Therefore, the argument that Obama did not order the wiretapping a.k.a. surveillance of Donald Trump is more fake news deception. He ORDERED it on everybody, including Donald Trump, his family, friends and colleagues. The parsing of words that he may not have said "Donald Trump", his chief political enemy, specifically, is ridiculous given the FACTS of the Stellar Wind, surveillance program, or whatever it is called now, run out of the White House.
Read the Office of Inspector General's (OIG) Jul. 10, 2009 assessment of the "Stellar Wind" illegal surveillance program:
Vol. 1 (82 pgs, 19.3 MB)
Vol. 2 (240 pgs., 38.5 MB)
Vol. 3 (424 pgs, 118 MB).
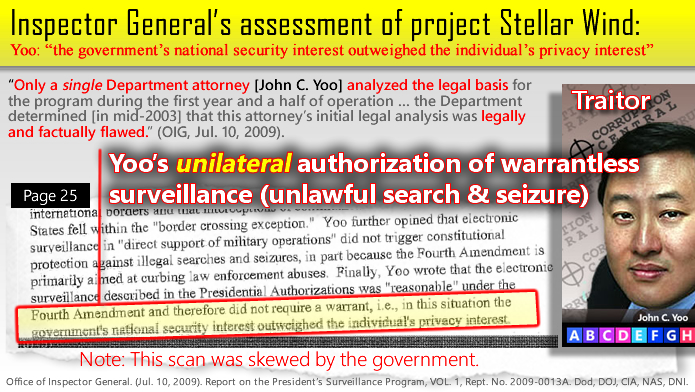
The document provided by a FOIA release employed all the usual unscrupulous lawyer tricks. The heavily redacted documents were unsearchable. Key pages were heavily skewed (as seen below on perhaps the most damning disclosure in the 674 page document) to escape optical readers. All those impediments have been fixed in the download links above. The documents are now searchable. The arrogance of the Deep State is evident in the quotes below from the Inspector General's scathing report on the absence of normal checks and balances for a subject as serious as our fundamental privacy protections in the Bill of Rights.
ORIGINAL POST
(Mar. 26, 2017)—You cannot make this stuff up. Readers are encouraged to follow these facts where they lead, then act to preserve our Republic from this Deep State takeover attempt.
Facebook’s Mark Zuckerberg is growing increasingly bold in his arrogance. He forces native Hawaiians off their land. He builds high fences around his Silicon Valley compound while decrying a border wall. He implements Chinese-style censorship while declaring Facebook to be transparent. This arrogance appears to emerge from a belief that his crimes will never be punished and that he is above the law.
The House Intelligence Committee should investigate Zuckerberg and analyze his 28 stonewalled computers, now.
Yesterday, we asked Michael McKibben, the true inventor of social networking and founder of Columbus-based innovator Leader Technologies, Inc. to review documents from WikiLeaks Vault 7: DEEP MATTER.
Specifically, we asked him about a leaked C.I.A. document named “Triton 1.3 User Guide.” According to the guide, "Triton is an automated implant" designed to hijack target Mac computers for data extraction. In more familiar terms, Triton is very sophisticated malware used by the C.I.A. to completely takeover Apple computers.
The Triton 1.3 User Guide describes how the C.I.A. infects Apple Macs (other related user guides target iPhones) via “Listening Posts” in the Internet to which “Beacon” programs installed on smart phones and computers send data and receive instructions for further intrusion of an “infected target” device.
McKibben said “just substitute the words ‘social platform’ for ‘Listening Post’ and ‘app’ for their ‘beacon’ and it is easy to understand that the Triton 1.3 manual describes illegal surveillance using social apps in the Internet.”
Also identified in the document is DROPBOX as the "cloud" data repository for stolen user data.
C.I.A.'s own document admits illegality of Triton 1.3
“The manual even admits that the C.I.A. knows what they are doing is illegal."
"They use the word ‘Exfiltration’ in one of their headers. Exfiltration means unauthorized access to a computer and data theft, generally by cyber criminals,” McKibben continued.
He confirmed that Leader’s invention is described in the Triton 1.3 document.
McKibben said “earlier we obtained whistleblower evidence that proves C.I.A. agents had orchestrated the theft of our social networking invention in 2001—at the founding of the IBM Eclipse Foundation on Nov. 29, 2001 with a $40 million IBM donation to promote “open source.” See TIMELINE for People you trusted are now hijacking the Internet.
McKibben added, “almost anyone in technology knows that using the words ‘IBM’ and ‘open source’ in the same sentence is a joke. IBM owns more patents than any other company on the planet. They are anything but open source where everything is free. So what was Eclipse giving away if not IBM’s secrets? Leader’s stolen invention, obviously. Hindsight is 20-20.
Clearly, IBM formed the Eclipse Foundation to distribute our social networking invention to the technology world so long as those companies gave the IBM Eclipse C.I.A. handlers a backdoor key for mass surveillance. Most assuredly, these C.I.A. rogues held out the promise of future government contracts in exchange for these technology companies turning a blind eye to their abuse of the Bill of Rights.”
“Another ‘coincidence’ is the fact that our patent attorney in 2001, James P. Chandler, was also IBM’s chief outside intellectual property counsel. IBM’s inside counsel at the time, David J. Kappos, was appointed Patent Office director in 2009 by Obama,” said McKibben.
IBM Eclipse Foundation started giving away Leader’s social networking invention in 2001, just as the NSA fired William Binney, the architect of the NSA’s lawful surveillance system.
IBM Eclipse gave away Leader’s invention in 2001, while NSA fired Binney
NSA whistleblower William Binney points to 2001 as the time when the NSA went rogue. McKibben continued “it seems obvious that the rogue C.I.A. group who stole my social networking invention wanted to replace William Binney’s earlier platform architecture with ours.” Binney ‘retired’ in Oct. 2001, just one month before the IBM Eclipse Foundation started with IBM, Chandler, Kappos driving the bus.”
McKibben said that it was well known at the time that Chandler was also consulting closely with then Assistant Attorney General Eric Holder.
McKibben said investigators have been hard at work in the days since the U.S. Supreme Court refused to consider the Leader v. Facebook appeal in Jan. 2013, thus protecting Facebook.
“Being red-blooded Americans who inherently respected our courts and judges, we were stunned that our highest judges would just ignore the law and precedent in favor of Facebook’s crimes that we had just PROVED with mountains of evidence and expert testimony. The lower federal court jury actually RULED that Facebook was GUILTY of infringing all eleven patent claims. What we witnessed was patent theft by the judiciary!”
"We were suckered by Bill Clinton's chief intelligence and national security attorney, James P. Chandler, who pretended to be our attorney while he was sucking us dry."

By way of metaphor, McKibben said about their research to figure out where this corruption led, “for the longest time we would open the door on a subject area in our investigation, like Zuckerberg’s 2003-2004 computers and Harvard emails, and catch glimpses of shadowy figures darting out of the room. This has happened maybe 500 times now.”
Each time, the researchers would note the occurrence on a jigsaw puzzle piece, lay it on the table and move on.

McKibben said that when they added the new research to evidence they already had, some pieces started fitting together. Patterns emerged. Our suspicions began to grow as we continued to focus on hard evidence.
“Then, we started learning about whistleblowers and watchdogs, including William Binney, J. Kirk Wiebe, Tom Drake, Ed Loomis, Diane Roark, Edward Snowden, Julian Assange, WikiLeaks, Guccifer, Marcel Lehel Lazar, Guccifer 2.0, DCLeaks, Dinesh D’Souza, Tom Fitton, Judicial Watch, HSBC Swiss Leaks, Hervé Falciani, ICIJ, Open Secrets, Center for Public Integrity, Lawless America, True the Vote, Center for Self Governance, Mark Herr, David Knight, Daily Caller, ZeroHedge, Tyler Durden, Larry Hagmann, Larry C. Johnson, Mike Cernovich, The Panama Papers, Larry Klayman, The Intercept, Glenn Greenwald, Freedom Watch, Alex Jones, Infowars, Steve Pieczenik, Empire Files, Abby Martin, Roger Stone, Peter Schweizer, Matt Drudge, Andrew Breitbart, Joseph Farah and WorldNet Daily, and others.” See Real News links.
“The more we learned, the more the previously shadowy figures became actual names and faces.”
Takedown of the Republic
McKibben said that while Leader was focused on understanding the misconduct of Facebook and the senior federal judiciary in Leader v. Facebook, a larger context emerged. He said, "we began to realize we had a front row seat watching the takedown of the American Republic by 'one world order' globalist forces.”
He said certain keywords and phrases began to shout at their investigators:
C.I.A., NSA, FBI, In-Q-Tel, Goldman Sachs, Morgan Stanley, JPMorgan Chase, Kleiner Perkins, Greylock, Accel Partners, Fidelity, Vanguard, T. Rowe Price, executive orders, conspiracy, collusion, blackmail, money laundering, globalism, Saul Alinsky, bribery, collusion, Wall Street bankers, Harvard Law, Yale Law, Stanford Law, GWU Law, Georgetown Law, stonewalling, arrogance, pedophilia, snuff parties, Silicon Valley venture capitalists, Big Data, China, uncontrolled immigration, The Internet of Things (IoT), new world order, encryption backdoor keys, new communism, mind control, eugenics, wiretapping, warrantless surveillance, deceptive licensing, media manipulation, election rigging, Glass-Steagall, Mena, net neutrality, election rigging, fake news, ICANN, TPP, TiSA, FISA Court and corruption.
Zuckerberg’s 28 computer hard drives will show collusion with the rogue C.I.A.
During the Leader v. Facebook trial―all through 2009 (while Hillary Clinton was ceding State Department control to George Soros)—Zuckerberg and Facebook stonewalled providing Leader’s attorneys access to Zuckerberg’s 2003-2004 computer devices and emails.
Judicial Watch recently uncovered secret contracts related to that same time. Then Secretary of State Clinton contracted with Facebook to write election manipulation software―which is obstruction of justice.
On the eve of Facebook being ordered to produce Zuckerberg's 2003-2004 computers in late 2009, Facebook suddenly changed attorneys to Cooley Godward LLP (Obama’s energy stimulus promoter). Then, the year-long stonewalling excuses magically transformed into “we cannot find them.” Judge Leonard P. Stark who presided over the Leader v. Facebook trial let them get away with it.
Nonetheless, Leader proved patent infringement at the federal trial on 11 of 11 claims in July 2010. However, Judge Leonard P. Stark then fabricated facts and ruled for Facebook anyway. Stark’s technicality is laughable if it were not so sad. He pulled out a Civil War era criminal decision to justify his actions—a law that had never in history been applied to a civil patent case. His best argument was that it was "not impermissible" for him to use the 120-year old case for the first time in his unprecedented way—a way that defied well-settled patent precedent.
Leader appealed to the Federal Circuit Court of Appeals in Washington, D.C. that hears all patent appeals. Hindsight shows that the Federal Circuit unfortunately has many globalist actors. They continued to protect Facebook even though all three judges had Facebook financial interests and cozy relationships with Facebook’s lawyers. Facebook’s Gibson Dunn LLP appeal attorney, Thomas G. Hungar, had even REPRESENTED those same judges in an ethics complaint that year (2010).
Zuckerberg's Magical resurrection of his 28 “lost” computers
Two days after the Federal Circuit ruling against Leader, 28 Zuckerberg computer devices and Harvard emails magically surfaced in another case against Facebook—Ceglia v. Zuckerberg.
Overnight the Facebook story on Zuckerberg’s hard drives flipped 180 degrees from being “lost” to having 28 of them! Why Facebook thought they were safe from Ceglia's claims in disclosing the 28 computer devices is baffling. Ceglia is a victim of the C.I.A./Facebook treachery, just like Leader. It is clear that Zuckerberg signed two contracts with Ceglia to stall him from introducing a college “facebook” at Harvard until Zuckerberg / IBM / C.I.A. were ready to launch with Leader's invention, which they did on Feb. 4, 2004.
Facebook’s crooked attorney:
Gibson & Dunn LLP
More telling, Zuckerberg’s 28 computers and Harvard emails were in the custody of Gibson Dunn LLP, Facebook’s appeal attorney, the entire time. They were never lost as Facebook claimed at the Leader v. Facebook district court trial. This is still more proof of fraud and obstruction of justice.
Suggestion to the House Intelligence Committee on the alleged Russian meddling:
Impound and forensically analyze Zuckerberg’s 28 computer devices held by Gibson Dunn LLP—before they disappear

Clinton, Podesta, Summers, Sandberg: the Real Russian Collusion
The facts show that three Clinton and Obama confidantes, Larry Summers, John Podesta and Sheryl K. Sandberg have been intimately involved with certain Russian oligarchs since the early 1990’s—before Vladimir Putin became President. These people then played pivotal roles in the emergence of free Email and free social networking in Russia and America. Since the election of Donald Trump, these same people are now moving their illegitimate companies toward Orwellian levels of free speech censorship.
Prominent among these relationships are two Russian oligarchs, Yuri Milner and Alisher Usmanov. Both Milner and Usmanov were multiple billion dollar winners in the Facebook initial public offering in May 2012. While one may expect corruption from these Russian oligarchs as their way of life, Summers, Podesta and Sandberg are supposed to follow U.S. laws. See Hillary's Secret Offshore Empire.
Summers’ “Big Bangery” and “Globalbaloney” Harvard “advice” to a collapsing Soviet economy (under Anatoly Chubais (Rusnano, pre-Putin))
Economist David Ellerman wrote sarcastically about Summers’ “ersatz policy” for World Bank privatization of the former Soviet economy in the early 1990s. Hindsight shows that Summers lined his pockets handsomely while his reckless recommendations for the Soviet economy failed miserably and gave rise to the current system of corrupt Russian oligarchs.
Bookmark: #podesta-putin-joule-rusnanoSummers hired Milner along with his former student, Sheryl K. Sandberg, to work for him at the World Bank, after he left Harvard in 1991.
Sandberg followed Summers to the Treasury Department as his chief of staff after Bill Clinton’s election in 1993. Curiously, in late 1992—just six weeks before Bill Clinton's election—George Soros almost crashed the British Pound and pocketed $1 billion into his hedge fund and his new Open Society Foundations. See also George Soros: The epic global meddler.
Milner's bank Menatep acquired $14.8 billion for the globalist agenda
Milner moved back to Russia, then popped up in the late 1990s’ enmeshed in two banking scandals—about the time then Treasury Secretary Summers obliterated Glass-Steagall banking controls. Milner was implicated in the diversion of $4.8 billion in IMF funds and $10 billion in Russian mob money laundering by the Russian Bank Menatep. See Congressional Briefing.
Takeover of email and social networks in Russia & America—Gmail, Mail.ru, Facebook, VK
By 2004, Sandberg was assigned to start Google Gmail, then became COO of Facebook in 2008. Milner was assigned to start Mail.ru, the Russian equivalent of Gmail, then later VKontakte (VK), the Russian equivalent of Facebook. The coincidences are legion among this clutch of globalists. Clearly, control of email and social networking was key to their strategy.
It is now evident that a rogue C.I.A. group, begun under Bush Sr. (1989-1993), then got organized under Clinton (1993-2001), shifted to the new social networking mass surveillance under Bush (2001-2009), then exploited the platform to amass great wealth and control under Obama (2009-2017).
Clearly, the Milner-Usmanov-Summers-Clinton-Sandberg Russian connections have been corrupting world digital networks for a very long time. The WikiLeaks documents prove they have been spying on everyone for decades. Therefore, this “Russians did it” accusation against Donald Trump and his supporters is absolute nonsense.
These Clinton-esque associations with Russia occurred even before Vladimir Putin came to power as President of Russia.
Zuckerberg’s 28 hard drives will reveal the beginnings of Deep State's mass surveillance
What will Zuckerberg’s 28 hard drives and Harvard emails reveal?
1. Real Russian Connections: They will prove the real Russian connections that formed the basis of the Deep State shadow government’s mass surveillance network currently being criminally used against Donald Trump and his supporters, including Roger Stone, General Michael Flynn, Paul Manafort, Sen. Rand Paul and others.
2. Facebook’s rogue C.I.A. handlers: The identity of his C.I.A. handlers will be revealed
Prediction: This will include the “PayPal Mafia” who were in bed with the Deep State, including James W. Breyer (Accel Partners), Reid Hoffman (LinkedIn), Peter Thiel (NSA/Palantir), Gilman Louie (C.I.A.), Joe Lonsdale (Palantir), Matt Choler (Instagram), Battelle Memorial Institute/John Kasich/IBM/Ohio State University (M.O.O.C.), National Venture Capital Association (NVCA), In-Q-Tel (C.I.A.), IBM, and The Eclipse Foundation.
3. Deep State Controls over Mass Surveillance: How the Deep State implemented their controls using Facebook, Google and others.
4. Reveal stolen software used by the Deep State: It will reveal that The IBM Eclipse Foundation software code base was stolen from Columbus innovator Leader Technologies and others, including Dr. Lakshmi Arunachalam, former director of network architecture for Sun Microsystems.
5. How the Binney NSA system was dismantled: Evidence of the conversion of the NSA systems away from the LEGAL designs of NSA whistleblower William Binney and toward the ILLEGAL designs of the rogue C.I.A. / IBM Eclipse Foundation and social networking.
6. Mainstream Media Collusion: The collusion of the mainstream media and Hollywood in promoting the fabricated story of Facebook’s supposed origins at Harvard.
7. Law Firm Collusion: The collusion of the law firms who perpetuate this criminality.
Prediction:
A full forensic evaluation of Zuckerberg’s 28 stonewalled Facebook hard drives and Harvard emails will likely blow the lid off of the Deep State shadow government’s hijack of the digital world. It will also reveal the nature of their uncontrolled spying and their collusion with Russian actors, including those before Vladimir Putin took power.
It will help prove that the current “The Russians Did It” accusation is yet another Alinsky-esque tactic against one’s opponent, to take the focus off the fact that one is doing exactly that oneself.
Congress needs to stop sitting on this destruction of our Republic and get these scoundrels locked up.
* * *
Investigation timeline, resources & bibliography:
- Americans for Innovation Archive.
- TIMELINE & Investigation Bibliography: People you trusted are now hijacking the Internet.
- Briefing for Representative Jim Jordan (OH 4th) – House Oversight Committee - American and Russian Opportunists Undermining U.S. Sovereignty and Corrupting U.S. Financial and Judicial Systems, Oct. 19, 2012.
- Request for Congressional Intervention from Concerned Citizens on Behalf of Shareholders of Leader Technologies, Inc., to 113th Congress, 1st Session, Feb. 21, 2014.
Notice: This post may contain opinion. As with all opinion, it should not be relied upon without independent verification. Think for yourself. Photos used are for educational purposes only and were obtained from public sources. No claims whatsoever are made to any photo. Fair Use is relied upon.
Comment
Click "N comments:" on the line just below this instruction to view comment on this post. On about Dec. 05, 2016, Google began blocking comments to this blog. However, if you email your comment to a secure email website we have established at:: afi@leader.com we'll post it for you. We welcome and encourage anonymous comments, especially from whisteblowers.

 e.g. "IBM Eclipse Foundation" or "racketeering"
e.g. "IBM Eclipse Foundation" or "racketeering"