation |
| 2009 (Sep 22) | Chambers/Cisco donated up to $5,000,000 in Clinton Foundation. See donor list (fn. 320) |
| 2010 (Dec 29) | Hillary identified Cisco in stonewalled emails on her illegal private server along with other Deep State Hive Mind conspirators Yahoo, Ebay, Semantec, MicroTech, FCC, Ford Foundation, Microsoft, Apple, Safaricom, Ushahidi, Twitter, Square, Google, Mobile Accord, Carlos Slim, HowCast, Mo Ibrahim Foundation, Mextel, NYU, Harvard. The notes of this speech were redacted as CLASSIFIED by the State Department |
| 2010 (Jun 27) | Chambers/Cisco committed $1,000,000,000 (one billion) in Skolkovo, Russia to Obama/Hillary’s 'Russian Reset' along with other funds from IBM, Google and Intel—now this is REAL RUSSIAN COLLUSION! |
| 2010 (Jun 29) | Renaissance Capital, Moscow, Russia, Uranium One underwriter with close Kremlin ties, paid Bill Clinton $500,000 for a speech. |
| 2010 (Dec 17) | Secretary of State Hillary Rodham Clinton presented Cisco with the Secretary of State’s 2010 Award for Corporate Excellence (ACE). |
| 2011 (Feb 17) | Chambers/Cisco guest of Barack Obama at an excluse Silicon Valley elitist dinner |
| 2011 (Apr 10) | Vladimir Putin's Rusnano company, Moscow, Russia, invested $35 million in Joule Unlimited where John Podesta was a director |
| 2013 (May 29) | Chambers/Cisco bought Joulex, Thomas E. Noonan, CEO; also long-time IBM shadow executive, and founding member of NIAC |
| 2014 (Aug 28) | Chambers/Cisco paid Hillary Clinton $325,000 for speech in Las Vegas, NV. |
| 2016 (Jan 14) | Chambers/Cisco given special access to Hillary Clinton at the State Department; admitted NSA penetration; pretended they were not partnered with the NSA |
| 2016 (Aug 16) | Chambers/Cisco admitted to building in C.I.A. / NSA / FBI encryption backdoors in Internet switches for many years |
| 2017 (Mar 21) | Chambers/Cisco admitted "critical bug" in 318 Internet switches to hide their decades of Deep State collusion with the NSA / C.I.A. / FBI shadow government; fails to admit these were features built in for the rogue C.I.A., not bugs. |
| Table 2: John T. Chambers, Chairman & CEO, Cisco Systems collusion with Barack Obama, Bill and Hillary Clinton and New World Order Deep State shadow government globalists. | |
How do we know the Deep State abused their bureaucratic power?
The NIAC’s own internal PowerPoint said that’s what they were doing—by design. They clearly state that they will essentially bribe vendors with government contracts to get compliance with the plan:

ZIPPED archive of NIAC Quarterly Business Meeting Minutes from Nov. 26, 2002 to Sep. 16, 2016 (last accessed Jun. 28, 2017) (24.7 MB).
This circumstance is EXACTLY what President Dwight D. Eisenhower warned about in his farewell address to the nation on Jan. 17, 1961.
The military-industrial complex hive members have become New American Tyrants
Bookmark: #eisenhower-warningThese criminals control the mainstream media as their propaganda arm, as Roger Stone so clearly describes in this video just released yesterday.
Bookmark: #roger-stone-on-free-speechConclusion
We the People must reassert our power over these criminals who have hijacked so much of our country in their stealth.
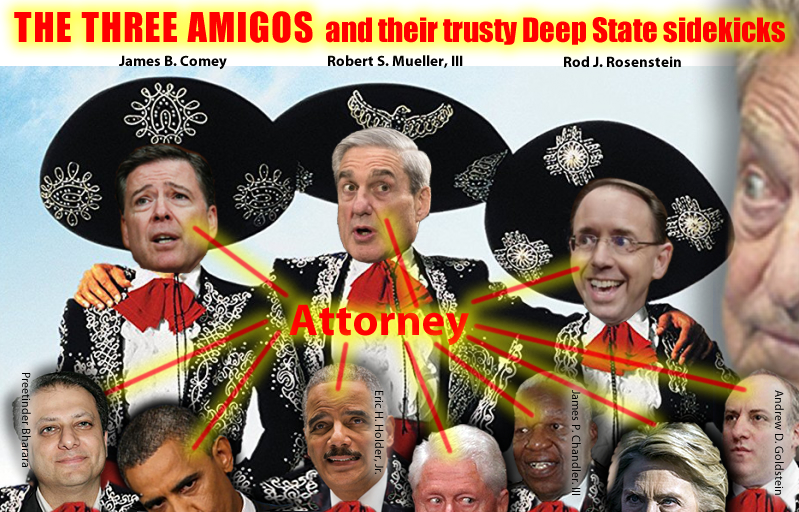
Fig. 11: Roger Stone. (Jun. 22, 2017). Mueller, Rosenstein, and Comey: The Three Amigos from the Deep State. StoneColdTruth.com.
Notices: This post may contain opinion. As with all opinion, it should not be relied upon without independent verification. Think for yourself. Photos used are for educational purposes only and were obtained from public sources. No claims whatsoever are made to any photo.
Comment
Click "N comments:" on the line just below this instruction to comment on this post. Alternatively, send an email with your comment to amer4innov@gmail.com and we'll post it for you. We welcome and encourage anonymous comments, especially from whisteblowers.