The coin of the realm in the Clinton-Bush-Obama shadow government has been bribery, blackmail, money laundering, pay-to-play, insider tips, influence peddling, staged crises (false flags), threats and murder

Notice: Every assertion in this post is supported by facts which we will be linking over the next few days. Please return to see the updated version that will contain a mountain of evidence. Alternatively, use the AFI search tool to find the evidence yourself. See also the TIMELINE: People you trusted are now hijacking the Internet for a full bibliography of support evidence. Note: We have downloaded all the source documents cited herein and will post the PDFs and soon as they are ready. In the meantime, let's see whether the actual source document disappear suddenly.
Trump advisor and NYT best-selling author Roger Stone survives assassination attempt
Roger Stone's doctors confirm that he was likely poisoned in December 2016 by radioactive polonium while writing his new book The Making of the President 2016: How Donald Trump Orchestrated a Revolution to be released in Jan. 2016. Polonium is a byproduct from a nuclear reactor, and as such, can only be produced by countries with nuclear capabilities. It is highly toxic to life. Ostensibly, the Russians used polonium to assassinate their former Russian FSB agent Alexander Litvinenko. However, new information points to British MI6 agent Christopher Steele as the most likely hit man. Steele was recently identified as the author of the smear "dossier" that the Democrats have been trying to pin on Donald Trump. Did Steele poison Roger Stone also?
Roger Stone responded on his way in to the Donald Trump inauguration ceremony a few minutes ago: "Pure, unadulterated crap." Stone said he welcomed Congressional scrutiny of his assertion that he has no contact with Russians. He accused the C.I.A. Deep State shadow government of fabricating these falsehoods that Dr. Ulfkotte says the C.I.A. does routinely.
Stone believes the attack on him was meant to shut him up before he could debunk the lie that the Russians hacked the U.S. election.
Where are the MSM reports on this attempt to assassinate a Donald Trump advisor? Their silence tells us all we need to know.
C.I.A. Whistleblower found dead: "We all lie for the C.I.A. ...I'm fed up with this propaganda"

May God bless you
Dr. Ulfkotte. We must all tell your story now so that your death will have not been in vain.
George Soros-funded globalist surrogate Media Matters (founded by Clinton advisor David Brock) trumpets a The New York Times article yesterday accusing Trump advisor Roger Stone of being a Russian agent. (Remember, The New York Times is now owned by Mexican globalist Carlos Slim—the largest donor to The Clinton Foundation. Remember also, Soros' hedge funds make money from wars and rumors of wars as currency values go up and down in response—which feed more propaganda in a never ending stream of conflicts and money-making by globalists.) Curiously, this occurred at the same time that C.I.A. media whistleblower Dr. Udo Ulfkotte was found dead at age 56. See Ulfkotte video.
ORIGINAL POST
(Jan. 17, 2017)—John Grisham’s fiction warned us about a Deep State takeover. Former C.I.A. operative and patriot, Steve Pieczenik, was a Grisham advisor. He is currently helping to prevent a takeover of America by the Deep State shadow government that does not control Donald Trump.
The current C.I.A. attempts to smear President-elect Donald Trump, just days before his inauguration, have exposed their undemocratic treachery. For example, on Jan. 7, 2017 Senator Chuck Schumer issued a not-so-veiled threat to Donald Trump not to mess with the C.I.A. because they had "six ways from Sunday of getting back at you." Is Senator Schumer inadvertently admitting that the C.I.A. is a rogue agency?
Senator Chuck Schumer Threatens Donald Trump with retribution — saying [rogue] C.I.A. uses powers for revenge proves The Agency is out of control
Shockingly, the current attempts by the C.I.A. rogue-backed globalists are not part of a Grisham spy novel, they are real and actually happening. Fortunately, as the Deep State actors step from the shadows to protect their turf from Donald Trump, they themselves are providing the missing pieces in this puzzle of treachery and treason.
Mena, Ak; London, UK; Moscow
The C.I.A. treachery of the shadow government can trace its contemporary roots back to Mena, Arkansas and London, England.
On Sep. 17, 1992, George Soros crashed the UK Pound and pocketed $1.4 billion overnight. Two weeks later, Bill Clinton was elected the 42nd President of the United States and immediately appointed Harvard wonk and World Bank chief economist Larry Summers to the U.S Treasury. Summers immediately hired Russian Yuri Milner—later Mail.ru, DST, VKontakte (Russian Gmail and Facebook), and Sheryl K. Sandberg—later Gmail and Facebook. The recommendations pressed by this trio destroyed the emerging Russian economy. They pressed unworkable World Bank and IMF privatization policies that ushered in the current oligarch banking corruption upon which these criminals built their fortunes . . . with the help of George Soros. Their scheme to takeover global digital Email and social networks is evident in hindsight.
Soros would go on to repeat this money market manipulation across the world for decades. These funds were used to finance Bill & Hillary Clinton, The Clinton Foundation, The Clinton Global Initiative, Barack Obama, his takeover of the U.S. Democratic Party and his Open Society Foundations globalist "new world order" political agenda.[437] See also George Soros: The epic global meddler.
Bill Clinton served two terms as governor of Arkansas (1979–1981, 1983–1992). During their time in the state house, Bill and Hillary Clinton perfected their corruption skills which they brought to Washington, D.C. when Bill became president in 1993. They learned how to smuggle, sell and launder $100 million a month in cocaine through a small airport in Mena, Arkansas. They covered up their activities through bribery, offering government employment, coercion . . . and murder, as needed, of judges, police and the media.
Hillary is a disciple of the anarchist and Luciferian—Saul Alinsky. Alinsky loathed the Judeo-Christian natural order and morality. Hillary famously conjured up Eleanor Roosevelt and visited a Los Angeles witch’s coven regularly. Their former political fixer, Larry Nichols, exposed this conduct in his documentary The Clinton Chronicles (1994).
Washington, D.C. digital communications infrastructure
Bill Clinton was inaugurated to his first term on Jan. 20, 1993.
Within months he teamed up with three equally ambitious individuals, John Podesta, Larry Summers and law professor James P. Chandler, III.
On Jun. 07, 1993, (the digital sellout of America began this day—all the while, Bill and Hillary Clinton's former bodyguards and campaign staff were dying left and right, God Rest Their Souls) just five months after Clinton's inauguration, these men used White House influence to convene a meeting of leaders in technology, law, commerce and education with the singular focus to create a rationale for giving the FBI an encryption backdoor key. The C.I.A. was not mentioned, but lurked in the shadows as the real beneficiary.
C.I.A. forbidden from operating inside the USA
However, the C.I.A. and NSA are forbidden by law from spying on American citizens inside the United States. That said, Presidents Clinton, Bush and Obama executive orders have chipped away at dubious exceptions that empower the President to sneak around the law, ostensibly for our "security."
To get the backdoor key approved, Podesta schmoozed politicians, Summers bankers and Chandler lawmakers and judges.
Dubious executive orders
The Clinton White House took control of the nation’s intelligence infrastructure through a string of dubious executive orders. Chandler created the legal framework to pave the way for this takeover. He even rewrote the Economic Espionage Act and got the Congress to approve lying to Congress and courts. That’s right. it is legal to lie to Congress without legal penalty—False Statements Accountability Act of 1996, subsection (b). Summers worked on the repeal of Glass-Steagall. Among other things, this enabled him to launder the $10’s of billions he was accumulating from his offshore Russian oligarch accounts.
Congress was totally unaware of this Deep State agenda
On Sep. 29, 1999 a lynchpin for this takeover plan was the formation of In-Q-Tel by the C.I.A.
On the surface it sounded all sweetness and light. It would “unleash” the creativity of the private sector for the benefit of the C.I.A.―who was ostensibly protecting the homeland from global threats. Who could argue with that? Right?
Wrong. The C.I.A. lies and deceives for a living. American justice can barely survive such wanton conduct. Placed in the hands of unscrupulous actors, such talents will pull down any country ostensibly ruled by law and not men.
No one appears to oppose this illegal C.I.A. takeover of Silicon Valley hardware and software companies. Intelligence activities inside the United States are (should be) the exclusive domain of the FBI. One wonders how they have gotten away with it.
The current officers and trustees of In-Q-Tel prove without question that America’s digital infrastructure was hijacked under Bill Clinton and that George Bush and Barack Obama also approved this immorality.
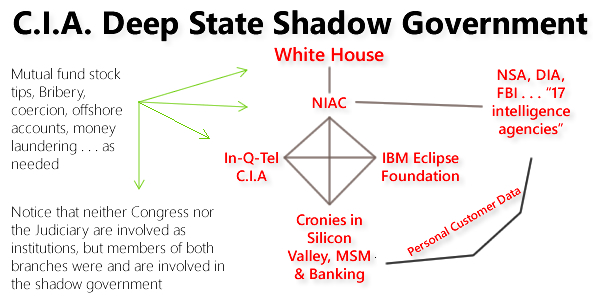
Three organizations run the illegal Deep State shadow government:
- In-Q-Tel run by the C.I.A. to pump billions of dollars in public funds to buy private companies in Silicon Valley. Once formed, the C.I.A. uses Wall Street to launder funds globally and create trillions of dollars in value to perpetuate this evil bubble. See also AFI Timeline, search "in-q-tel"
- NIAC (National Infrastructure Assurance/Advisory Council) created by a string of dubious executive orders. See also AFI Timeline, search "niac"
- The IBM Eclipse Foundation created by the Deep State to provide the common social technology infrastructure around the planet using Leader Technologies’ social networking invention as its foundation. See also AFI Timeline, search "eclipse"
The Deep State discovered that they had no Internet-scale platform when they wanted to get rolling in the late 1990’s
As with every evil scheme, the Deep State plan had an Achilles’ Heel.
The technology infrastructure plan in the late 1990’s was to rely on IBM, Microsoft and AT&T for the technology.
However, they had a collective problem. They had been so busy selling their legacy “client-server” systems (PC’s linked together in networks) during the 1990’s that they had grown lax in research and development for the emerging Internet.
Microsoft’s Bill Gates admitted that he was late to the Internet game, as were IBM and AT&T.
During the mid-1990’s, a Columbus, Ohio inventor-entrepreneur named Michael McKibben had saved AT&T from great embarrassment. AT&T Bell Labs discovered that they were not prepared with new email software for the much ballyhooed introduction of Microsoft’s Windows 95.
McKibben’s team came to the rescue and built for $1 million in six months what Bell Labs had estimated would cost $6 million and three years. During that time McKibben and his team supported AT&T’s global infrastructure. McKibben’s company and Disney were two of the first ten commercial websites set up by AT&T WorldNet.
Engineer McKibben saw a gaping hole in IBM, AT&T and Microsoft capabilities to support large-scale Internet collaboration. They could not scale to the volumes of transactions that Internet users would expect.
Social networking was invented by the real developers in Columbus, Ohio—Leader Technologies
Facebook Hacks
So, rather than tell anyone what he saw, McKibben quietly formed Leader Technologies in 1997, raised his own funds, hired world-class talent, and ran the research and development himself. He invented what we now know as “social networking” over the next three years. By the early 2000’s he had invested $10 million and created 650,000 lines of programming source code. At 66 lines per page, that’s a 10,000-page book. By contrast, Mark Zuckerberg’s lie is that he invented Facebook in “one to two weeks” while drinking, chasing girls and studying for midterms.
Zuckerberg has yet to produce any evidence of his fake story as perpetuated in The Social Network. That's right, Zuckerberg was and is merely a C.I.A. hack.
Knowing that their invention was too early for an Internet market with less than 10 million users, McKibben sought to protect these innovations with copyrights and patents. He sought the best patent advice he could find in Washington, D.C. See Leader v. Facebook trial transcripts.
The Deep State schemed to steal social networking
Through various people, McKibben was introduced to law professor James P. Chandler, III. Chandler saw instantly that McKibben had solved the technology problems his Deep State shadow government was having with IBM and Microsoft Internet platform software.
Rather than file the patents immediately, which experts say would have been normal advice, Chandler advised Leader to “reduce the invention to practice” before he would file the patents. Since Chandler was advising the Clinton White House, Congress and the Courts on such matters, Leader assumed his advice was sound.
Hindsight shows that Chandler’s advice was a self-serving effort to steal the invention for the Deep State.
Ironically, Chandler, Clinton, Summers and Podesta had formed In-Q-Tel on Sep. 29, 1999. Leader Technologies was first introduced to Chandler just a few months later in Jan. 2000.
Attorney-client privilege confidentiality is a Deep State fiction to fool unsuspecting inventors
Chandler agreed immediately to become Leader’s patent attorney and even to become a member of Leader’s board of directors. Leader was flattered by Chandler’s interest and naturally assumed that attorney-client confidentiality would be honored.
Chandler’s organizing role in the C.I.A. Deep State shadow government has taken many years to uncover. It is pretty well hidden.
However, various whistleblowers and FOIA disclosures to groups including Judicial Watch and Citizens United have now exposed Chandler’s central role. Leader’s personnel say that Chandler never disclosed his conflicts of interest with the Clinton White House, IBM, Microsoft, C.I.A., the NSA and the shadow government.
Deep State legal justification: National Infrastructure Assurance Council (NIAC)
On Jan. 18, 2001, Bill Clinton appointed Bill Gates and James P. Chandler to the National Infrastructure Assurance Council (NIAC) which he had formed and empowered by a succession of executive orders. George Bush renamed it the National Infrastructure Advisory Council (also, NIAC) and layered on more executive orders.
Deep State technology distributor: The IBM Eclipse Foundation

Fig. 4—The IBM selection of this imagery for The IBM Eclipse Foundation appears to be appropriate since the symbol of Islam is an eclipse of the moon.
Six weeks after 9/11, on Nov. 29, 2001, IBM and Chandler formed The IBM Eclipse Foundation with a $40 million IBM “donation” to promote “open source.” Pundits know that IBM and “open source” are oil and water since IBM is the largest holder of patents on the planet.
Hindsight shows that the term “Eclipse” may have been well-chosen imagery for the coming radical Islamic jihadi onslaught promoted by Obama’s Deep State as he has apparently attempted to destroy Western economies in favor of China and the New World Order globalists.
On Aug. 29, 2002, all of Leader Technologies technical innovations appeared overnight in the IBM Eclipse Foundation distribution of source programming code to a suddenly rich assortment of “members” including SAP, Microsoft, HP, Oracle and IBM. IBM claimed copyrights on it all.
A series of laughable narratives by various Eclipse parties tried to cover over this theft of Leader Technologies innovations with nonsensical cover stories.
The C.I.A. created much of modern day Silicon Valley illegally—social media is a fraud because its foundation was stolen, and the C.I.A. funded its expansion as an illegal spy tool
Now we roll this story forward to today to prove that the C.I.A. CREATED the “social” Silicon Valley as the excuse to steal all data from all users, globally, not just in the USA.
Three Silicon Valley venture capital companies figure prominently in C.I.A. In-Q-Tel:
- Kleiner Perkins, Ted Schlein:
 James W. Breyer
James W. Breyer
C.I.A. In-Q-Tel NVCA chairman; Facebook chairman; Accel Partners; IDG-Accel Capital (China)
Google, Facebook, Twitter, Amazon, AOL, Verisign, Zynga, Cisco, Genentech, Netscape, WebMD, Intuit, Coursera, Groupon
- Greylock, Howard E. Cox
Facebook, Instagram, LinkedIn, Cloudera, Dropbox, Groupon, Pandora, Airbnb, Digg, Zend, Constant Contact, Workday
- Accel Partners, James W. Breyer
Facebook, BitTorrent, Cloudera, ComScore, DropBox, Etsy, Groupon, Raytheon BBN

These facts prove that Silicon Valley is essentially nationalized. Readers should remember recent history: Nazi Germany permitted private industry to flourish as long as the companies like Krupp, VW, BMW, IBM, Mercedes, Siemens, Ford and Opel supported the Nazi political agenda. The involvement of these 'private' companies in this secret White House intelligence operation parallels Nazi Germany's corporate corruption.
Kleiner and Greylock are current trustees of In-Q-Tel.
Accel Partners and its founder James W. Breyer facilitated the rise of In-Q-Tel while Breyer was Chairman of the National Venture Capital Association (NVCA, 2004) where In-Q-Tel’s founding CEO Gilman Louie was also a director (1999-2006), as was as In-Q-Tel trustee Theodore "Ted" E. Schlein, CEO of Kleiner Perkins.
Other current C.I.A. In-Q-Tel trustees and officers include:
| C.I.A. In-Q-Tel Management/Agents Download all these CIA In-Q-Tel biographies, accessed Jan. 17, 2017 |
||||
| Lastname | Firstname | Fullname | In-Q-Tel position | Organization / C.I.A. Operative |
| Crow | Michael M. | Michael M. Crow | Chairman | Arizona State University |
| Adams | Bruce | Bruce Adams | General Counsel | Arnold & Porter LLP |
| Barksdale | James L. | James L. Barksdale | Trustee | Netscape |
| Barris | Peter | Peter Barris | Trustee | New Enterprise Associates (NEA) |
| Bowsher | Steve | Steve Bowsher | Managing Gen. Partner | InterWest, E-Trade, Stanford |
| Cox | Howard | Howard Cox | Trustee | Greylock |
| Darby | Chris | Chris Darby | Trustee | Intel, Symantec, HP, Northern Telecom |
| Gleichauf | Bob | Bob Gleichauf | Director, Lab41 | Cisco |
| Jones | Anita | Anita Jones | Trustee | University of Virginia |
| Krongrad | A.B. “Buzzy” | A.B. “Buzzy” Krongrad | Trustee | DLA Piper LLP, C.I.A. |
| Misick | Jami | Jami Misick | Trustee | Kissinger Associates |
| O’Toole | Tara | Tara O’Toole | Director, B. Next | DHS, DOE |
| Louie | Gilman | Gilman Louie | CEO emeritus | "Once C.I.A., always C.I.A." |
| Mullen | Mike | Mike Mullen | Trustee | Bush/Obama military advisor, Joint Chiefs of Staff chairman |
| Paté-Cornell | M. Elisabeth | M. Elisabeth Paté-Cornell | Trustee | Bush Foreign Intelligence Advisory Board |
| Porter | Lisa | Lisa Porter | Director, Cosmiq Works | IARPA, NASA |
| Poulos | Lisabeth | Lisabeth Poulos | Chief of Staff | BAE, Microstrategy |
| Radosevich | Will | Will Radosevich | EVP, Technology Programs | Mobile System 7 |
| Schlein | Ted | Ted Schlein | Trustee | Kleiner Perkins, National Venture Capital Association (NVCA) |
| Shea | Teresa | Teresa Shea | Director, Cyber Reboot | NSA |
| Strottman | Matthew | Matthew Strottman | COO | Friedman Billings, PWC, Notre Dame, Georgetown |
| Tenet | George J. | George J. Tenet | Trustee | C.I.A. Director, Allen & Co |
| Vickers | Mike | Mike Vickers | EVP | DoD |
| Table 1—C.I.A. managers/agents of In-Q-Tel. | ||||
The illegal collusion of the Deep State military-industrial complex is grossly evident just in the list of In-Q-Tel trustees. When we add the list of members in the NIAC and IBM Eclipse Foundation, the evident corruption of the shadow government is glaring. Again, one wonders why no one in government, intelligence, commerce or the military blew the whistle on this massive collusion.
It appears that when the rogue public-private C.I.A. operatives came out of the woodwork to smear Donald Trump with all the talk of fake news and supposed Russian dossiers, they over-played their hand, thankfully.
2,387 technology financings by C.I.A. officers
These three “vulture” capitalists have together funded 2,387 financings of largely Silicon Valley companies that are heavily committed to the C.I.A. “The Internet of Things” social technologies. Accel Partners, Greylock, Kleiner Perkins.
Click here for an Excel | PDF full downloads of the CrunchBase financing summaries for Accel Partners, Greylock and Kleiner Perkins.

Breyer has shifted his venture capital investing priority outside the the U.S. to China where his reclusive father, John P. Breyer (the web has been essentially cleansed of Breyer Sr.'s biographical information who was the founder of ComputerWorld (!), but AFI investigators found some information linked here), moved to set up IDG-Accel and IDG Capital Partners. John P. Breyer, Andy Grove (Intel) and George Soros are fellow Hungarian refugees.
Some of the Chinese officers of Breyer's IDG Technology Venture Investment III LLP and Wininchina, Inc. were identified by HSBC Swiss whistleblower Hervé Falciani as being involved with off-shore money laundering of dictators, drug and arms dealers. The HSBC money launders fingered by Falciani include all of the Facebook IPO underwriters and several Facebook law firms.
Breyer is also pressing Barack Obama to push through the Trans-Pacific Partnership (TPP) which includes liberal intellectual property provision allowing infringing countries to rewrite their rules at any time to favor a local infringer like Facebook and other Breyer companies.
C.I.A. operatives like Breyer are “super-bullish” on China
Many technology operatives are now meeting in Davos, Switzerland at the World Economic Forum. They are openly complaining about Donald Trump’s populist victory in America, and Brexit in the UK. Tellingly, one of the keynote speakers was Chinese President Xi Jinping.
China is promoting Internet censorship of populist movements worldwide
The Chinese president is openly calling for censorship of the American populist alternative media. Davos globalist disciples are now looking to Communist China to save their 100-year One World Government agenda (e.g., Rothchilds, Bilderberg, Rockefellers, J.P. Morgan) to establish corporate control of world government--a movement that is now being resisted worldwide.
The American Republic is teetering
No wonder the American Republic is teetering.
An entire generation of technology entrepreneurs in Silicon Valley has been morally and ethically ruined by this rogue group of C.I.A. spies and their global accomplices.
These In-Q-Tel people elected themselves to dictate the rules of our business and social discourse. The American Republic is under attack.
We need to find every way to resist these globalists.
* * *
Bookmark: #cia-whistleblower-found-deadPoscript, Jan. 20, 2017 Update:
Journalist Who Blew the Whistle on C.I.A. Media Control Drops Dead at 56; says C.I.A. rogues are fomenting global wars
Dr. Ulfkotte said the mainstream media is completely fake. https://youtu.be/d9SN_-sWOYU | Raw *.mp4 video file
"We all lie for the C.I.A... I'm fed up with this propaganda"
Related Posts:
Jan. 06, 2017: The day the C.I.A. / NSA turned against our privacy rights - Trump is right.
Dec. 13, 2016: Fake social media is run by the CIA and creates fake news to demonize truth tellers and overturn Trump's election
Dec. 19, 2015: The fall of the U.S. & the rise of a New World Order
Oct. 23, 2015: Hillary testimony uncovered collusion with the spy state cartel
Sep. 11, 2015: Spy state cartel has taken over the digital world.
Aug. 11, 2015: Hillary & Bill shill for a secret intelligence agency cartel.
Aug. 03, 2015, Will Republicans debate the real core of Washington corruption — the C.I.A. Facebook spy state?
Jul. 17, 2015: Disastrous rise of a lawless C.I.A.
Jul. 09, 2015: Facebook started by C.I.A. as spy-state tool.
Jun. 23, 2015: IBM lied about NSA spy platform.
May 29, 2015: NSA bulk data scheme controlled by an IBM cartel.
Apr. 18, 2015, Shadowy IBM Eclipse Foundation lords over American media and politics
Mar. 25, 2015, Betrayal: former FBI director colluded with cartel offshore money laundering havens
Feb. 11, 2015, Obama promotes IBM criminality in latest executive order
Notice: This post may contain opinion. As with all opinion, it should not be relied upon without independent verification. Think for yourself. Photos used are for educational purposes only and were obtained from public sources. No claims whatsoever are made to any photo. Fair Use is relied upon.
Comment
Click "N comments:" on the line just below this instruction to view comment on this post. On about Dec. 05, 2016, Google began blocking comments to this blog. However, if you email your comment to a secure email website we have established at:: afi@leader.com we'll post it for you. We welcome and encourage anonymous comments, especially from whisteblowers.








































