Yes, Mueller organized 9/11, and then investigated himself!
Mueller placed his patsy Joseph E. Sullivan at Cloudflare to fix the 2018 midterm elections
Sullivan is a shill for the Senior Executive Service (SES) shadow government controlled by Mueller
Sullivan tried to cover up the loss of 57 million Uber customer and driver personal data records, was fired, then rehired by Cloudflare that controls FL, OH election encryption keys

(Nov. 16, 2018)—New facts suggest that special counsel Robert S. Mueller, III who is running the Trump witch hunt, is also muscling in on the Clinton encryption key tax and surveillance empire.
Their war cry appears to be: "Tax and Surveil!" Ask yourself, if controlling these encryption keys is so central to the mission of the Deep State shadow government and their theft of our Constitutional Republic birthright, shouldn't you be resisting them with all your strength? We posit that if you are not—if you are silent, or worse, if you scoff at those who are fighting, while mindlessly repeating the "conspiracy theory!" epithet*—then that is your first clue that you have been successfully brainwashed and neutralized by incessant mainstream media propaganda—which these miscreants control.
Bookmark: #conspiracy-theory-defined | https://tinyurl.com/y9xo7cdq
Traditional mobsters control big city garbage, prostitution, loans, drugs, haulage and so on. They either actually run the business or shake down enterprises for monthly “protection” payments.
According to Larry Nichols (Jul. 28, 1994 timeline entry), Bill Clinton’s former political advisor in Arkansas and for President, Hillary’s father Hugh Rodham and Dan Rostenkowski took over the Chicago mob after Al Capone. Later, Rosentkowski became the Democrat representative to Congress from the Illinois 5th district (1959 to 1995). In short, these men learned how to turn corruption into political power—without going to jail.
Hugh Rodham encouraged his daughter to become a patent attorney. He told her to corner the market on emerging technologies, which she has done.
Bookmark: #joseph-e-sullivan-biography | https://tinyurl.com/y7d8935e| Meet Robert Mueller's perennial SES shadow government silicon valley errand boy—Joseph E. Sullivan |
We strongly recommend that you download and store this Sullivan biography. It includes about fifty (50) links to source documents. Thank you to the AFI and AIM Conclave miners! |
| Click image to view this document. |
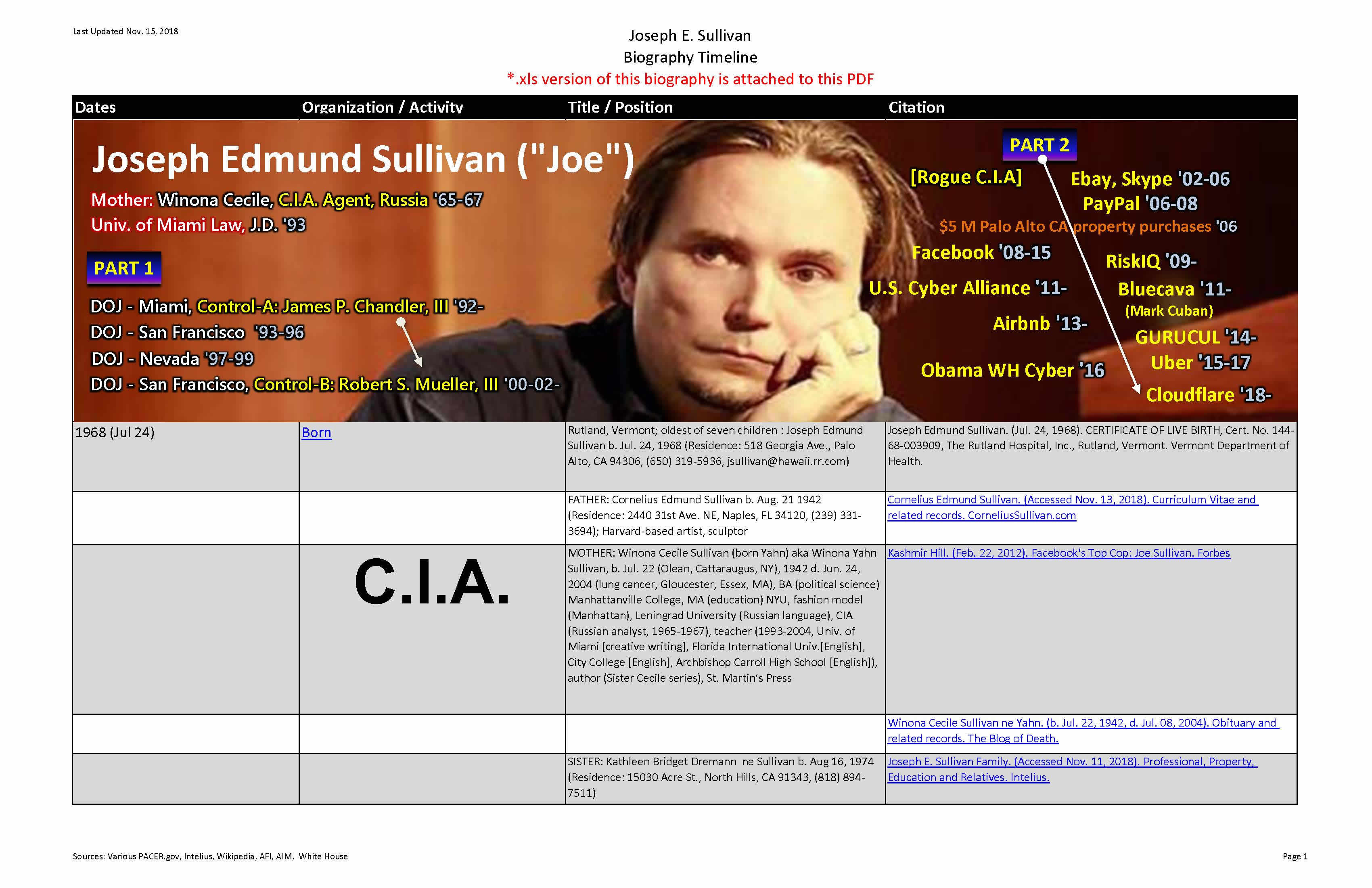 |
| Fig. 3—Joseph Edwin Sullivan. (Prepared Nov. 09, 2018). Biography and Timeline. Anonymous Patriots. |
In Feb. 1977, Hillary joined the Rose Law Firm in Little Rock, Arkansas, and eventually seized control of a client's promising invention, a quarter-sized quartz device called the QRS-11 that could be used to track planes, cars, trucks, trains, buses, and more generally anything in which it was embedded.

Hillary’s legal mentor was a clever black Harvard and George Washington University law professor named James P. Chandler, III. While he coached Bill and Hillary, Chandler was scheming to corner the legal market on protection of software inventions, trade secrets and "the intellectual property of the United States." So he boasted at every opportunity.
When the Clintons came to power in 1993, Chandler became their top outside advisor for intellectual property, patents, trademarks, copyrights, trade secrets, economic espionage, counterfeiting and counter intelligence. He immediately wrote and Congress approved (unanimously), The Economic Espionage and Federal Trade Secrets Acts of 1996, and The False Statements Accountability Act of 1996 (officially sanctioned lying to Congress and the courts. That's right, you did not misread).
One of Chandler’s strategies was to use his influence over the Clintons to take over the Internet as a way to stay perpetually ahead of Russian, Chinese, Japanese, Israeli, Irish, Indian and French intelligence. So he also boasted.
At the same time, Chandler was outside counsel to IBM. He worked closely with IBM inside intellectual property counsel, David J. Kappos (Obama's Patent Office director - 2009-2013), to muscle IBM's competitors with "junk patents" to extort license fees. This activity was the real "patent troll" which Chandler and Kappos have flipped 180 degrees into unfounded media attacks on small inventors as the trolls.
The weaponization of social networking
IBM was all the while standing behind Chandler's plan to weaponize the Internet. See our previous post: The Weaponization of Social Media Should Concern Us All (PDF).
Within months of Clinton coming to power, Chandler arranged for the Carnegie Endowment for Peace, Clinton chief of staff John Podesta, and a raft of DOJ insiders, including Robert Mueller, James Comey, Duval Patrick and Louis Freeh to hold a Who’s Who conference to promote giving the FBI backdoor encryption access to the emerging commercial Internet, which was in its infancy then. The proposed “Clipper Chip” died in Congress over privacy concerns and inadequate safeguards.

James P. Chandler, III, John D. Podesta. (Jun. 07, 1993). Third CPSR Cryptography and Privacy Conference, included Stephen D. Crocker, John D. Podesta, James P. Chandler, III, Ann Harkins, Ken Mendelson (Stroz Friedberg), Juan Osuna, Cathy Russell, Steven Wolff, IBM, HP, AT&T. FOIA No. 9403963. U.S. Dept. of State. Note: This PDF file contains a spreadsheet of the attendees (click on the paper clip inside the PDF).
Said another way to hopefully clear up the confusion, the Clipper Chip and the QRS-11 chip are different devices. The Clipper Chip was a device proposed in the early Clinton Administration (1993) to be embedded in hardware to encrypt digital signals, but was never approved by Congress or implemented—rogue intelligence did an end-around Congress with the Dual_EC_DRBG algorithm discussed in the next paragraph. By contrast, the QRS-11 was and is a navigation device installed widely in ships, vehicles and airplanes to transmit 3-D coordinates and receive instructions to control autopilots remotely.
Undeterred, Chandler and his FBI/DOJ/DoD/Senior Executive Service (SES) co-conspirators turned to the Departments of Commerce and Justice to concoct an export license requirement to embed the backdoor key as a prerequisite for sale of their hardware, software and firmware offshore. The list of vendors who embed the NSA Dual_EC_DRBG encryption algorithm to this day is even published.
American-style fascism was perfected under Clinton rule
The Clinton-Chandler-Podesta-Mueller scheme to bypass Congress on encryption backdoors as well as all other technology and Internet policy was hatched.
The Clintons began focusing on: (1) Chandler-drafted executive orders, (2) some changes to laws triggered by totally staged “terror” threats, (3) patsy Senior Executive Service (SES) appointments in the Executive agencies (their 10,000+ leave-behind senior management saboteurs a.k.a. the "shadow government" or "Deep State." and (4) cooperation from the private sector as "public-private partners" in exchange for no-bid contracts. In short, American-style fascism.
High Tech Mobsterism
In keeping with the age-old maxim of “follow the money,“ the real money being made in "Big Data" is through secret taxes on the encryption keys and the sale of information.
Prior to social networking however, these Clinton mobsters experimented with various forms of control and revenue, but their systems suffered from data “silos.” Large volumes of data were system specific and not easily transportable across systems. Any ability to tax these transactions was fraught with too many technology and policy hurdles to implement it globally.
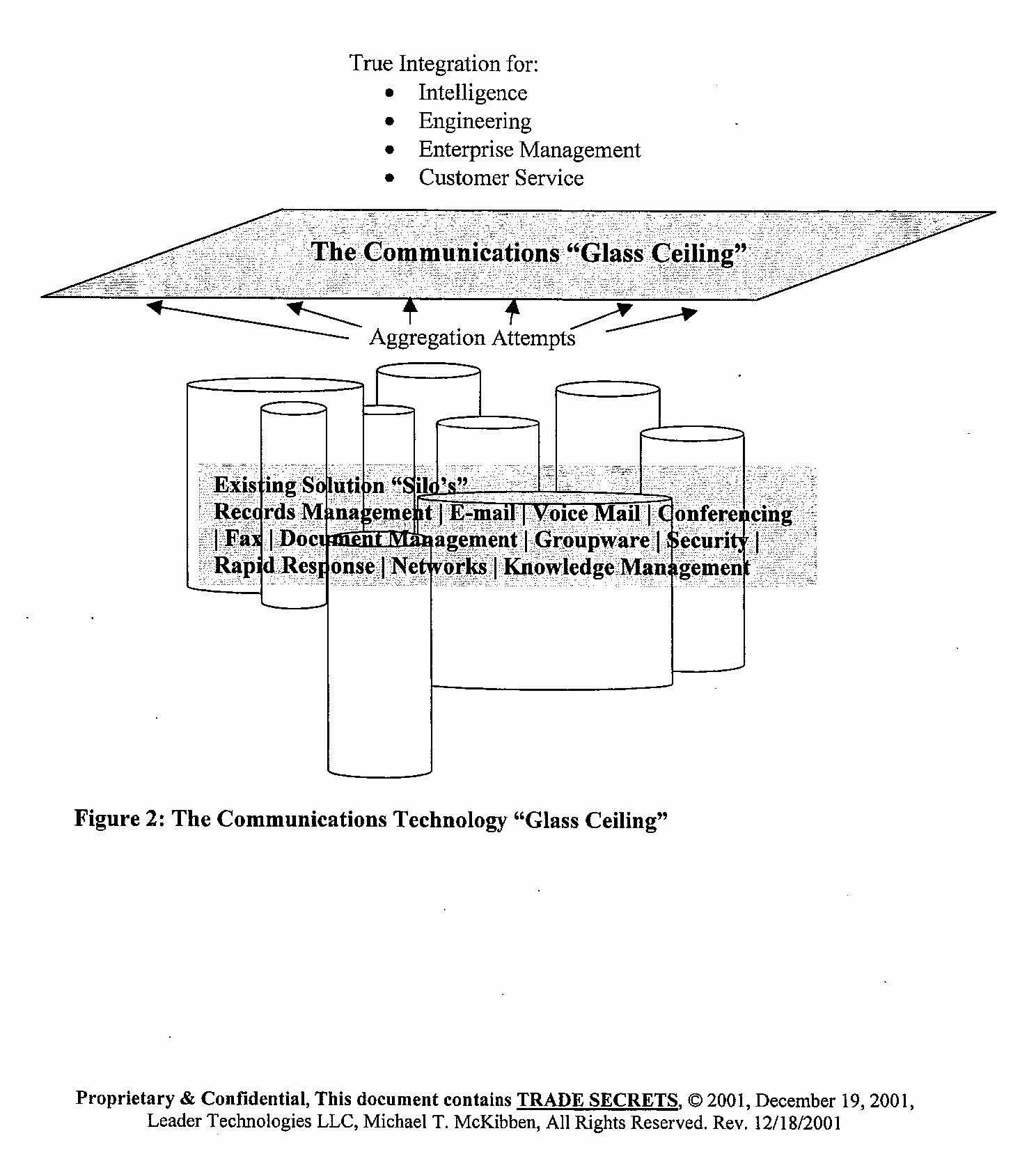
Michael T. McKibben. (Dec. 18, 2001). BAA Command and Control Proposal. WPAFB/Leader Technologies.
These mobsters yearned for a way to collect a private, non-governmental tax on each Internet transaction. They also wanted a universal way to spy on people at will.
The answer to their evil prayers came one day in January 2000 when James P. Chandler, III was introduced to Columbus entrepreneur, engineer and inventor Michael T. McKibben. McKibben and his team, in total secrecy, had invented a way to overcome the silo problem and make the Internet scalable.
McKibben knew what he was doing engineering-wise and organizationally. He was an accomplished organizational development consultant and a leadership and management author. In the early 1990’s he had rebuilt AT&T’s main email system AT&T AccessPlus 3.0 in time for release with Windows 95 as well as designed a number of personal information managers.
Social networking scalablilty opened the door to one encryption key per person, thus the ability to track and tax everything
Hindsight being 20-20, we now see that Chandler, Clinton, Mueller, etc. decided to steal McKibben’s invention (illegal) for infinite Internet scalability, inserted IBM copyrights (illegal), declared it "open source" (illegal), then distributed it free almost overnight to Silicon Valley (illegal) to build the “IBM Internet of Things (IoT),” and thus control universal back end access (illegal) to all the code they had given away. That's right, the entire IoT industry is one mammoth fraud, built on theft, lies, and more lies.
With McKibben’s social networking invention in mind, they also reconfigured their approach to “Public Key Infrastructure” (PKI), government documents (p. 6) describe (ref. "late 90's" [when Chandler met McKibben and Leader Technologies] and "Prior to 2004" [when IBM launched EclipseCon 2004, Feb. 02-05, 2004, and they launched Facebook, Feb. 04, 2002]).
They also devised a convoluted licensing system that only an unscrupulous lawyer could love whereby “trusted” private companies would maintain not only the public keys used by websites, but also a copy of people’s private keys, ostensibly for disaster recovery convenience. See Fig. 8.
Trust (not)
These selected PKI Certificate Authorities plaster their cheeky ad words on all their PR. These words include: trust, high standards, security, integrity, verified, trustworthy, assurance, certified, protect, reliable, secure, quality and veritas (Latin: truth). They have proven through focus groups that 99.5% of the public believes their excrement about "trust" and lets them get away with their criminality.
Moral: Whenever “public-private” fascist capitalists use words like "trust, you can almost be sure that you cannot trust because this is classic Saul Alinsky misdirection.
Several types of encryption keys that use PKI
In lay terms, the basic idea behind PKI is that you need to marry up a public key for your recipient’s website with your private key. Those married keys are then used to encrypt your transmission. It's like you need two keys, not one, to open your front door.
Then, instead of sending your message through the Internet for anyone to read, your transmission is scrambled while it is on the move. See Fig. 3 below. This type of encryption occurs automatically, presuming each side has purchased their essentially government-mandated Certificate Authority (Hint: Herein is the universal tax on all Internet transactions—run by private corporations controlled by Hillary et al. Want in on this action? No! Deplorables need not apply.)
This purchase is Hillary’s dirty little secret for how she taxes the Internet and makes money from each and every transaction all around the planet.
Bookmark: #encryption-flow-chart | https://tinyurl.com/y78qyumt| Click image to enlarge this graphic. |
 |
| Fig. 6—Illustration of unencrypted (plain text) and encrypted data |
Another use of public and private keys is encrypting files and messages. Both sender and recipient share their public key and each creates a private key. The public key is generally kept on a PKI server. The secret here is that these servers also use various ways to sniff and store your private key without your knowledge. In addition, many if not most of the applications that encrypt and decrypt using this method contain the NSA Dual_EC_DRBG algorithm that enables snoopers to decrypt anything without any keys, public or private.
Mueller is muscling Hillary for encryption key turf
Over the last thirty years, the encryption key turf was controlled by Hillary and her mentor Chandler. They let the DOJ and FBI play through corruptocrats like Robert S. Mueller, III and James B. Comey, among others.
However, it now appears that Mueller and Chandler quietly recruited Joseph Edmund Sullivan, son of a C.I.A. agent, as the mole to do their dirty work.
Sullivan’s mother, Winona Cecile Sullivan (born Winona Yahn), was a C.I.A. agent focused on Russian spying (1965-67). She studied Russian at the University of Leningrad, then applied to the C.I.A. to be a spy. Her good looks may have helped her professionally. The trade craft of deception was well-honed among the Sullivans. Joseph claims he had no knowledge of his mother’s spying, but given his career as a spy himself, this assertion is not credible. And, as we now see, these SES spies like to pass on their insider knowledge to their offspring.
From 1992 to 2002, Sullivan worked for the DOJ and specifically for Chandler and Mueller as Assistant U.S. Attorney (AUSA) in Miami, Las Vegas and San Francisco. He only prosecuted 41 cases in total during his work as AUSA. He bragged at his House Judiciary hearing on Jul. 28, 2010 that he was a founding member of the DOJ Computer Hacking and Intellectual Property Unit (see link above), despite scant few cases on that subject. Ironically, that was the very same day that Leader proved in Leader v. Facebook that Facebook was infringing Leader Technologies' social networking patent on 11 of 11 claims. Sullivan failed to disclose this to Congress. He also failed to disclose Hillary's secret contract for Facebook to build an election winning template. He also failed to disclose his relationship with Leader's patent attorney Chandler, thus being engaged in tampering with a witness.
This Mueller Cyber Crime Unit appears to have been a ruse to cover up Mueller’s work to horn in on the Clinton’s money-making from taking fees for digital encryption Certificate Authority keys. It appears that the real cyber criminals are Mueller, Chandler and Sullivan.
Bookmark: #us-v-avalar-mueller-sullivan | https://tinyurl.com/y9gtysqeHere’s proof that Sullivan and Mueller collaborated closely.
| Click image to view this document. |
 |
| Fig. 7—US v. Avalar, et al, 5:01-cr-20069-JW-1 filed jointly between Robert S. Mueller, III, US Attorney and Joseph E. Sullivan, Assistant US Attorney (CAND filed Apr. 26, 2001). |
Here’s further proof that Mueller was Sullivan’ mentor:
| Click image to view this document. |
 |
| Fig. 8—Joseph E. Sullivan. (Jul. 28, 2010). Chief Security Officer for Facebook testimony before the U.S. House of Representatives Committee on the Judiciary, Subcommittee on Crime, Terrorism, and Homeland Security, hearing on Online Privacy, Social Networking, and Crime Victimization. U.S. House of Representatives. |
Here is proof that Chandler and Sullivan worked together. This case could only have been prosecuted with Chandler’s approval since it is notoriously known in Washington, D.C. that the U.S. Department of Justice was required to permit Chandler to oversee the prosecutions of his newly minted Federal Trade Secrets Act of 1986 19 USC 1832 for ten (10) years.
Bookmark: #us-v-wang-chandler-sullivan | https://tinyurl.com/y9gtysqe| Click image to view this document. |
 |
| Fig. 9—US v. Wang, et al, 5:01-cr-20065-JF-1, Joseph E. Sullivan, AUSA with James P. Chandler, III (CAND filed Aug. 24, 2000). |
Sullivan’s move from DOJ/FBI to Silicon Valley has been truly magical
Sullivan was then placed as the top legal and security officer and advisor at Ebay, PayPal, Skype, Facebook, RiskIQ, U.S. Cyber Alliance, Bluecava (Mark Cuban), Airbnb, GURUCUL, Obama’s Presidential Commission on Enhancing National Cybersecurity (read: get Hillary elected), Uber and now Cloudflare.
After eBay, Sullivan bought two homes in Silicon Valley in 2006 worth $5 million—a remarkable achievement for a guy who had made $130,000 per year as an assistant U.S. attorney.
Remarkably, Sullivan was hired as chief security officer at Cloudflare despite his epic loss of 57 million user and driver records at Uber and his attempt to cover it up six months earlier. That got him fired at Uber. Of course, normally that might have been a career-ending faux pas, but not for Mueller’s and Chandler’s flunky.
Cloudflare hired tainted goods—evidently because Mueller directed it
Evidently, Mueller placed his errand boy Sullivan at Cloudflare, but for what purpose?
A quick review of Cloudflare’s owners is one clue to Mueller's thinking. It is the same list of shadow government crony corporate beneficiaries like Pelion Ventures, Venrock, NEA (New Enterprise Associates), Union Square Ventures, Greenspring Associates, Fidelity Investments, Google Capital, Microsoft, Qualcomm and Baidu (China).
The specter of foreign interference in U.S. elections is evident given Baidu (China)'s substantial ownership stake in Cloudflare. Also, given Google’s now hostile activity in supporting totalitarian regimes in China and Venezuela, and their support of Project Dragonfly and the heinous “social credit score” in China, the risk to free and fair US elections is doubly evident.
When one adds the fact that Mueller's Russia probe is a witch hunt that is debilitating our government, has he exposed American election to Chinese influence using Cloudflare, has Mueller not now become an enemy of the state?
Bookmark: #us-state-election-certificate-authorities | https://tinyurl.com/y88oavrf| Click image to view this document. |
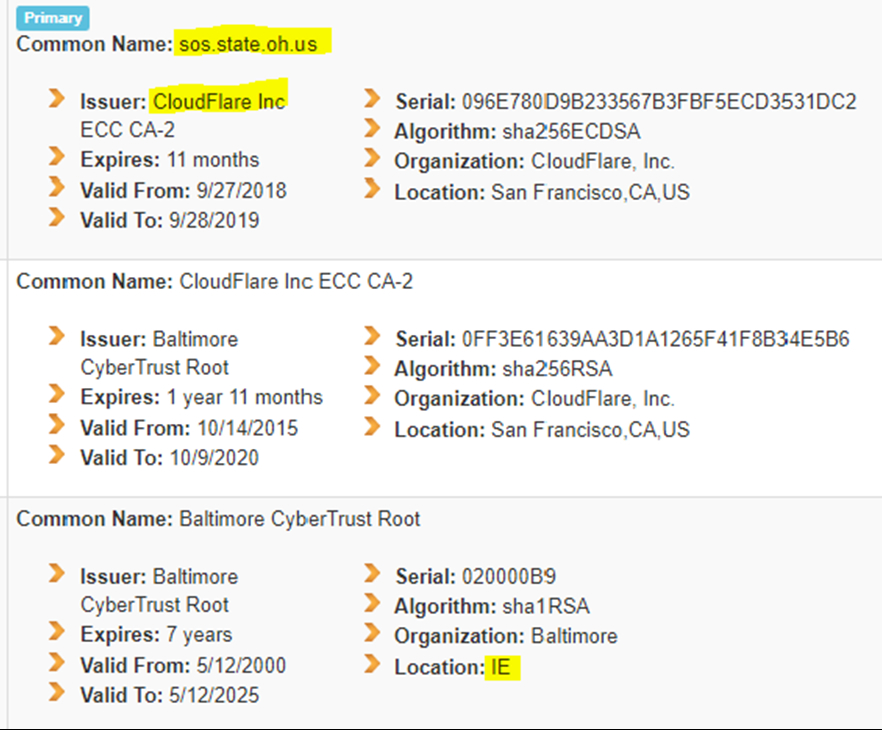 |
| Fig. 10—Anonymous Patriots. (Prepared Nov. 09, 2018). OHIO - State Election Encryption Authorities, by State, p. 71-72. MX Toolbox. |
| Click image to view this document. |
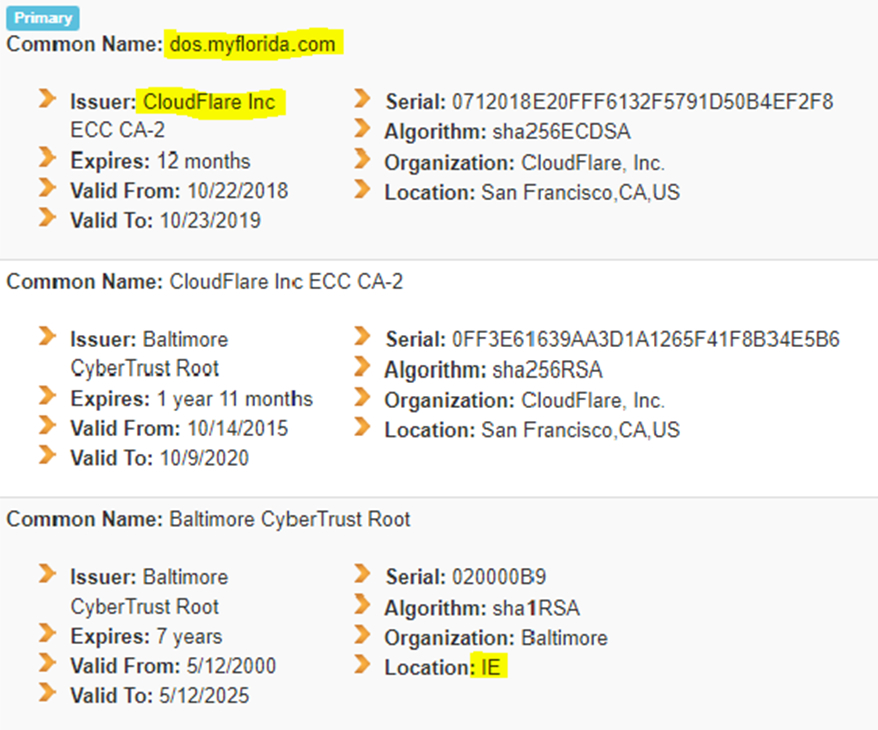 |
| Fig. 11—Anonymous Patriots. (Prepared Nov. 09, 2018). FLORIDA - State Election Encryption Authorities, by State, p. 24-25. MX Toolbox.. |
Mueller infiltrated Cloudflare via Sullivan to get access to swing state election encryption keys
Given how quickly Cloudflare and Mueller muscled in on Hillary’s Certificate Authority turf, we are observing an evident mob turf war for control of all Certificate Authority taxing and encryption keys.
When one considers that Hillary and her 19-year law partner Jerry C. Jones sold ENTRUST to placate Michael Chertoff on December 17, 2013, the specter of a full-on mob turf war seems likely. With the ENTRUST purchase, Chertoff bought Certificate Authority in at least Colorado, Oklahoma, Pennsylvania, South Dakota and Wyoming.
The difference between Chertoff and Mueller is that Chertoff appears to be a soy boy who is satisfied with his little piece of the pie.
Robert Mueller: 'Ole Mule Face Dreams he is King of the world! (He thinks Queen Hillary screwed up her encryption keys in 2016)
Mueller, on the other hand, wants to be king maker, evidently.
In the process of giving Michael Chertoff some of the encryption action, Hillary and Jerry C. Jones shifted their Certificate Authority business by purchasing DigiCert, which controls the encryption keys in the following state election systems: Connecticut, Illinois, Kentucky, Louisiana, Maine, Maryland, Massachusetts, Michigan, Nevada, North Carolina, Ohio (Cloudflare-DigitCert), Oregon, South Carolina, Tennessee, Vermont, Virginia, Washington, West Virginia, Wisconsin
By grabbing encryption keys in Ohio and Florida, Mueller is challenging Hillary’s turf.
Are Mueller’s Wheels Falling off? We hope so.
As an illegitimate special counsel, Mueller is attempting to unseat a duly elected President Donald J. Trump.
Mueller has overstepped his special counsel authority by conducting a political witch hunt against his effective enemies including Paul Manafort, Roger Stone, Julian Assange, among others.
Mueller and Chertoff evidently organized the events of 9/11 to remove the Constitutional blocks to their SES shadow government takeover of our Constitutional Republic.
Mueller has persecuted dozens of FBI and CIA whistle blowers.
It is strongly believed that Mueller had his former FBI agent Whitey Bulger assassinated recently just before he was preparing to testify about Mueller.
Mueller clearly wants a piece of the Certificate Authority taxing and mass surveillance encryption system that the Clintons currently control.
Maybe he wants more.
Maybe he wants to be the King Mob Boss.
The Clintons are now in his way.
Call to Action:
President Trump can immediately direct his Federal Public Key Infrastructure Policy Authority (FPKIPA) to revoke any and all Certificate Authorities that are engaged in supporting treasonous or seditious activity against the United States. This is a matter of grave national security that falls under the rubric of recent State of Emergency Executive Orders.
Specifically, any certificate authorities associated directly or through surrogates with Robert S. Mueller, III, James P. Chandler, III, James B. Comey, Michael Chertoff, Bill & Hillary Clinton, Jerry C. Jones, Joseph E. Sullivan, Orlando Bravo should be revoked immediately.
Regarding foreign election meddling, any Certificate Authority currently providing services to the state boards of elections that maintain encryption keys offshore should be immediately revoked.
As a part of this review, the President should evaluate the qualifications and loyalties of the members of the Federal Public Key Infrastructure Policy Authority (FPKIPA) which is comprised of members "appointed by each federal agency’s CIO, and the group operates under the authority of the Federal CIO Council" stay-behind corruptocrat Senior Executive Service (SES) members who are not loyal to our duly elected President Donald J. Trump. If he cannot fire them due to the convoluted and self-serving SES policies, then he should invoke the Holman Rule and reduce their salaries and benefits to $1.
Bookmark: #public-key-infrastructure-pki | https://tinyurl.com/y9r9d4xt| Click image to view this document. |
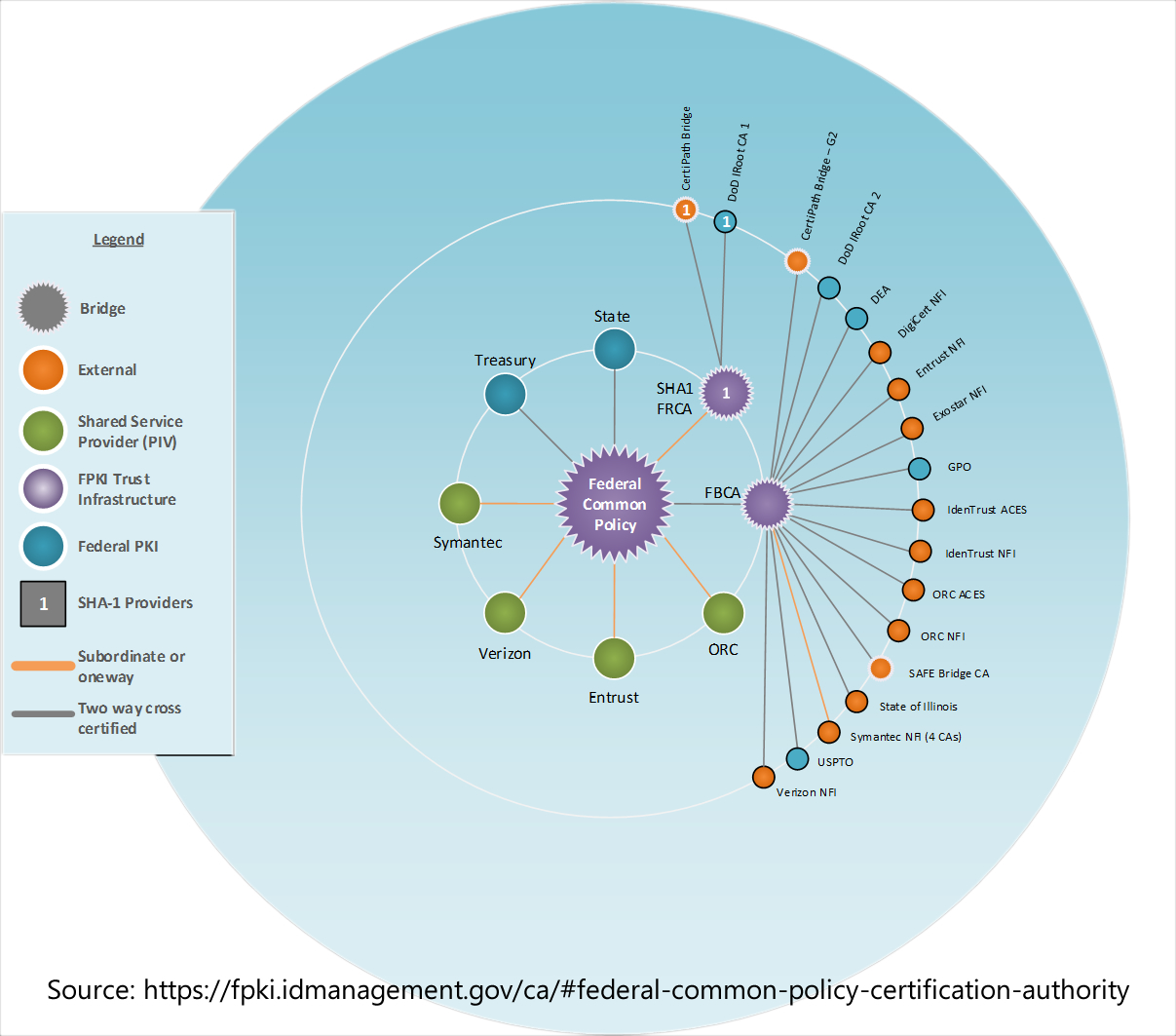 |
| Fig. 12—Certificate Authorities ILLUSTRATION. (Accessed Nov. 17, 2018). Federal Public Key Infrastructure Guides. CIO.gov, Idmanagement.gov, GSA. See also GSA.https://fpki.idmanagement.gov/ca/ and https://www.idmanagement.gov/fpkipa/ (PDF) |
Click image to view this interactive federal graph.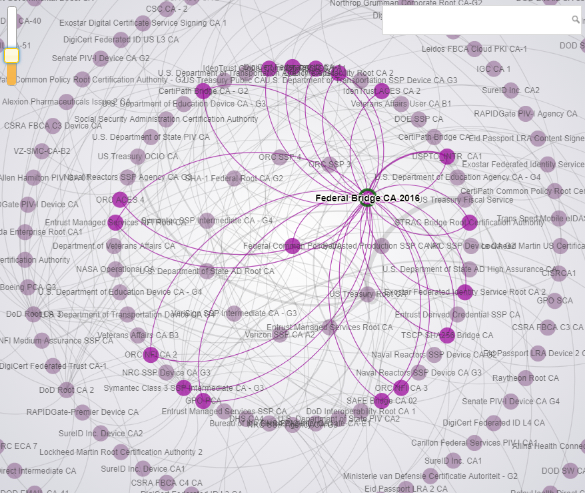 |
| Fig. 13—Federal PKI Graph. (Accessed Nov. 17, 2018). Federal PKI Graph. (Accessed Nov. 17, 2018). Federal PKI Graph, Federal Public Key Infrastructure Guides. CIO.gov. Idmanagement.gov. GSA. https://fpki.idmanagement.gov/tools/fpkigraph/ | PDF version. |
| American sovereignty is now Swiss Cheese—Come On In !— our encryption keys are for sale to the highest bidder ! |
Click image to view this document.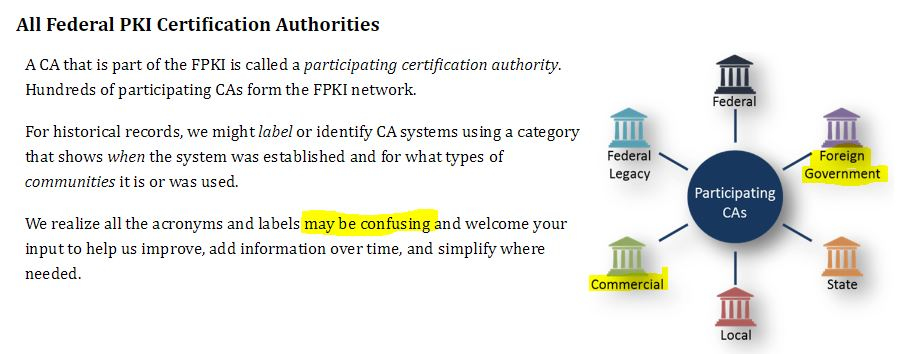 |
| Fig. 14—Certificate Authorities ILLUSTRATION#2, p.5. (Accessed Nov. 17, 2018). Federal Public Key Infrastructure Guides. CIO.gov, Idmanagement.gov, GSA. See also GSA.https://fpki.idmanagement.gov/ca/ and https://www.idmanagement.gov/fpkipa/; see also https://fpki.idmanagement.gov/tools/fpkigraph/ |
* * *
Return to return to the beginning of this post.

WTF??
ReplyDeleteInsanity is rampant.
DeleteMust be something in the water.
Fluoride?
Is their anyone telling the President any of this !!
ReplyDeleteIs anyone telling the President any of this, if not, he need's to clean up his house quick, and get rid of any Bush or OBUMA hold over's !! Thank's Rence Prebius !!POS
ReplyDeleteThank you for a most informative article. The ties that bind all these crooks at the top are almost unbelievable, your article explains very well how they have operated to control the narrative, and how they intended to exert absolute control over We the people. Thank heaven Crooked Hillary wasn't able to cheat her way into the presidency despite all their effort! I hope that President Trump will take action and send all these crooks where they belong.
ReplyDeleteSpeaking of encryption keys, don't overlook Microsoft being complicit in all this. When I was a DOD IT contractor in the late 90s, early 2000s, we used to joke about Microsoft's "Undocumented Features" (read software glitches) that we had to overcome in order to produce the desired "zero defects" product.
ReplyDeleteDear Readers. We are still updating the contents of this post, and have received an enormous number of comments already since last night. Please stay tuned. We'll get to them. Spread the truth in the meantime!
ReplyDeleteHere's the TinyURL for this post:
Deletehttps://tinyurl.com/y8cz4s8d
Please get this to President Trump. There was a "Sullivan" that he was thinking about to appoint to take Sessions place, after the temporary Whitaker. Cause I think it was said, that supposedly the law says that he can't name the Temporary to the Permanent spot. Even though Whitaker seems like a good fit.
DeleteI will do my part. This is exactly as stated. Way deeper than I ever thought. Great work!
DeleteSuddenly, all the bits and pieces start to make sense. With stakes so high, in this cryptic turf war, it is a wonder there has not been another catastrophic event like 911.I pray daily for our President to be surrounded by the right people who tell him the truth!
ReplyDeleteThanks for this information on the encryption keys and the link to the deep state. It must come to light.
ReplyDeletePlease send some extra cheesecake to all those AFI researchers. They are an amazing group of patriots!
ReplyDeleteIt's a shame you don't have a donate button! I'd without a doubt donate
ReplyDeleteto this fantastic blog! I suppose for now i'll settle for book-marking and adding your RSS feed to my Google account.
I look forward to fresh updates and will share this site with
my Facebook group. Chat soon!
Order the Marine Corps to arrest all these Traitors the Clinton's,Chandler,Mueller etc.Put them in Gitmo and convict them by Military Tribunal and execute them immediately for sedition,espionage and Treason.
ReplyDeletePlease, can you write a 2nd, briefly edited version without the more conservative-leaning words/bits so we can share/wake-up/'red-pill' more 'normies'/rest of the country to help unify people who would be more able to 'hear'/read such a great piece of information...?
ReplyDeleteMaybe add some 'neutral source' research links to verification/sourcing***
Many would love to share and could share more if certain receipients, who need it the most, could access this important information in a more neutral presentation.
I am on board with your presentation-style, myself, no problem, yet I do know so many who might be able to get there with a bit different presentation that they wouldn't immediately shut down with - just a few words...phrases edited... would help 'red-pill' more who really need this and might 'hear'...
Thank you so much for your great work and for considering this request for a bit more 'neutral' version!!
Dear Anonymous,
DeleteFeel free to recast this research in a way that Red Pills your constituents! Not sure what you mean about "neutral" research. We strive for "judicially recognizable" sources. Our core research comes from court records, Congressional records, Securities and Exchange Commission documents, State Department document, General Services Administration contract records, DoD records, CIA records, NASDAQ records, doctoral theses, published records, the subjects themselves, etc.`Sometimes we use the writings of third parties when their research is especially useful and on point. We'd love to read your "bit different presentation!" Go for it!
When we started this research, we had no preconceived conclusions. These conclusions have been drawn with the facts as they emerged from the mines. Consider that labels such as "conservative" and "neutral" are themselves pejorative, and it is better to just let the facts organize themselves. We strive to share them just as they speak to us, without skewing them toward any group. We do observe that the facts expose corruptocrats within each political label. If readers are more comfortable attempting to pigeonhole these facts as coming from one camp or another, that is, of course, their perogative, but such pigionholing may actually color the facts unnecessarily and slow down the Red Pilling. The facts are what they are! That said, we are very open to reading your version to learn more about your perspective and style approach! "Different strokes for different folks."
The AFI/AIM Conclave miners
P.S. When you are ready with your draft. Please notify us here or on AIM4TRUTH.org and we'll make contact with you to get your draft for posting!
Dear Anonymous:
DeleteWe are still waiting for your edits!
Please send them.
The Conclave
Email comment by TG:
ReplyDeleteStaff, Douglas Gabriel. (Nov. 19). CHEMTRAILS, EUGENICS/GENOCIDE, EXOTIC WEAPONS EYEWITNESS BARELY MAKES IT OUT ALIVE IN CALIFORNIA FIRE STORM. ForbiddenKnowledgeTV.net.
14 hours ago
Scenes of vaporized homes surrounded by unscathed trees are the hallmark of the devastating California fires we’ve seen, especially starting last year. Last October and last August, when there were massive wildfires in California, I reported on the pervasive pattern of dustified homes and cars, while nearby trees remained relatively unharmed and how some people were coming to the shocking conclusion that these eerie events were the result of Directed Energy Weapons (DEWs). As of last week’s California fires, the number of people thinking this has grown.
Scientific papers exist on the use of electrical fields for combustion synthesis in metals and there’s no doubt that focused microwaves or masers are used in DEWs. When you apply microwaves to metals, the oxygen released functions as an accelerant to feed a fire in what’s called “microwave-assisted combustion synthesis”. Significantly, you can’t do this with trees because there’s no metal in trees to create the oxidizing agent to fuel a self-sustaining fire.
Full story [VIDEO]:
https://forbiddenknowledgetv.net/eyewitness-barely-makes-it-out-alive-in-california-fire-storm/
Previous comment:
Deletehttps://tinyurl.com/ycayabuh
Spread the truth.
Email comment by Sharyl Attkisson:
ReplyDeleteSharyl Attkisson. (Nov. 17, 2018). THE COMPUTER INTRUSIONS: DISAPPEARING ACT. Full Measure.
The following is the third in a series of excerpts from my New York Times bestseller “Stonewalled,” which recounts the government intrusions of my computers. More excerpts to follow.
| DISAPPEARING ACT
In late December 2012, I take up my friend’s offer to have my computer examined by an inside professional. Arrangements are made for a meeting.
In the meantime, Jeff wants to check out the exterior of my home. To examine the outside connections for the Verizon FiOS line and see if anything looks out of order.
“If you’re being tapped, it’s probably not originating at your house, but I’d like to take a look anyway,” he says.
Read excerpt #1 here: The Computer Intrusions: Up at Night
Read excerpt #2 here: Big Brother: First Warnings
“Sure, why not.” I don’t think he’ll find anything but there’s no harm in having him look. Maybe I should be more concerned. What if the government is watching me? What if they’re trying to find out who my sources are and what I may be about to report next?
Full story:
https://sharylattkisson.com/2018/11/17/the-computer-intrusions-disappearing-act/
Previous comment:
Deletehttps://tinyurl.com/yayv6pf3
Spread the truth.
Email comment by GH:
ReplyDeleteGlenn Greenwald. (Nov. 16 2018). As the Obama DOJ Concluded, Prosecution of Julian Assange for Publishing Documents Poses Grave Threats to Press Freedom. The Intercept.
THE TRUMP JUSTICE DEPARTMENT inadvertently revealed in a court filing that it has charged Julian Assange in a sealed indictment. The disclosure occurred through a remarkably amateurish cutting-and-pasting error in which prosecutors unintentionally used secret language from Assange’s sealed charges in a document filed in an unrelated case. Although the document does not specify which charges have been filed against Assange, the Wall Street Journal reported that “they may involve the Espionage Act, which criminalizes the disclosure of national defense-related information.”
Full story:
https://theintercept.com/2018/11/16/as-the-obama-doj-concluded-prosecution-of-julian-assange-for-publishing-documents-poses-grave-threats-to-press-freedom/
Previous comment:
Deletehttps://tinyurl.com/y87ufmbu
Spread the truth.
Special Note: JAMES P. CHANDLER, III wrote the Economic Espionage Act of 1996 at the same time he revised The False Statements Accountability of 1996 where Congress approved lying to Congress and the courts by lawyers and litigants.
ReplyDeletehttp://www.fbcoverup.com/docs/cyberhijack/cyber-hijack-findings.html#economic-espionage-act
Email comment by GH:
ReplyDeleteTyler Duren. (Dec. 12, 2017). Ex-Spy Chief Admits Role In 'Deep State' Intelligence War On Trump. ZeroHedge.
An ex-spy chief who spoke out publicly against Trump while inspiring other career intelligence figures to follow suit has admitted his leading role in the intelligence community waging political war against the president, describing his actions as something he didn't "fully think through". In a surprisingly frank interview, the CIA's Michael Morell - who was longtime Deputy Director and former Acting Director of the nation's most powerful intelligence agency - said that it wasn't a great idea to leak against and bash a new president.
Morell had the dubious distinction of being George W. Bush's personal daily briefer for the agency before and after 9/11, and also served under Obama until his retirement. In the summer of 2016 he took the unusual step (for a former intelligence chief) of openly endorsing Hillary Clinton in a New York Times op-ed entitled, I Ran the C.I.A. Now I'm Endorsing Hillary Clinton, after which he continued to be both an outspoken critic of Trump and an early CIA voice promoting the Russian collusion and election meddling narrative.
Full story:
https://www.zerohedge.com/news/2017-12-11/ex-spy-chief-admits-role-deep-state-intelligence-war-trump
Previous comment:
Deletehttps://tinyurl.com/y8srhgo3
Spread the truth.
Pardon me, I was just daydreaming and imagined what would happen on Earth if “at Hillary” was substituted for “as hell” a la Howard Beale:
ReplyDeletehttps://www.youtube.com/watch?v=AS4aiA17YsM&feature=youtu.be&t=230
ps.st! What would the future hold if precisely at midnight (the s-witching hour) on New Year’s Eve a flash catharsis transpired?
GITMO PRACTICE!!!
ReplyDeletePress Release. (Nov. 29, 2018). Three Senior Executives at Defense Contracting Firms Charged with Scheme to Defraud the U.S. Military in Connection with $8 Billion Troop Supply Contract and with Violating the Iran Sanctions Regime. U.S. Department of Justice.
• https://www.fbcoverup.com/docs/library/2018-11-29-Three-Senior-Executives-at-Defense-Contracting-Firms-Charged-with-Scheme-to-Defraud-the-US-Military-Press-Release-Department-of-Justice-Nov-29-2018.pdf
• https://www.justice.gov/opa/pr/three-senior-executives-defense-contracting-firms-charged-scheme-defraud-us-military
• https://tinyurl.com/yc45h4xh
Good Video Overview:
Kip Simpson. (Nov. 30, 2018). Justice Department Charges Clinton, Obama, Feinstein Donor for $8 Billion Contract Fraud. YouTube.
• https://youtu.be/drNdbNrJ1a8
Indictment – aka PRACTICE!
• U.S. v. Faouki et al, INDICTMENT, 1:18-cr-00346-TNM (DCDC 2018), indictment filed Nov. 27, 2018
o https://www.fbcoverup.com/docs/library/US-v-Farouki-et-al-INDICTMENT-18-cr-00346-TNM-Trevor-N-McFadden-DCDC-filed-Nov-27-2018.pdf
• U.S. v. Faouki et al, DOCKET, 1:18-cr-00346-TNM (DCDC 2018), captured Dec. 02, 2018, indictment filed Nov. 27, 2018
o https://www.fbcoverup.com/docs/library/US-v-Farouki-et-al-DOCKET-18-cr-00346-TNM-Trevor-N-McFadden-DCDC-filed-Nov-27-2018.pdf
Previous comment (thanks to DL)
Deletehttps://tinyurl.com/ycz5gnls
Spread the truth.